How to List All Users in Active Directory

This article will offer you two straightforward ways to list and export all Active Directory users in your environment. I’ll show you how to do that using the graphical user interface (GUI) and the Active Directory Users and Computers applications, and I’ll also explain how you can narrow down the list using various filters available in PowerShell.
How to list all users in Active Directory using the GUI
There are several methods you, as an IT pro, can use the Active Directory Users and Computers (ADUC) application to find all your user accounts in Active Directory. Let me first start with some simple searches to find user accounts.
The different ‘UserAccountControl‘ types
One important aspect to keep in mind is the dizzying number of ‘UserAccountControl‘ types. Here is a table that shows all the available types.
| Property flag | Value in hexadecimal | Value in decimal |
|---|---|---|
| SCRIPT | 0x0001 | 1 |
| ACCOUNTDISABLE | 0x0002 | 2 |
| HOMEDIR_REQUIRED | 0x0008 | 8 |
| LOCKOUT | 0x0010 | 16 |
| PASSWD_NOTREQD | 0x0020 | 32 |
| PASSWD_CANT_CHANGE You can’t assign this permission by directly modifying the UserAccountControl attribute. For information about how to set the permission programmatically, see the Property flag descriptions section. | 0x0040 | 64 |
| ENCRYPTED_TEXT_PWD_ALLOWED | 0x0080 | 128 |
| TEMP_DUPLICATE_ACCOUNT | 0x0100 | 256 |
| NORMAL_ACCOUNT | 0x0200 | 512 |
