Microsoft Releases September 2023 Patch Tuesday Updates for Windows 11 and Windows 10

Key takeaways
- The September 2023 Patch Tuesday updates fix a total of 65 vulnerabilities, including two security flaws already being exploited by attackers.
- A new “Enable Optional Updates” policy gives IT pros more granular controls over optional updates and Controlled Feature Rollouts (CFRs) on Windows 11 PCs.
- Microsoft fixed an authentication issue when using a smart card to join or rejoin a computer to an Active Directory domain might fail.
Microsoft released the September 2023 Patch Tuesday updates for Windows 11 and Windows 10 yesterday. The monthly updates were quite easy to miss yesterday as Apple’s iPhone 15 event pretty much dominated the news cycle, but there’s actually quite a lot to discuss this month.
This month, Microsoft fixed a total of 65 vulnerabilities in Windows, Exchange, Office, and other components, with two security flaws already being used by attackers. On Windows 11 version 22H2, Microsoft is also adding a new “Enable optional updates” policy that gives IT admins more control over optional Windows updates, including what Microsoft calls Controlled Feature Rollouts (CFRs).
September 2023 Patch Tuesday Updates fix 65 vulnerabilities
As pointed out by the Zero Day Initiative, the two security flaws that are already being exploited by attackers include a Microsoft Word vulnerability and an elevation of privilege vulnerability affecting the Microsoft Streaming Service Proxy. Additionally, there are five critical vulnerabilities affecting Internet Connection Sharing (ICS), the Microsoft Azure Kubernetes Service, and Visual Studio.
Here is what you should know about these CVEs:
- CVE-2023-36761: This Microsoft Word Information Disclosure Vulnerability uses the Preview Pane as an attack vector, and Microsoft said that exploiting this vulnerability could allow the disclosure of NTLM hashes.
- CVE-2023-36802: This Microsoft Streaming Service Proxy Elevation of Privilege Vulnerability could allow attackers who successfully exploited it to gain SYSTEM privileges.
- CVE-2023-38148: This Internet Connection Sharing (ICS) Remote Code Execution Vulnerability can be exploited by an unauthorized attacker sending a specially crafted network packet to the Internet Connection Sharing (ICS) Service (if it’s enabled). Microsoft noted that attacks would still be limited to systems connected to the same network segment as the attacker.
- CVE-2023-29332: This Microsoft Azure Kubernetes Service Elevation of Privilege Vulnerability can be exploited from the Internet to gain Cluster Administrator privileges.
- CVE-2023-36792, CVE-2023-36793, and CVE-2023-36796: These 3 Visual Studio Remote Code Execution Vulnerabilities require an attacker to convince users to open a maliciously crafted package file in Visual Studio.
You can find the full list of CVEs for September 2023 below:
| Product | Impact | Max Severity | Article | Download | Details |
| Microsoft Edge (Chromium-based) | Release Notes | Security Update | CVE-2023-4863 | ||
| Microsoft .NET Framework 3.5 AND 4.8 | Remote Code Execution | Important | 5030186 | Security Update | CVE-2023-36794 |
| Microsoft .NET Framework 3.5 AND 4.8 | Remote Code Execution | Important | 5030178 | Security Update | CVE-2023-36794 |
| Microsoft .NET Framework 3.5.1 | Remote Code Execution | Important | 5030182 | Monthly Rollup | CVE-2023-36794 |
| Microsoft .NET Framework 3.5 | Remote Code Execution | Important | 5030184 | Monthly Rollup | CVE-2023-36794 |
| Microsoft .NET Framework 3.5 | Remote Code Execution | Important | 5030183 | Monthly Rollup | CVE-2023-36794 |
| Microsoft .NET Framework 3.0 Service Pack 2 | Remote Code Execution | Important | 5030185 | Monthly Rollup | CVE-2023-36794 |
| Microsoft .NET Framework 2.0 Service Pack 2 | Remote Code Execution | Important | 5030185 | Monthly Rollup | CVE-2023-36794 |
