Reduce Data Theft with Microsoft Purview Insider Risk Management
- Blog
- Compliance
- Post

Through Microsoft Purview Insider risk management in Microsoft 365, organizations can identify and mitigate insider risks quickly and effectively. Before you can manage and minimize risks in your organization, though, it is critical to understand the different types of internal risks you may encounter. This article will explore how Microsoft Purview Insider Risk Management can help to prevent data theft and data leak of sensitive information within an organization.
The modern workplace allows users to create, manage, and share data via various platforms and services. With employees having access to all of these platforms, identifying and mitigating organization-wide risks while meeting compliance requirements has become increasingly difficult for organizations, especially when they have a limited set of resources and tools to do so.
Organizations also cannot directly control certain risks that may arise from user behavior or events within the company. Users can behave in an unethical, inappropriate, or illegal manner within your organization, and employee departures and accidental or malicious data leaks can also be hugely problematic. However, Microsoft Purview Insider Risk Management can really help to mitigate these internal risks.
What is Microsoft Purview Insider Risk Management?
Microsoft Purview Insider Risk Management comes with Microsoft 365 E5, and it’s also available in the Microsoft 365 E5 Compliance add-on. Microsoft Purview is actually the new name of Azure Purview, the data governance solution that the company made generally available back in September 2021.
Microsoft Purview leverages the Microsoft Graph to obtain real-time signals across Office, Windows, and Azure, including file activity and abnormal user behaviors. Additional third-party signals from HR systems and desktop agents can also be included via an API-level integration.
Using Microsoft 365 and Microsoft Graph logs, you can define insider risk policies to address the types of risks your organization wants to identify. By monitoring those risks, you can take appropriate action and, if necessary, escalate cases to Microsoft eDiscovery (Premium).
The insider risk policies you can create will allow you to identify risky activities and mitigate them accordingly. Compliance analysts will then be able to quickly take appropriate actions and ensure that users follow your organization’s compliance policies.
Overview of the Microsoft Purview Insider risk management dashboard
The Insider risk management dashboard on Microsoft Purview displays an overview of alerts waiting for your review, active cases, users, and policies that have seen the most activity. There’s also a guided experience for onboarding tenants which provides a step-by-step tutorial on how to use the solution. Other tabs include Alerts, Cases, Policies, Users, and Notice templates.
The Top Actions To Get You Started section provides you with both required and optional steps to help you implement insider risk management. Clicking on the Add allowed and unallowed domains action allows us to view details about the recommendations and navigate directly to the appropriate location to implement them.
Next, let’s examine some of the detected activities. When you click on Alerts, a list of risk types based on alerts appears. Under Alerts, you can view basic statistics and how alerts have trended over time.
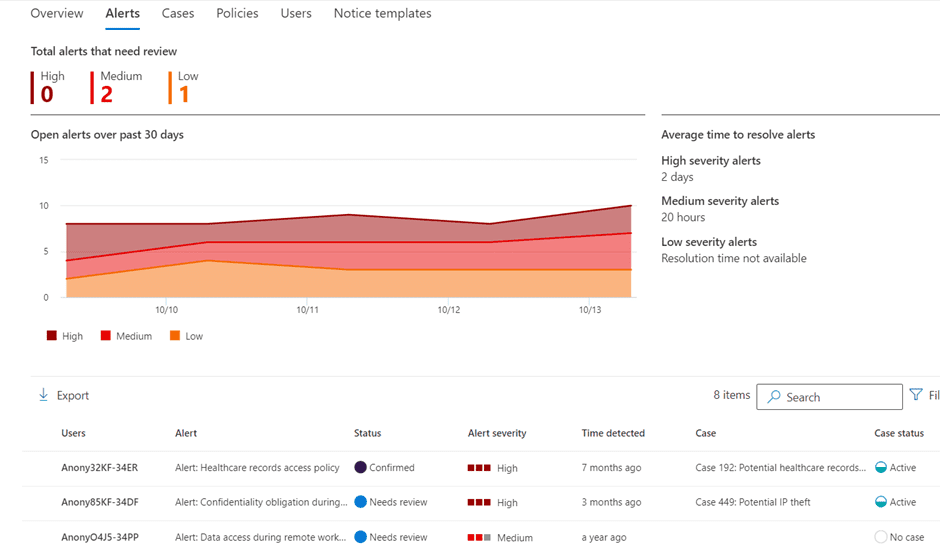
The names of users on the list are pseudo-anonymized by default to prevent conflicts of interest, protect privacy, and ensure that you do not overlook a relative, friend, or boss by mistake. If the pseudonymize option is disabled, the “Users” tab will display information from Azure AD including the user’s full name, e-mail address, title, department, and manager name.