| INTERDOMAIN_TRUST_ACCOUNT | 0x0800 | 2048 |
| WORKSTATION_TRUST_ACCOUNT | 0x1000 | 4096 |
| SERVER_TRUST_ACCOUNT | 0x2000 | 8192 |
| DONT_EXPIRE_PASSWORD | 0x10000 | 65536 |
| MNS_LOGON_ACCOUNT | 0x20000 | 131072 |
| SMARTCARD_REQUIRED | 0x40000 | 262144 |
| TRUSTED_FOR_DELEGATION | 0x80000 | 524288 |
| NOT_DELEGATED | 0x100000 | 1048576 |
| USE_DES_KEY_ONLY | 0x200000 | 2097152 |
| DONT_REQ_PREAUTH | 0x400000 | 4194304 |
| PASSWORD_EXPIRED | 0x800000 | 8388608 |
| TRUSTED_TO_AUTH_FOR_DELEGATION | 0x1000000 | 16777216 |
| PARTIAL_SECRETS_ACCOUNT | 0x04000000 | 67108864 |
As account attributes are modified, these values get assigned to the user account itself. You can use the adsiedit.msc snap-in if you want to view these. But, let’s do some searches now.
Searching for Active Directory user accounts in ADUC
- Open Active Directory Users and Computers from Administrative Tools.
- Right-click on the domain root (reinders.local) and click Find…
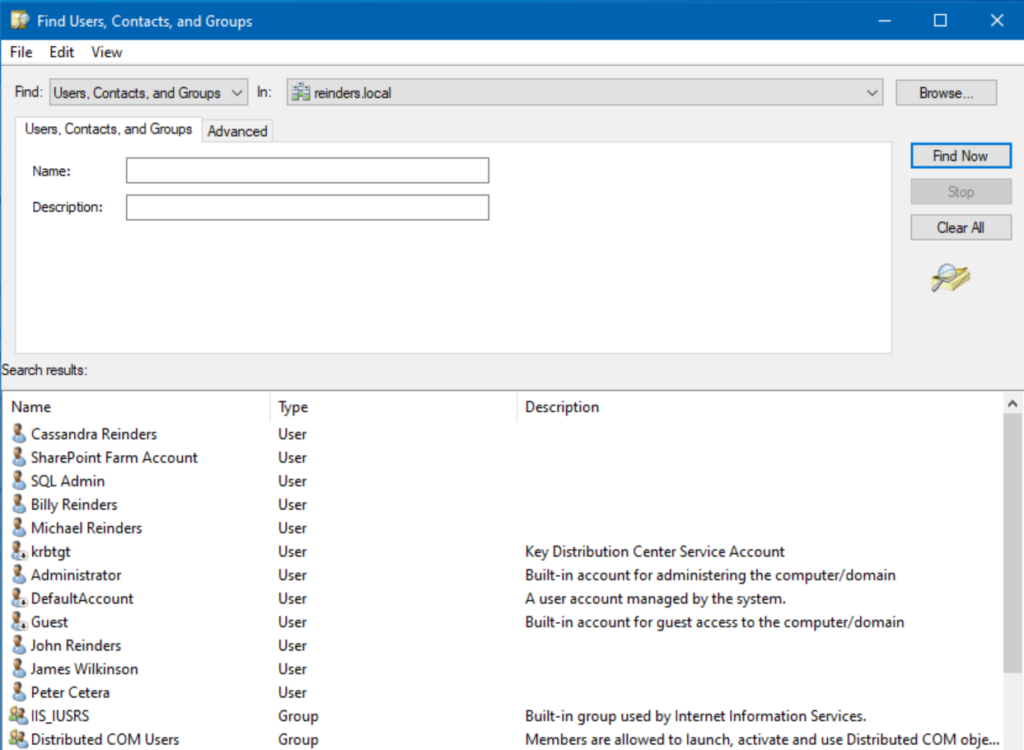
- Click Find Now and then sort the ‘Type‘ column until ‘User‘ is displayed. You will then see all your true user accounts.
Using the Saved Queries feature in ADUC
Next, let’s use the very helpful ‘Saved Queries‘ feature in ADUC:
- Right-click on Saved Queries above your domain root object in the tree and click New -> Query.
- Type in a Name and Description. Then, click Define Query…
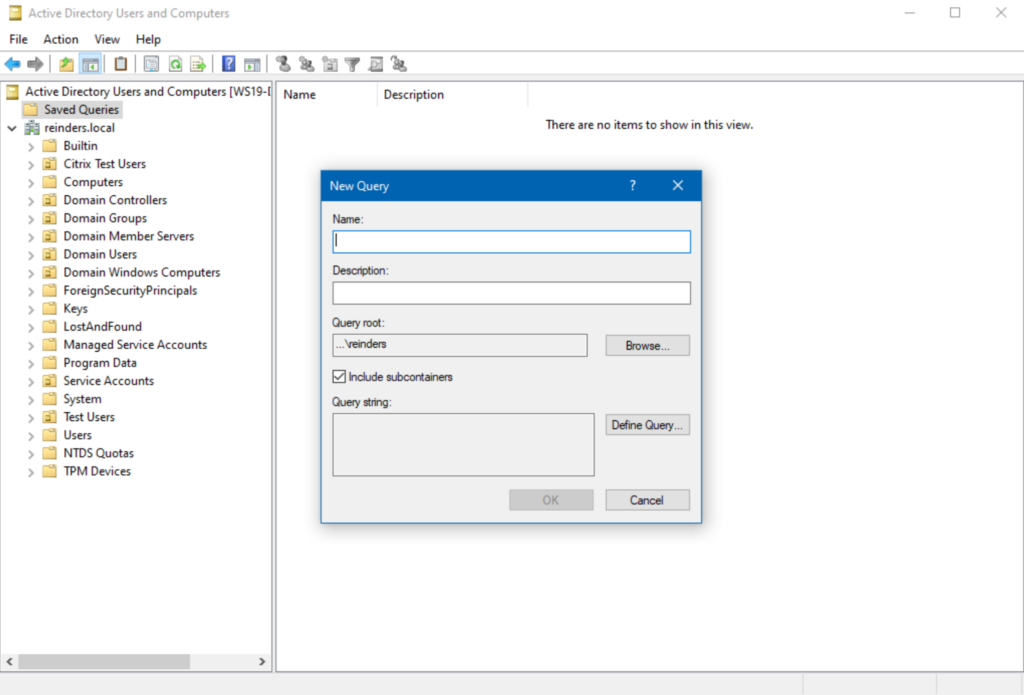
- In the ‘Name:’ field, choose ‘Has a value.’