| Microsoft .NET Framework 4.6.2 | Remote Code Execution | Important | 5030185 | Monthly Rollup | CVE-2023-36794 |
| Microsoft .NET Framework 3.5 AND 4.8.1 | Remote Code Execution | Important | 5030180 | Security Update | CVE-2023-36794 |
| Microsoft .NET Framework 3.5 AND 4.8.1 | Remote Code Execution | Important | 5029921 | Security Update | CVE-2023-36794 |
| Microsoft .NET Framework 3.5 AND 4.8.1 | Remote Code Execution | Important | 5030179 | Security Update | CVE-2023-36794 |
| Microsoft .NET Framework 3.5 AND 4.8.1 | Remote Code Execution | Important | 5030181 | Security Update | CVE-2023-36794 |
| Microsoft .NET Framework 3.5 AND 4.8.1 | Remote Code Execution | Important | 5030186 | Security Update | CVE-2023-36794 |
| Microsoft .NET Framework 4.6.2/4.7/4.7.1/4.7.2 | Remote Code Execution | Important | 5030184 | Monthly Rollup | CVE-2023-36794 |
| Microsoft .NET Framework 4.6.2/4.7/4.7.1/4.7.2 | Remote Code Execution | Important | 5030183 | Monthly Rollup | CVE-2023-36794 |
| Microsoft .NET Framework 4.6.2/4.7/4.7.1/4.7.2 | Remote Code Execution | Important | 5030182 | Monthly Rollup | CVE-2023-36794 |
| Microsoft .NET Framework 4.8 | Remote Code Execution | Important | 5030184 | Monthly Rollup | CVE-2023-36794 |
| Microsoft .NET Framework 4.8 | Remote Code Execution | Important | 5030183 | Monthly Rollup | CVE-2023-36794 |
| Microsoft .NET Framework 4.8 | Remote Code Execution | Important | 5030182 | Monthly Rollup | CVE-2023-36794 |
| Microsoft .NET Framework 3.5 AND 4.8 | Remote Code Execution | Important | 5030180 | Security Update | CVE-2023-36794 |
| Microsoft .NET Framework 3.5 AND 4.7.2 | Remote Code Execution | Important | 5030178 | Security Update | CVE-2023-36794 |
| Microsoft .NET Framework 3.5 AND 4.8 | Remote Code Execution | Important | 5030179 | Security Update | CVE-2023-36794 |
| Microsoft .NET Framework 3.5 AND 4.8 | Remote Code Execution | Important | 5030181 | Security Update | CVE-2023-36794 |
| Microsoft .NET Framework 4.8 | Remote Code Execution | Important | 5029924 | Security Update | CVE-2023-36794 |
| Microsoft Office 2013 Service Pack 1 (64-bit editions) | Spoofing | Moderate | 5002477 | Security Update | CVE-2023-41764 |
| Microsoft Office 2013 Service Pack 1 (32-bit editions) | Spoofing | Moderate | 5002477 | Security Update | CVE-2023-41764 |
| Microsoft Office 2013 RT Service Pack 1 | Spoofing | Moderate | 5002477 | Security Update | CVE-2023-41764 |
| Microsoft Office 2016 (64-bit edition) | Spoofing | Moderate | 5002457 | Security Update | CVE-2023-41764 |
| Microsoft Office 2016 (64-bit edition) | Spoofing | Moderate | 5002498 | Security Update | CVE-2023-41764 |
| Microsoft Office 2016 (64-bit edition) | Spoofing | Moderate | 5002100 | Security Update | CVE-2023-41764 |
| Microsoft Office 2016 (32-bit edition) | Spoofing | Moderate | 5002457 | Security Update | CVE-2023-41764 |
| Microsoft Office 2016 (32-bit edition) | Spoofing | Moderate | 5002498 | Security Update | CVE-2023-41764 |
| Microsoft Office 2016 (32-bit edition) | Spoofing | Moderate | 5002100 | Security Update | CVE-2023-41764 |
| Microsoft Office LTSC 2021 for 32-bit editions | Spoofing | Moderate | Click to Run | Security Update | CVE-2023-41764 |
| Microsoft Office LTSC 2021 for 64-bit editions | Spoofing | Moderate | Click to Run | Security Update | CVE-2023-41764 |
| Microsoft 365 Apps for Enterprise for 64-bit Systems | Spoofing | Moderate | Click to Run | Security Update | CVE-2023-41764 |
| Microsoft 365 Apps for Enterprise for 32-bit Systems | Spoofing | Moderate | Click to Run | Security Update | CVE-2023-41764 |
| Microsoft Office 2019 for 64-bit editions | Spoofing | Moderate | Click to Run | Security Update | CVE-2023-41764 |
| Microsoft Office 2019 for 32-bit editions | Spoofing | Moderate | Click to Run | Security Update | CVE-2023-41764 |
| Microsoft Identity Linux Broker | Remote Code Execution | Important | Information | Security Update | CVE-2023-36736 |
