
Key Takeaways:
- Octo Tempest, a hacking group, is actively targeting organizations with data extortion and ransomware attacks, posing a significant cybersecurity threat.
- Microsoft has unveiled Octo Tempest’s tactics, including SMS phishing and advanced social engineering, to infiltrate corporate networks, highlighting the need for robust security measures.
- Microsoft recommends the implementation of FIDO-compliant multi-factor authentication alongside additional security measures.
Microsoft has recently published details about a hacking group dubbed Octo Tempest that uses advanced social engineering techniques, SIM swapping, and occasional physical threats to target organizations. Their activities have raised alarms and prompted Microsoft to release recommendations for organizations to strengthen their defenses against this emerging threat.
According to the Microsoft Incident Response and Threat Intelligence team, the threat actor first started targeting telecom and business process outsourcing companies with SIM-swapping attacks in early 2022. The group sold the data to let other cybercriminals gain unauthorized access to accounts and steal cryptocurrency. In the second phase, the hackers began targeting telecom companies as well as email and tech service providers with data extortion attacks.
Earlier this year, the Octo Tempest hacking group joined forces with the ALPHV/BlackCat ransomware. Their latest campaign aims to compromise both Windows and Linux systems, with a particular emphasis on VMWare ESXi servers. It targeted various industries such as technology, hospitality, manufacturing, law, retail, natural resources, consumer products, gaming, and financial services.
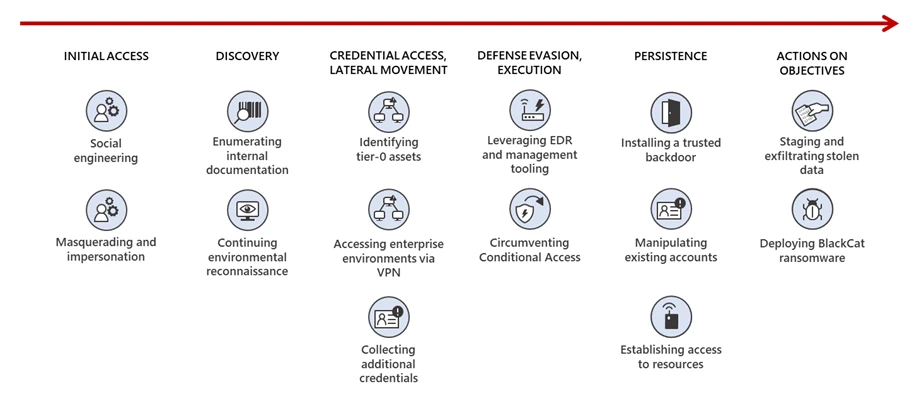
“In recent campaigns, we observed Octo Tempest leverage a diverse array of TTPs to navigate complex hybrid environments, exfiltrate sensitive data, and encrypt data,” Microsoft explained. “Octo Tempest leverages tradecraft that many organizations don’t have in their typical threat models, such as SMS phishing, SIM swapping, and advanced social engineering techniques.”
According to Microsoft, Octo Tempest uses social engineering methods to infiltrate corporate networks. The attackers focus on employees, especially those with access to network permissions, such as help desk personnel and support staff. They persuade the victims to download legitimate remote monitoring tools, which can then be used to steal credentials and multifactor authentication (MFA) session cookies.
After gaining initial access, the group convinces the victim to share corporate credentials and details about the company, including remote access methods, password policies, and employee onboarding processes. The hackers also attempt to gain access to server infrastructure, code repositories, and multi-cloud environments in order to launch subsequent attacks.
Recommendations to block Octo Tempest attacks
In response to the Octo Tempest ransomware attacks, Microsoft has recently published a set of recommendations to help organizations boost their defenses against these types of cyber threats. It’s advised to implement Microsoft Entra Privileged Identity Management (PIM) and FIDO-compliant multifactor authentication methods. Companies need to hold training sessions for their employees to raise awareness about emerging security threats.
Microsoft urges enterprise customers to use out-of-band communications when interacting with their colleagues. It’s also recommended to use security tools (such as Microsoft Sentinel) to detect AitM phishing attempts.