By default, this toggle is only off for users with the highest level of permissions for Insider rights management, which is usually limited to the legal or compliance departments of most organizations. If the user interface shows anonymized user information, the original user information is still stored in the backend if you need to investigate an issue.
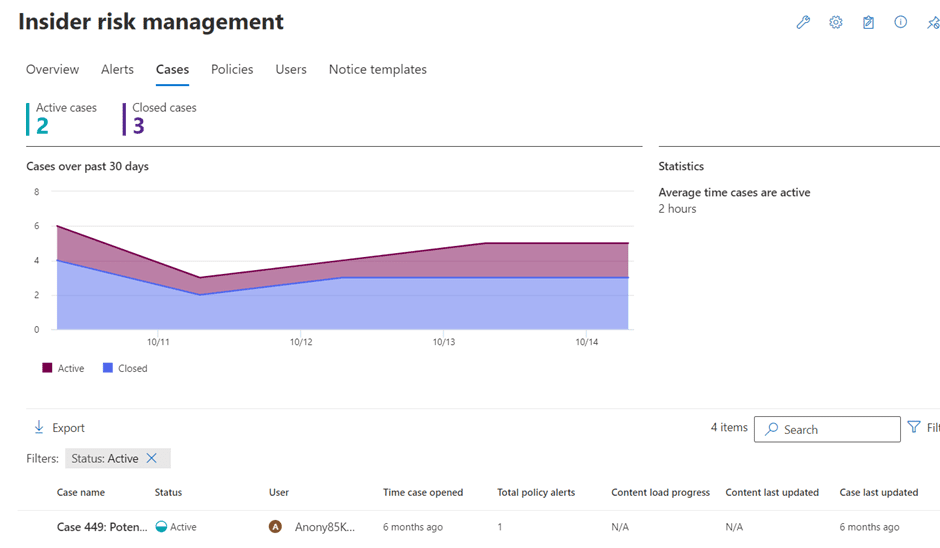
On the Cases page, you will find information about the cases as well as statistics and statuses for those cases.
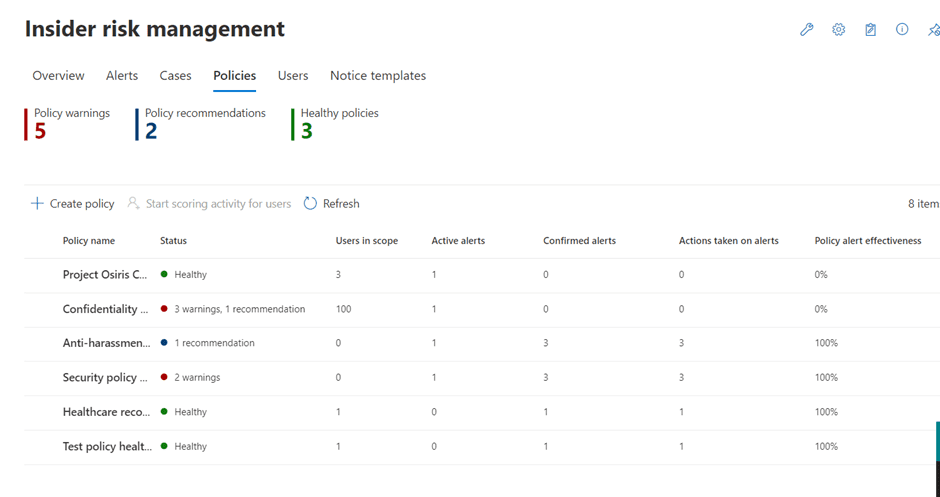
The Policies tab lists the policy violations and the current policies in place.
Additionally, we can configure standard notice templates to communicate clearly and consistently with users about activities that violate company policies.