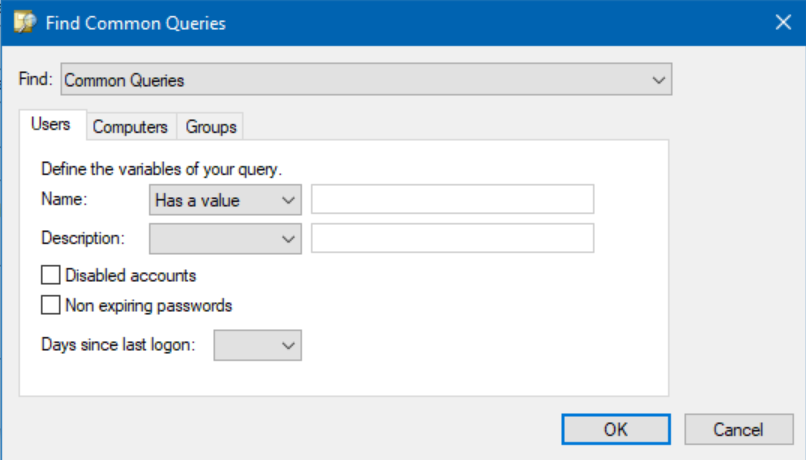
- Click OK and click OK a second time. Here is the result of our query definition.
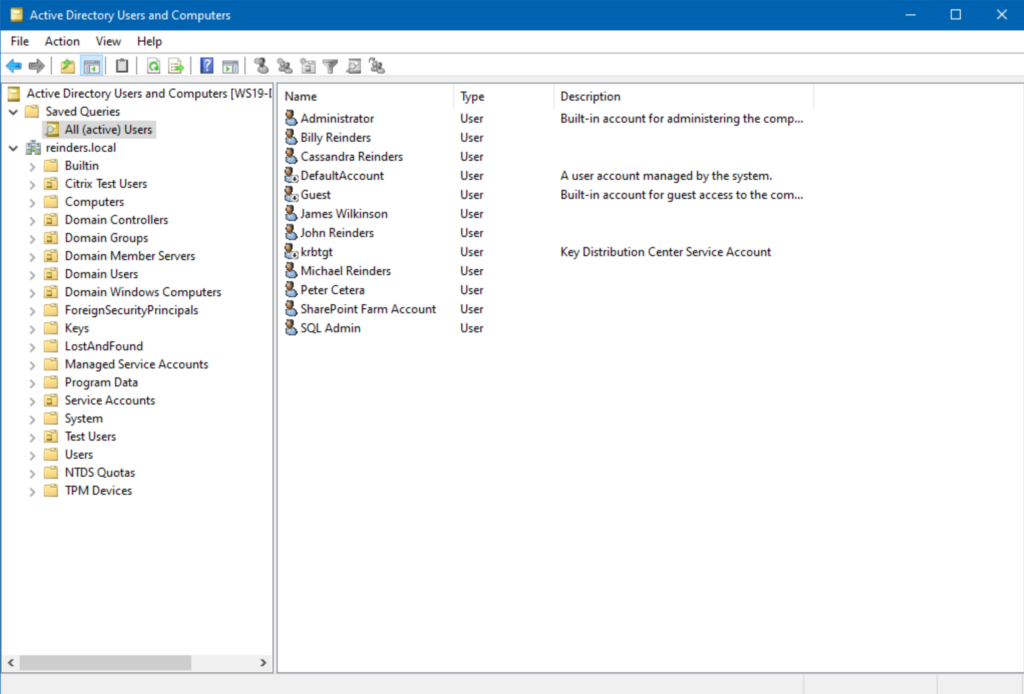
There we go! We’ve now created an always-accessible query for active users in our Active Directory.
Defining a custom LDAP query for our search
Let’s use a different custom query.
- Start another New Query. Choose a Name and Description, then click Define Query… again.
- In the ‘Find:‘ box at the top, choose ‘Custom Search.’