| Microsoft Visual Studio 2022 version 17.7 | Remote Code Execution | Important | Release Notes | Security Update | CVE-2023-36792 |
| Microsoft Visual Studio 2022 version 17.6 | Remote Code Execution | Critical | Release Notes | Security Update | CVE-2023-36793 |
| Microsoft Dynamics 365 (on-premises) version 9.0 | Spoofing | Important | 5029396 | Security Update | CVE-2023-38164 |
| Microsoft Dynamics 365 (on-premises) version 9.1 | Spoofing | Important | 5030608 | Security Update | CVE-2023-38164 |
| 3D Viewer | Remote Code Execution | Important | Release Notes | Security Update | CVE-2022-41303 |
| Visual Studio Code | Remote Code Execution | Important | Release Notes | Security Update | CVE-2023-39956 |
| Microsoft Visual Studio 2022 version 17.4 | Denial of Service | Important | Release Notes | Security Update | CVE-2023-36799 |
| Microsoft Visual Studio 2022 version 17.2 | Denial of Service | Important | Release Notes | Security Update | CVE-2023-36799 |
| Azure HDInsights | Elevation of Privilege | Important | Release Notes | Security Update | CVE-2023-38156 |
| .NET 7.0 | Remote Code Execution | Important | 5030560 | Security Update | CVE-2023-36794 |
| .NET 6.0 | Remote Code Execution | Important | 5030559 | Security Update | CVE-2023-36794 |
| Dynamics 365 for Finance and Operations | Spoofing | Important | Release Notes | Security Update | CVE-2023-36800 |
| Microsoft Excel 2013 Service Pack 1 (64-bit editions) | Information Disclosure | Important | 5002488 | Security Update | CVE-2023-36766 |
| Microsoft Excel 2013 Service Pack 1 (32-bit editions) | Information Disclosure | Important | 5002488 | Security Update | CVE-2023-36766 |
| Microsoft Excel 2013 RT Service Pack 1 | Information Disclosure | Important | 5002488 | Security Update | CVE-2023-36766 |
| Microsoft Excel 2016 (64-bit edition) | Information Disclosure | Important | 5002496 | Security Update | CVE-2023-36766 |
| Microsoft Excel 2016 (32-bit edition) | Information Disclosure | Important | 5002496 | Security Update | CVE-2023-36766 |
| Microsoft Office LTSC for Mac 2021 | Information Disclosure | Important | Release Notes | Security Update | CVE-2023-36766 |
| Microsoft Office Online Server | Information Disclosure | Important | 5002470 | Security Update | CVE-2023-36766 |
| Microsoft Office 2019 for Mac | Information Disclosure | Important | Release Notes | Security Update | CVE-2023-36766 |
| 3D Builder | Remote Code Execution | Important | Release Notes | Security Update | CVE-2023-36772 |
| Microsoft Visual Studio 2019 version 16.11 (includes 16.0 – 16.10) | Remote Code Execution | Critical | Release Notes | Security Update | CVE-2023-36796 |
| Microsoft Visual Studio 2017 version 15.9 (includes 15.0 – 15.8) | Remote Code Execution | Critical | Release Notes | Security Update | CVE-2023-36796 |
| Windows Server 2016 (Server Core installation) | Information Disclosure | Important | 5030213 | Security Update | CVE-2023-36803 |
| Windows Server 2016 | Information Disclosure | Important | 5030213 | Security Update | CVE-2023-36803 |
| Windows 10 Version 1607 for x64-based Systems | Information Disclosure | Important | 5030213 | Security Update | CVE-2023-36803 |
| Windows 10 Version 1607 for 32-bit Systems | Information Disclosure | Important | 5030213 | Security Update | CVE-2023-36803 |
| Windows 10 Version 22H2 for 32-bit Systems | Information Disclosure | Important | 5030211 | Security Update | CVE-2023-36803 |
| Windows 10 Version 22H2 for ARM64-based Systems | Information Disclosure | Important | 5030211 | Security Update | CVE-2023-36803 |
| Windows 10 Version 22H2 for x64-based Systems | Information Disclosure | Important | 5030211 | Security Update | CVE-2023-36803 |
| Windows 11 Version 22H2 for x64-based Systems | Information Disclosure | Important | 5030219 | Security Update | CVE-2023-36803 |
| Windows 11 Version 22H2 for ARM64-based Systems | Information Disclosure | Important | 5030219 | Security Update | CVE-2023-36803 |