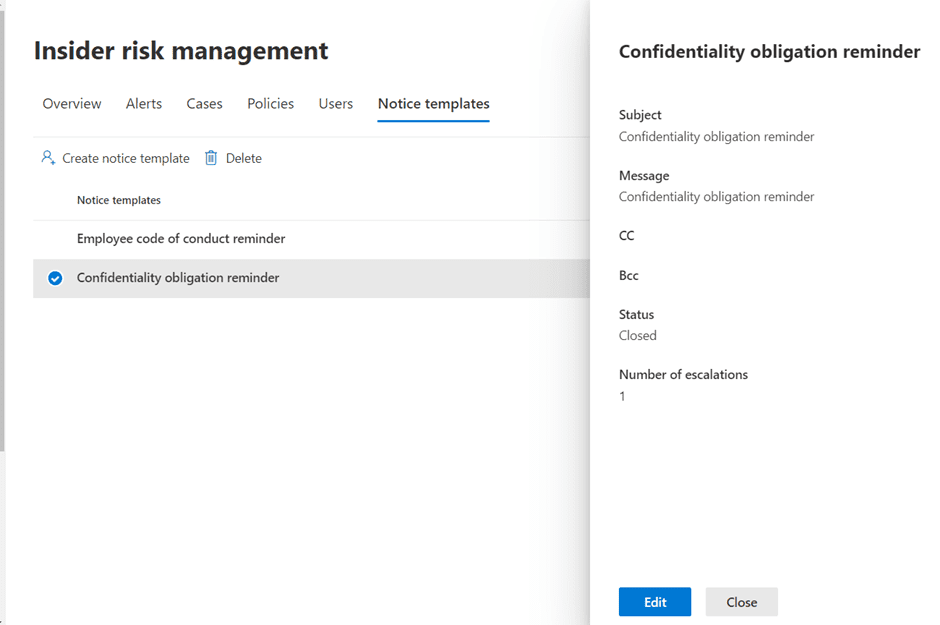
Creating a new insider risk policy
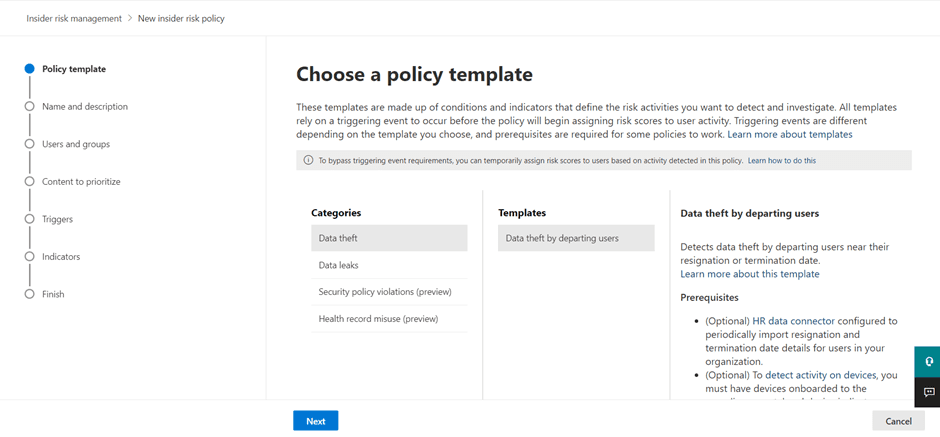
To manage risks of data theft and data leakage in your organization, the first step you need to take is to create a new insider risk policy so that you can start reviewing content and set up alerts that will be triggered automatically. Start by choosing a policy template from one of the four categories between Data theft, data leaks, Security policy violations (preview), and Health record misuse (preview).
The four different templates contain preconfigured detections targeted at specific insider risk types. When you have selected the policy template, you can name it and describe it.
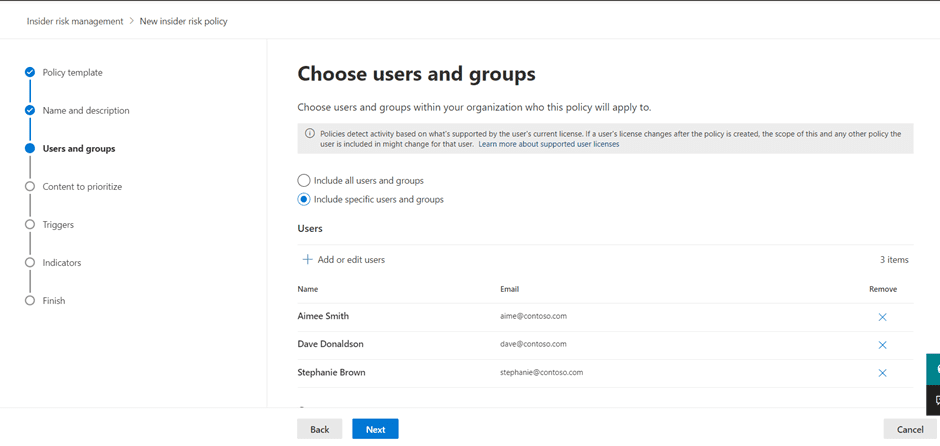
On the Users and groups page, you can choose to apply your new policy to either specific users and groups in the tenant or all users. Given the privacy implications at stake, Microsoft has developed this experience as an explicit opt-in experience, meaning you have to add users for a given policy.