- Next, click the Advanced tab and enter this LDAP query:
(&(&(objectCategory=user)(userAccountControl=512)))
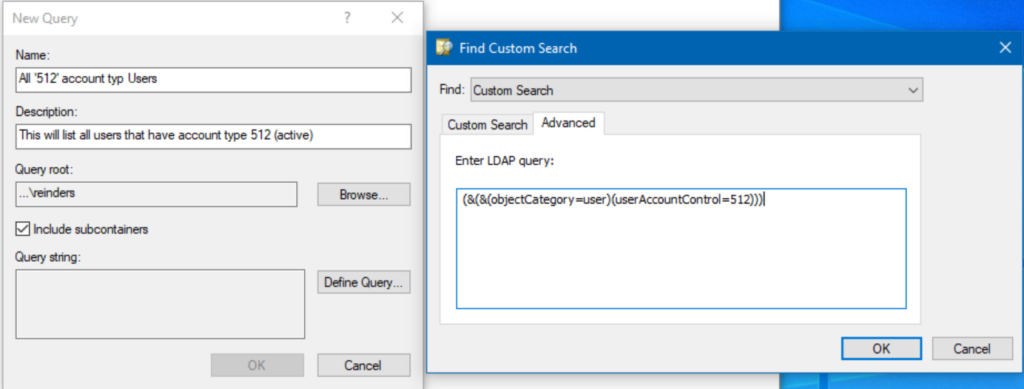
- Click OK twice and voila!
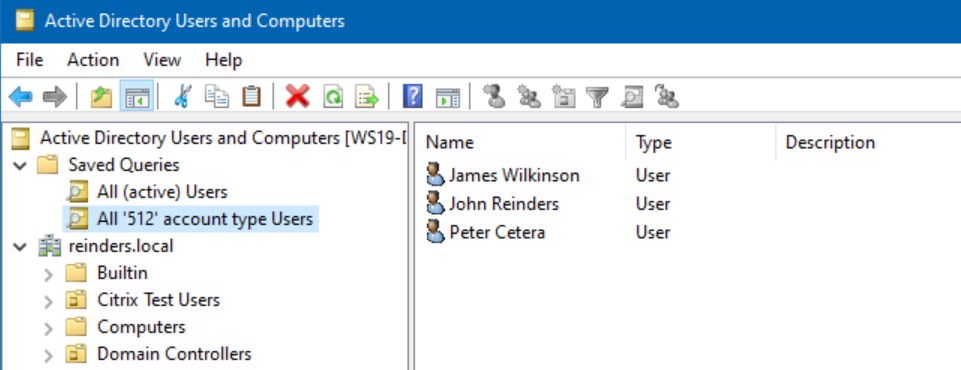
As you can see, only very ‘basic’ or vanilla users will be listed here. Only user accounts that have NO special attributes will be listed in this query.
Remember that table at the beginning of this article? If any account has any of those other attributes or states, they won’t show up here. It’s actually a nice tool to have.
How to list all users in Active Directory using PowerShell
Let’s look at the other main method to find all our users in Active Directory – PowerShell, or, more accurately, the Active Directory Module for Windows PowerShell (yes, I love that name, thank you Microsoft!)
Finding all Active Directory users with the Get-AdUser cmdlet
First off, let’s try finding all users, and format them in table format with the Get-AdUser command
Get-ADUser -filter * | ft
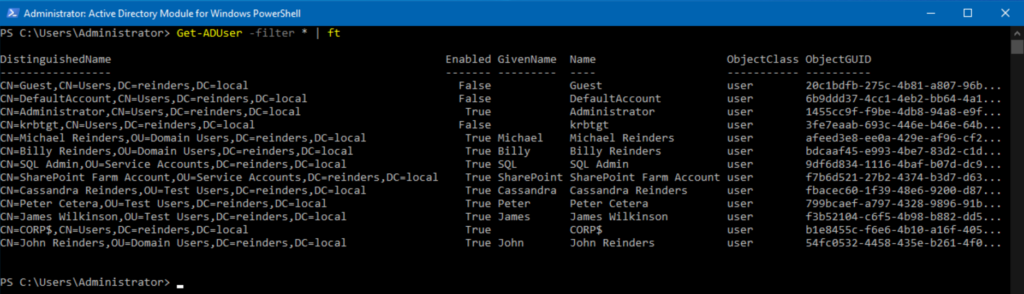
We used the ‘-filter‘ command and chose ‘*’ for all. Then, we ‘piped’ | the output to Format-Table (ft) format.