| Windows 10 Version 21H2 for x64-based Systems | Information Disclosure | Important | 5030211 | Security Update | CVE-2023-36803 |
| Windows 10 Version 21H2 for ARM64-based Systems | Information Disclosure | Important | 5030211 | Security Update | CVE-2023-36803 |
| Windows 10 Version 21H2 for 32-bit Systems | Information Disclosure | Important | 5030211 | Security Update | CVE-2023-36803 |
| Windows 11 version 21H2 for ARM64-based Systems | Information Disclosure | Important | 5030217 | Security Update | CVE-2023-36803 |
| Windows 11 version 21H2 for x64-based Systems | Information Disclosure | Important | 5030217 | Security Update | CVE-2023-36803 |
| Windows Server 2022 (Server Core installation) | Information Disclosure | Important | 5030216 | Security Update | CVE-2023-36803 |
| Windows Server 2022 (Server Core installation) | Information Disclosure | Important | 5030325 | AzureHotpatch | CVE-2023-36803 |
| Windows Server 2022 | Information Disclosure | Important | 5030216 | Security Update | CVE-2023-36803 |
| Windows Server 2022 | Information Disclosure | Important | 5030325 | AzureHotpatch | CVE-2023-36803 |
| Windows Server 2019 (Server Core installation) | Information Disclosure | Important | 5030214 | Security Update | CVE-2023-36803 |
| Windows Server 2019 | Information Disclosure | Important | 5030214 | Security Update | CVE-2023-36803 |
| Windows 10 Version 1809 for ARM64-based Systems | Information Disclosure | Important | 5030214 | Security Update | CVE-2023-36803 |
| Windows 10 Version 1809 for x64-based Systems | Information Disclosure | Important | 5030214 | Security Update | CVE-2023-36803 |
| Windows 10 Version 1809 for 32-bit Systems | Information Disclosure | Important | 5030214 | Security Update | CVE-2023-36803 |
| Windows Server 2012 R2 (Server Core installation) | Elevation of Privilege | Important | 5030269 | Monthly Rollup | CVE-2023-38142 |
| Windows Server 2012 R2 (Server Core installation) | Elevation of Privilege | Important | 5030287 | Security Only | CVE-2023-38142 |
| Windows Server 2012 R2 | Elevation of Privilege | Important | 5030269 | Monthly Rollup | CVE-2023-38142 |
| Windows Server 2012 R2 | Elevation of Privilege | Important | 5030287 | Security Only | CVE-2023-38142 |
| Windows Server 2012 (Server Core installation) | Elevation of Privilege | Important | 5030278 | Monthly Rollup | CVE-2023-38142 |
| Windows Server 2012 (Server Core installation) | Elevation of Privilege | Important | 5030279 | Security Only | CVE-2023-38142 |
| Windows Server 2012 | Elevation of Privilege | Important | 5030278 | Monthly Rollup | CVE-2023-38142 |
| Windows Server 2012 | Elevation of Privilege | Important | 5030279 | Security Only | CVE-2023-38142 |
| Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) | Elevation of Privilege | Important | 5030265 | Monthly Rollup | CVE-2023-38142 |
| Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) | Elevation of Privilege | Important | 5030261 | Security Only | CVE-2023-38142 |
| Windows Server 2008 R2 for x64-based Systems Service Pack 1 | Elevation of Privilege | Important | 5030265 | Monthly Rollup | CVE-2023-38142 |
| Windows Server 2008 R2 for x64-based Systems Service Pack 1 | Elevation of Privilege | Important | 5030261 | Security Only | CVE-2023-38142 |
| Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation) | Elevation of Privilege | Important | 5030271 | Monthly Rollup | CVE-2023-38142 |
| Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation) | Elevation of Privilege | Important | 5030286 | Security Only | CVE-2023-38142 |
| Windows Server 2008 for x64-based Systems Service Pack 2 | Elevation of Privilege | Important | 5030271 | Monthly Rollup | CVE-2023-38142 |
| Windows Server 2008 for x64-based Systems Service Pack 2 | Elevation of Privilege | Important | 5030286 | Security Only | CVE-2023-38142 |
| Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation) | Elevation of Privilege | Important | 5030271 | Monthly Rollup | CVE-2023-38142 |
| Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation) | Elevation of Privilege | Important | 5030286 | Security Only | CVE-2023-38142 |
| Windows Server 2008 for 32-bit Systems Service Pack 2 | Elevation of Privilege | Important | 5030271 | Monthly Rollup | CVE-2023-38142 |
| Windows Server 2008 for 32-bit Systems Service Pack 2 | Elevation of Privilege | Important | 5030286 | Security Only | CVE-2023-38142 |
| Windows 10 for x64-based Systems | Elevation of Privilege | Important | 5030220 | Security Update | CVE-2023-38142 |
| Windows 10 for 32-bit Systems | Elevation of Privilege | Important | 5030220 | Security Update | CVE-2023-38142 |
| Microsoft Defender Security Intelligence Updates | Security Feature Bypass | Important | Release Notes | Security Update | CVE-2023-38163 |
| Azure Kubernetes Service | Elevation of Privilege | Critical | Release Notes | Security Update | CVE-2023-29332 |
| Azure DevOps Server 2020.0.2 | Elevation of Privilege | Important | Release Notes | Security Update | CVE-2023-38155 |
| Azure DevOps Server 2019.1.2 | Elevation of Privilege | Important | Release Notes | Security Update | CVE-2023-38155 |
| Azure DevOps Server 2020.1.2 | Elevation of Privilege | Important | Release Notes | Security Update | CVE-2023-38155 |
| Azure DevOps Server 2022.0.1 | Elevation of Privilege | Important | Release Notes | Security Update | CVE-2023-38155 |
| Azure DevOps Server 2019.0.1 | Remote Code Execution | Important | Release Notes | Security Update | CVE-2023-33136 |
| Microsoft Exchange Server 2016 Cumulative Update 23 | Remote Code Execution | Important | 5030524 | Security Update | CVE-2023-36745 |
| Microsoft Exchange Server 2019 Cumulative Update 12 | Remote Code Execution | Important | 5030524 | Security Update | CVE-2023-36745 |
| Microsoft Exchange Server 2019 Cumulative Update 13 | Remote Code Execution | Important | 5030524 | Security Update | CVE-2023-36745 |
| Microsoft Word 2013 Service Pack 1 (64-bit editions) | Information Disclosure | Important | 5002483 | Security Update | CVE-2023-36761 |
| Microsoft Word 2013 Service Pack 1 (32-bit editions) | Information Disclosure | Important | 5002483 | Security Update | CVE-2023-36761 |
| Microsoft Word 2013 RT Service Pack 1 | Information Disclosure | Important | 5002483 | Security Update | CVE-2023-36761 |
| Microsoft Word 2016 (64-bit edition) | Information Disclosure | Important | 5002497 | Security Update | CVE-2023-36761 |
| Microsoft Word 2016 (32-bit edition) | Information Disclosure | Important | 5002497 | Security Update | CVE-2023-36761 |
| Microsoft SharePoint Enterprise Server 2016 | Remote Code Execution | Important | 5002494 | Security Update | CVE-2023-36762 |
| Microsoft SharePoint Enterprise Server 2016 | Remote Code Execution | Important | 5002501 | Security Update | CVE-2023-36762 |
| Microsoft Outlook 2016 (64-bit edition) | Information Disclosure | Important | 5002499 | Security Update | CVE-2023-36763 |
| Microsoft Outlook 2016 (32-bit edition) | Information Disclosure | Important | 5002499 | Security Update | CVE-2023-36763 |
| Microsoft SharePoint Server Subscription Edition | Elevation of Privilege | Important | 5002474 | Security Update | CVE-2023-36764 |
| Microsoft SharePoint Server 2019 | Elevation of Privilege | Important | 5002472 | Security Update | CVE-2023-36764 |
| Windows Server 2012 R2 (Server Core installation) | Security Feature Bypass | Important | 5030209 | IE Cumulative | CVE-2023-36805 |
| Windows Server 2012 R2 | Security Feature Bypass | Important | 5030209 | IE Cumulative | CVE-2023-36805 |
Quality and experience updates
The Patch Tuesday update for Windows 11 version 22H2 (KB5030219) addresses an authentication issue when using a smart card to join or rejoin a computer to an Active Directory domain might fail. This authentication bug has also been fixed in the monthly updates for Windows 11 version 21H2 (KB5030217) as well as Windows 10 version 22H2 (KB5030211).