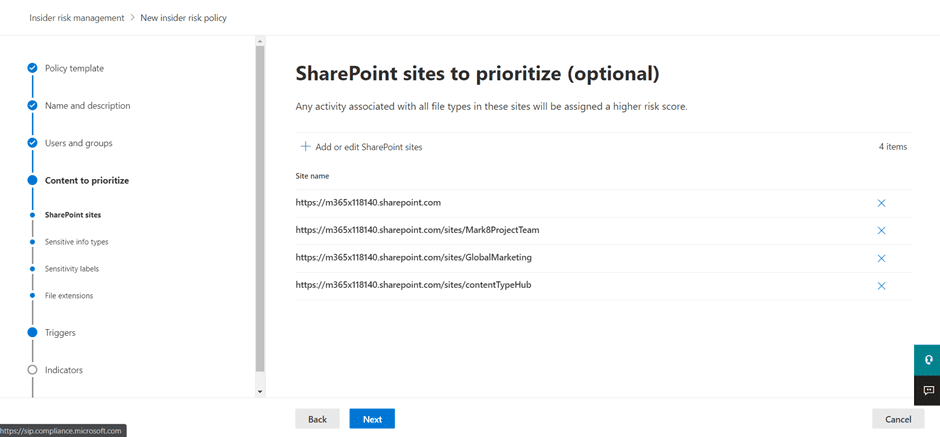
Because not all content is created equal, the next step is to determine content priority. As an example, if you’re creating a policy for a sales team while knowing that the most critical sales documents are in a specific SharePoint site, you can define that SharePoint site as a content priority for the given policy.
You can also select sensitive information types such as credit card numbers, banking information, or sensitive labels. You can use those additional settings to prioritize the critical content for this policy.
Next, you can select relevant policy indicators to trigger alerts. The built-in indicators include Office indicators, device indicators, and physical access indicators. The more indicators selected, the richer the policy matches will be. During this step, we can also configure additional indicators by using an HR connector to collect signals from other corporate systems.
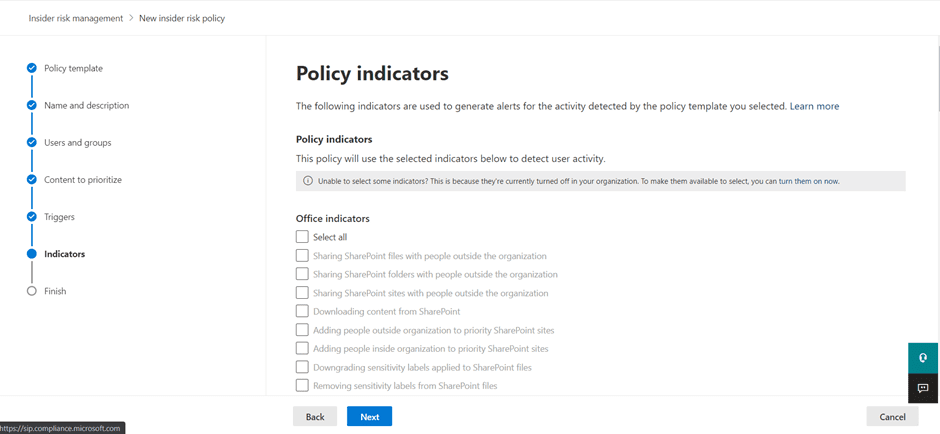
Once submitted, these policy, scope, and alert indicators will start generating alerts to review suspicious activities. Depending on your environment and user activity, it could take a couple of days before you start receiving your first alerts.