Filtering results with PowerShell
Now, let’s filter for all the wonderful people in the Reinders clan. We only need the Name and SamAccountName for each, so we’ll add attributes at the end, meaning we ONLY want to see those items.
Get-ADUser -Filter 'Name -like "*Reinders*"' | ft Name,SamAccountName
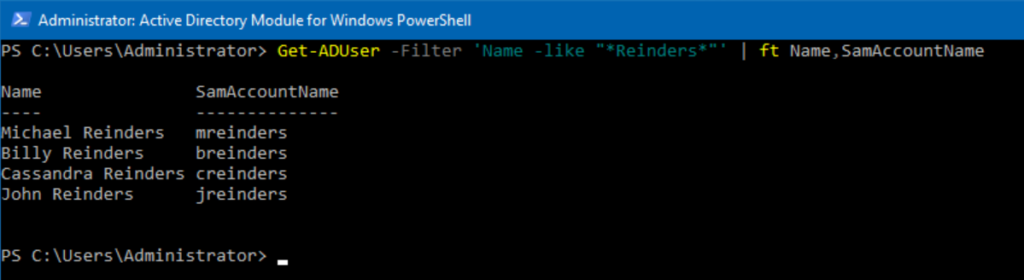
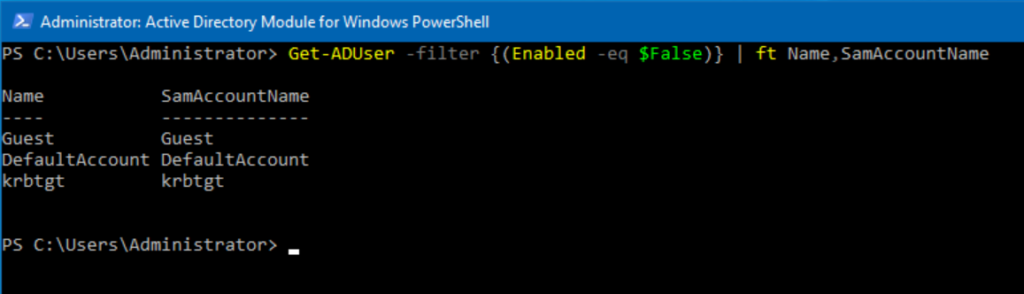
Piece of cake. Let’s get a list of all disabled accounts. We’ll use the following command:
Get-ADUser -Filter {(Enabled -eq $False)} | ft Name,SamAccountName
Checking attributes for user accounts in Active Directory
In case you’re unaware, there are dozens of attributes in each user account. Let’s get a glimmer of those for Billy Reinders with another variation.
