PowerShell Remoting: How to Restrict User Commands
- Blog
- PowerShell
- Post
How can I restrict the commands users can run when using PowerShell Remoting?
In my previous article, “How to Lock Down a Remote PowerShell with a Constrained Endpoint?,” I described how you can create a new remote PowerShell endpoint that doesn’t require users to have local administrator rights on the remote machine, therefore limiting the actions that can be performed over the remote session to what is allowed by the permissions assigned to the user connecting to the endpoint. Many administrators see remote PowerShell as a security risk, but it’s not necessary for users to have local administrator permissions on the target device.
In this article, I want to show you how to restrict an endpoint even further by limiting the commands that users can run when connecting to a remote device using PowerShell. To achieve this, you need a script that configures the session each time a user connects. While this sounds like it might be complicated, PowerShell 3.0 makes it easy to create the script through a handy cmdlet.
Create a Session Configuration File
In this example, I’m going to limit the session to the PowerShell Active Directory module and go even further by allowing users to run only the Get-ADUser and Unlock-ADAccount cmdlets. The following cmdlet will create a session configuration file (helpdesk.pssc), that I can use when registering a new endpoint.
- Log on to the server where you want to configure the PowerShell remote endpoint.
- Right-click the blue PowerShell icon on the desktop taskbar and select Run as Administrator from the menu.
- In the PowerShell console window, type the following command and press ENTER.
New-PSSessionConfigurationFile –ModulesToImport ActiveDirectory –VisibleCmdLets (‘Get-ADUser’, ‘Unlock-ADAccount’) –LanguageMode ‘NoLanguage’ –SessionType ‘RestrictedRemoteServer’ –Path ‘c:\helpdesk.pssc’
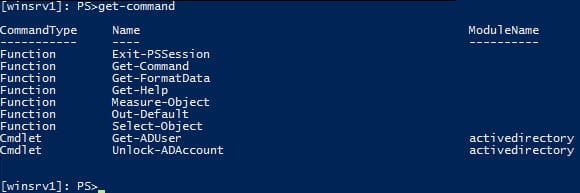
The LanguageMode parameter in the above command is set to NoLanguage, which restricts the user to running cmdlets and functions. Script blocks, variables, and operators will be barred. The RestrictedRemoteServer session type includes Exit-PSSession, Get-Command, Get-FormatData, Get-Help, Measure-Object, Out-Default, and Select-Object functions in the session configuration, but nothing else unless additionally specified.
Create a Constrained Endpoint with Your Session Configuration File
Now that we have our session configuration file (helpdesk.pssc) saved to the local disk, we can create a remote endpoint on the device that restricts users to running just the Get-ADUser and Unlock-ADAccount cmdlets. In the PowerShell console window, run the following command:
Register-PSSessionConfiguration –Name ‘HelpDesk’ -ShowSecurityDescriptorUI –Path ‘c:\helpdesk.pssc’
Confirm each configuration step by typing Y and pressing ENTER. A new window will appear allowing you to set permissions using the GUI.
Connect to the Endpoint and Check What Commands Are Accessible to the User
To test your endpoint, you can connect to it from either a remote machine or on the server where the endpoint is configured. In the PowerShell console, run the following command to connect, replacing <servername> with the name of the server where the endpoint is configured:
Enter-PSSession -ComputerName <servername> -ConfigurationName ‘HelpDesk’
Now type get-command in the PowerShell console and press ENTER. You should see that only the Get-ADUser and Unlock-ADAccount cmdlets are available to run. To exit the remote session, type exit-pssession and press ENTER.