Investigating a user
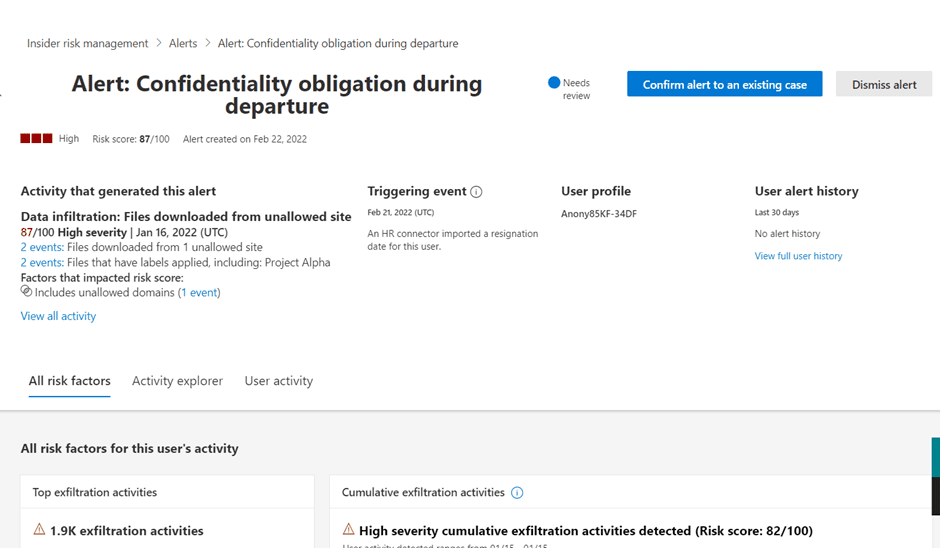
Let’s return to Alerts and begin investigating an activity that generated an alert. As you can see below, the alert is titled ‘Confidentiality obligation during departure’ and it’s been triggered by an anonymous user profile (User Anony85KF-34DF).
On the Summary tab, you can scroll through the information and see details about the user and activity that generated the alert and review some of the content that’s been detected. The information about activities that generated the alert can include files downloaded from confidential sites, access to health records, a large file deletion, etc.
In the User Activity tab, you see a curated timeline of activity or insights for that user. Across the bottom x-axis is time and across the left y-axis is the risk level. The alerts displayed on this graph include activities such as copying, downloading, and printing files. You can view the same curated timeline displayed on the alert down below.
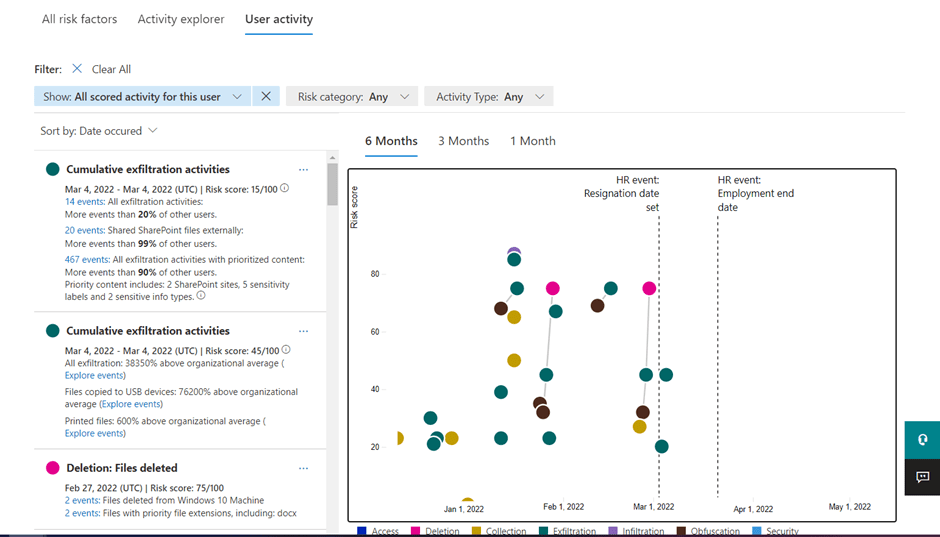
The timeline on the left of the User activity page shows a chronological view of the different events. Each circle corresponds to one or more sets of insights on the graph. We also see annotations on the graph that show when the user put in his resignation and when they are to leave the company. This exploration of user activity is critical to making timely and informed risk management decisions.