On Windows 11 version 22H2, the KB5030219 update also adds a new search flyout box when you hover your mouse over the search box in the taskbar, but it can be disabled in Settings. This update also introduces changes to app defaults: Apps can now redirect users to the Settings page where they can configure the default app to open a specific file type. Moreover, apps can leverage a new API to allow users to pin either primary or secondary tiles to their taskbar.
The biggest change for IT pros, however, is a new policy called “Enable optional updates.” When enabled, IT admins can get 3 different options regarding Windows updates on managed devices:
- Automatically receive optional updates (including CFRs)
- Automatically receive optional updates (without CFRs)
- Users can select which optional updates to receive.
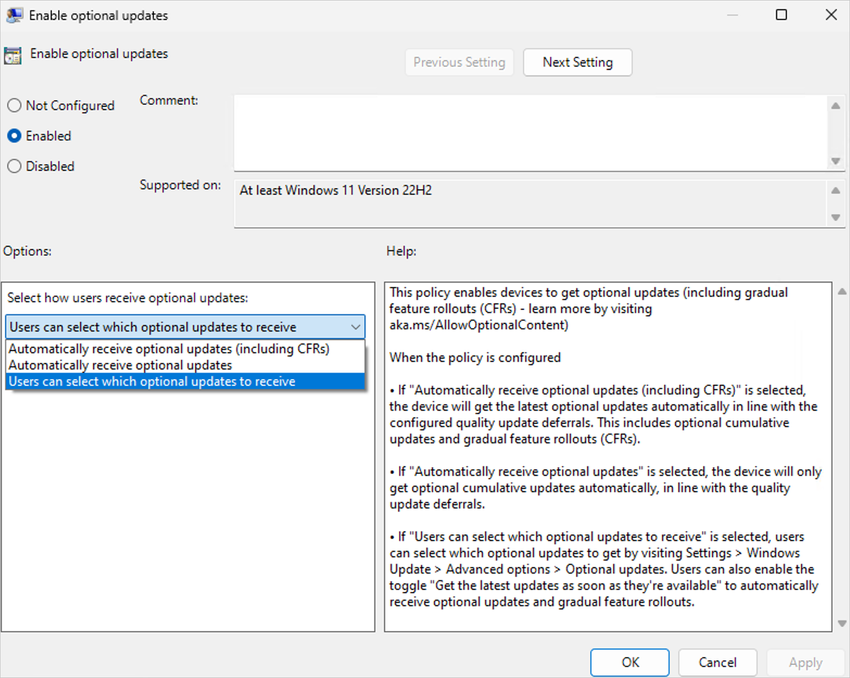
The last option allows users to enable the “Get the latest updates as soon as they’re available” setting in Windows Update to automatically receive optional Windows updates and controlled featured rollouts. These CFRs include new Windows 11 features that Microsoft releases throughout the year, and we have a recent example with the “Moment 3” features that started rolling out in late May.
We should now be getting closer to the release of Windows 11 version 23H2, the next annual update for Windows 11 that will be released as an enablement package. The update is currently being tested with Insiders on the Beta channel, and unfortunately, it looks like the new version of File Explorer is still quite buggy.
Anyway, Windows 11 version 23H2 should land on the Release Preview channel very soon. Microsoft will also be holding a special event on September 21, and we may get more details about the public rollout of Windows 11 version 23H2 on this occasion.
Windows Update testing and best practices
Organizations looking to deploy this month’s patches should conduct thorough testing before deploying them widely on production systems. That said, applying the patches widely shouldn’t be delayed longer than necessary as hackers start to work out how to weaponize newly reported vulnerabilities.
A best practice is to make sure you have backed up systems before applying updates. Every month, users experience issues with Windows updates that lead to systems not booting, application and hardware compatibility issues, or even data loss in extreme cases.
There are backup tools built into Windows and Windows Server that you can use to restore systems in the event a patch causes a problem. The backup features in Windows can be used to restore an entire system, or files and folders on a granular basis.
If you have any problems with this month’s patches, please let us know in the comments below. Other readers might be able to share their experiences in how to roll back problematic updates or mitigate issues caused by patches that are important to have in place.



