
Key Takeaways:
- Microsoft is prioritizing security to protect its infrastructure and customers from cyber threats, expanding its Secure Future Initiative (SFI) to reinforce defenses.
- Microsoft’s security approach encompasses six key pillars, including measures like multifactor authentication, network isolation, and enhanced threat detection, aiming to address vulnerabilities across its systems and processes.
- Microsoft is instituting measures to hold senior leadership accountable for security goals.
Microsoft has announced plans to make security its top priority to better protect its infrastructure and customers against sophisticated cyberattacks. The company has recently detailed in a blog post that it’s expanding the Secure Future Initiative (SFI) to ensure robust protection measures.
Last year, Microsoft announced its Secure Future Initiative (SFI) to boost the built-in security of its products and services. It’s aimed at tackling software and vulnerability issues exploited by cybercriminals in recent high-profile security breaches.
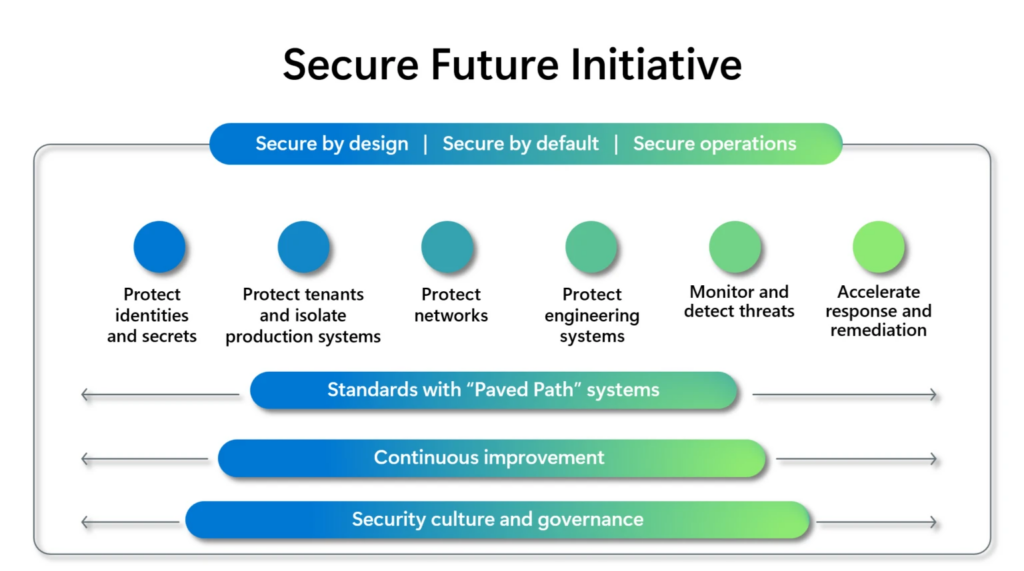
As part of the SFI, Microsoft outlined several plans and changes to its security practices, with some already put into action. The company explained that this expanded SFI approach will be driven by three security principles: Secure by design, Secure by default, and Secure operations.
“Microsoft plays a central role in the world’s digital ecosystem, and this comes with a critical responsibility to earn and maintain trust,” said Charlie Bell, Executive Vice President for Microsoft Security. “We’re expanding the scope of SFI, integrating the recent recommendations from the CSRB as well as our learnings from Midnight Blizzard to ensure that our cybersecurity approach remains robust and adaptive to the evolving threat landscape.”
Microsoft evolves its Secure Future Initiative approach
Microsoft detailed the following six actionable security pillars to address vulnerabilities in its systems and development processes:
- Protect identities and secrets: Microsoft plans to use phishing-resistant multifactor authentication methods to protect 100 percent of user accounts, applications, and identity tokens against unauthorized access.
- Isolate production systems: Microsoft will also implement strict controls aimed at isolating and safeguarding production environments in order to reduce the likelihood of security breaches.
- Enhance network security: Microsoft will utilize isolation and micro-segmentation techniques to enhance the protection of production networks. This strategy will add an extra layer of security for both customer and Microsoft resources.
- Secure engineering systems: Microsoft plans to strengthen the governance of software supply chains and engineering infrastructures via Zero Trust and least-privilege access policies.
- Accelerate response and remediation: Microsoft will adopt the Common Weakness Enumeration (CWE) and Common Platform Enumeration (CPE) industry standards to mitigate critical security vulnerabilities.
- Enhanced detection and monitoring: Microsoft will use advanced threat detection and monitoring capabilities to quickly detect and respond to potential security incidents. The company also intends to retain all system security logs for at minimum two years, while customers will have access to six months of relevant logs.
Microsoft highlighted that it has already enabled automatic multifactor authentication by default in Microsoft Entra ID tenants. The company has also expanded its security logging and removed 730,000 insecure apps deployed across production and corporate tenants.
Lastly, Microsoft noted that the pay of its senior leadership will be directly tied to reaching the internal security plans and milestones. The company will also hold monthly and weekly meetings with engineering teams and senior leaders to review progress and ensure alignment with security objectives.