Another important issue you need to take into account when creating your insider risk policy is the ability to track repeat offenders. It’s usually a good practice to assume positive intent, and if you see a policy violation, you may drive education or training – maybe even twice. However, if there’s a pattern of behavior, then the course of action you take for remediation should increase severity.
Managing a case
Cases help you organize information about a user’s activity history to determine if they have multiple policy violations or a pattern of risky behavior. You can collect information about users from the Activity and Content explorer views where you’ll find a place to add notes and contributors to the case.
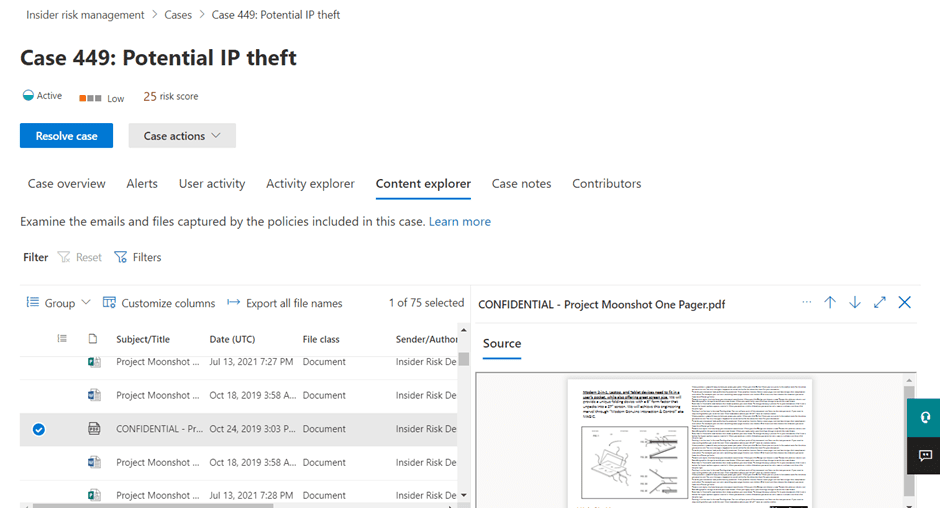
If activities such as corporate files being copied to a USB device were detected in the case, you could end up with an accidental or unintentional insider threat on your hands if that USB device and the files on it are not appropriately handled. You could make a quick note of this in the “Case Notes” and send this individual a friendly email notice about confidentiality obligations.
In the Case Notes tab, you can find the Send e-mail notice option under the Case actions drop-down menu.
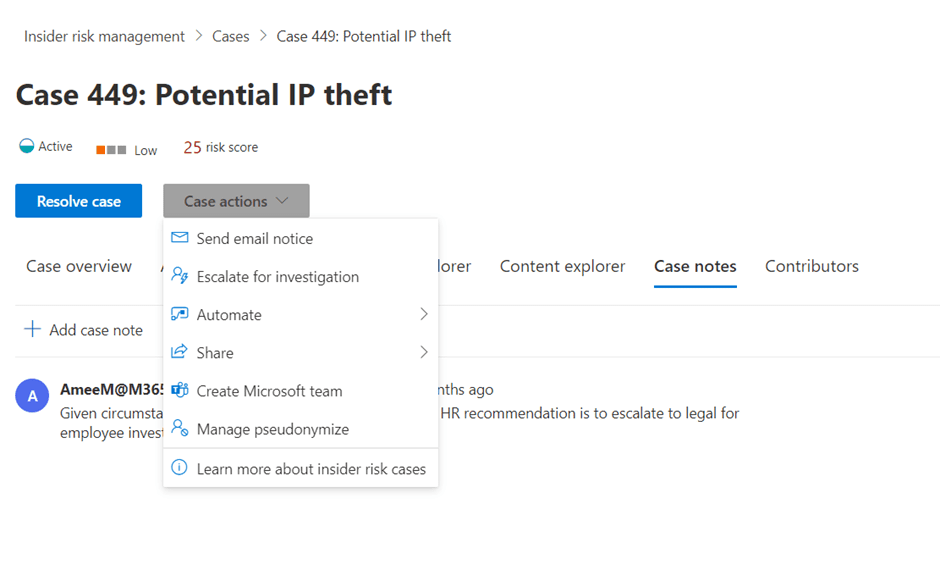
Before sending your email notice, you need to choose the correct template. You can even cc the individual’s manager as an FYI.