Get-ADUser -Identity breinders -Properties *
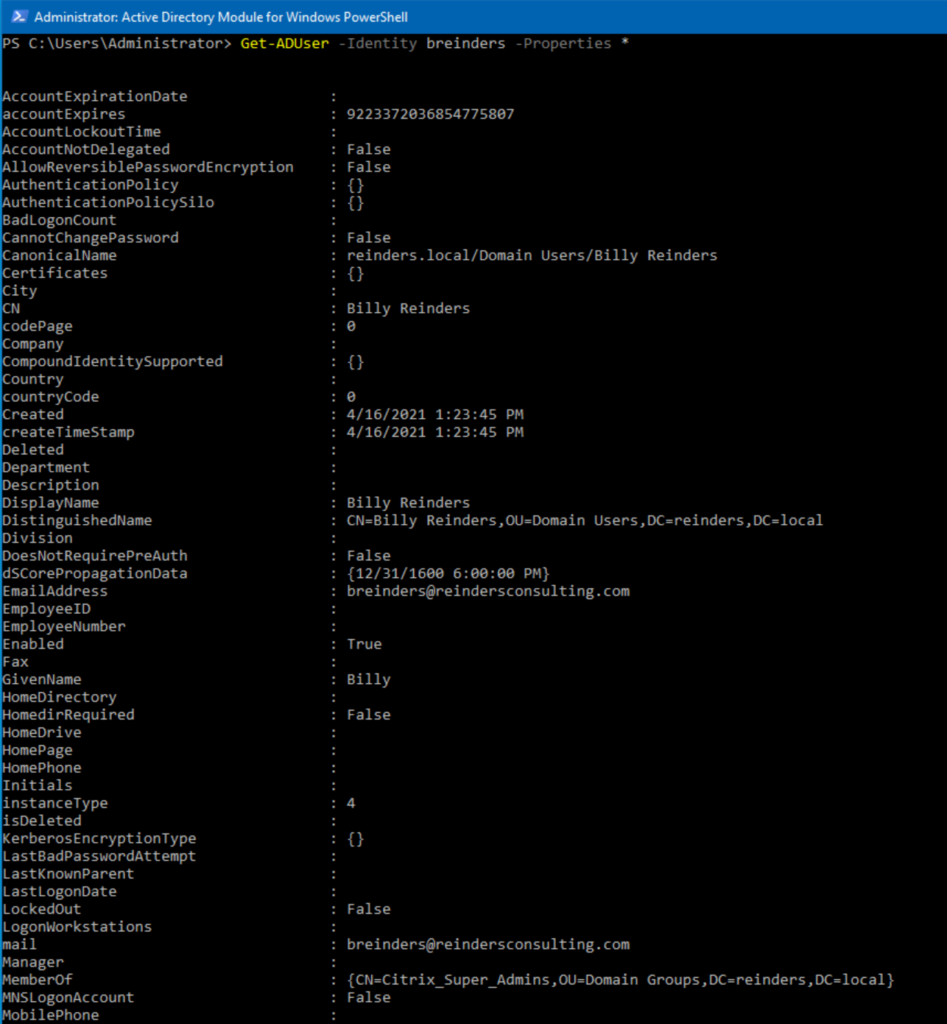
That is about half of them. One nice thing you can do when desiring specific output is to use wildcard characters for what attributes you want.
How about any attribute to do with ‘name’?
Get-ADUser -Identity breinders -Properties *Name*
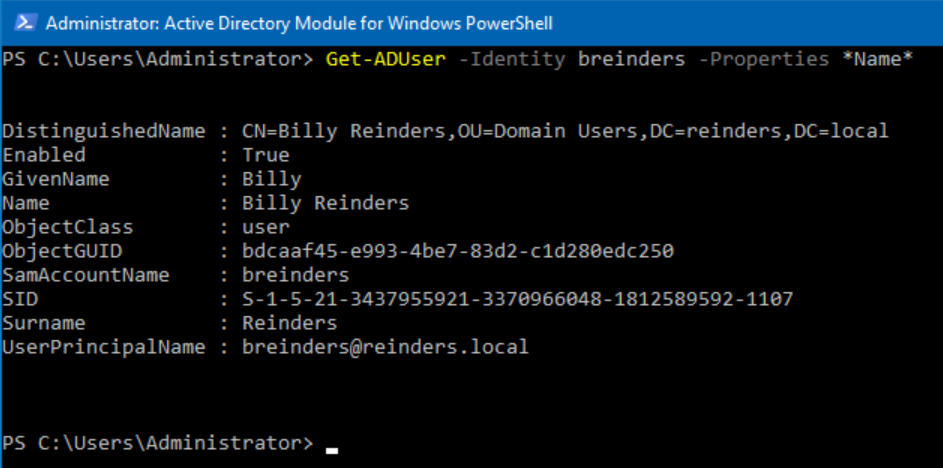
Conclusion
I hope you found some nice nuggets of information here to assist you in discovering all your users in Active Directory. There are a lot of methods you can use, and each one has its own strengths and weaknesses. Finding the right balance, the right tool in each situation helps immensely, especially when trying to hit a deadline from a security directive.
Please feel free to leave a comment below if you have any questions!