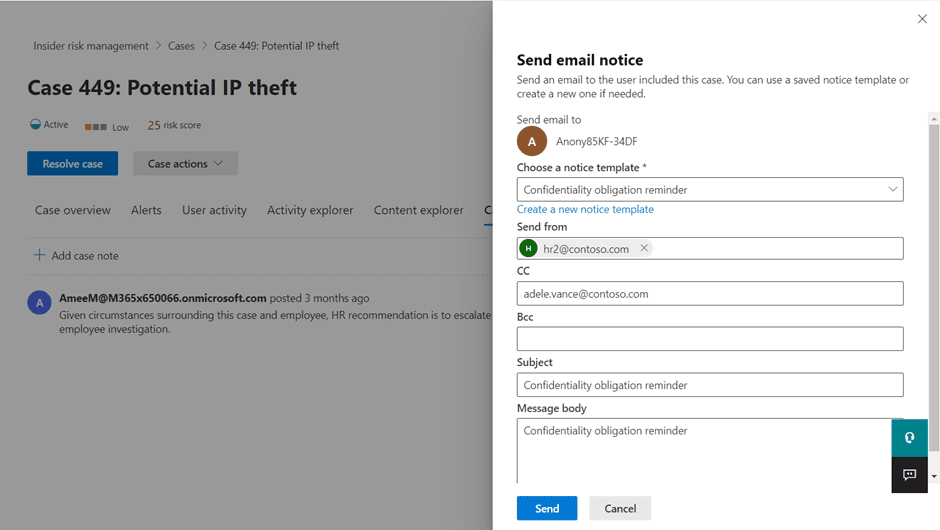
This is a good example of a situation where instead of opening up a formal investigation, you’re assuming positive intent and using the available information to make a timely and informed decision. Insider risk management isn’t just about finding the real insider threat, it’s about quantifying the risk and taking the necessary actions to mitigate it.
Escalating a case
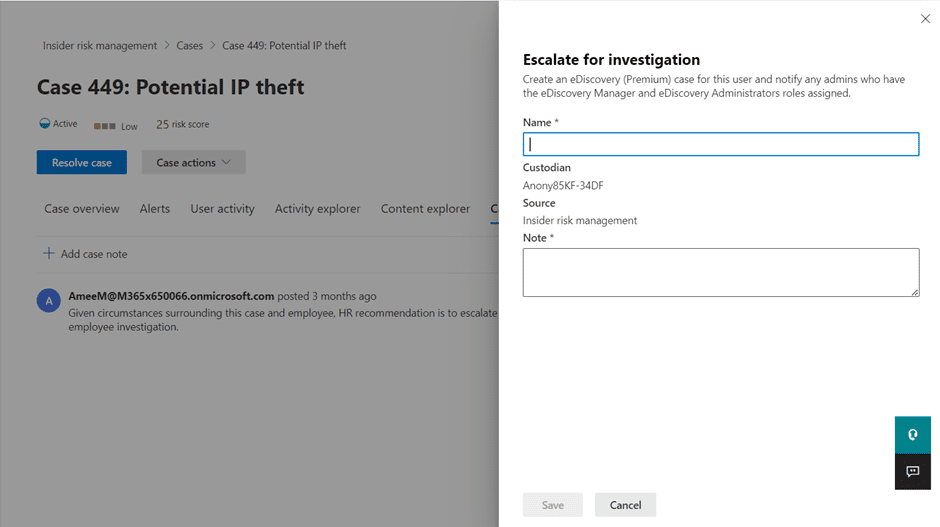
Suppose your investigation revealed a user with repeated policy violations and previous warnings. In that case, you could use the Case actions button to escalate the case for investigation, which will automatically package evidence captured so far to send this to your legal team for review as an advanced eDiscovery case.
Summary
Data theft and data leaks are serious risks businesses must manage these days, but Microsoft Purview Insider Risk Management provides a curated and easy-to-understand visual summary of individual risks within an organization. This view includes a historical timeline of all activities and trends associated with each identified threat, and end-to-end integrated workflows ensure that the right people across Security, HR, Legal, and Compliance can quickly investigate and take appropriate actions.
Insider risk management is a critical component of any security strategy, and it’s essential to take steps to reduce the chances of data theft or leakage. By implementing proper security measures and monitoring employee activity, businesses can protect themselves from the damaging effects of data loss.



