How to Use PowerShell to Manage Folder Permissions
- Blog
- PowerShell
- Post

Managing file and folder permissions is a complex and time-consuming process. This is especially so when utilizing the standard graphical user-interface (GUI). PowerShell makes this process easier and faster. For example, say you need to update folder permissions across hundreds of user folders, using the GUI would take a very long time whereas utilizing PowerShell makes quick work of large tasks such as this one. What can PowerShell do to assist in managing file and folder permissions? There are a number of ways that PowerShell makes this process easier.
- Listing file and folder permissions
- Adding file and folder permissions
- Removing file and folder permissions
- Modify file and folder ownership
- Enable or disable folder inheritance
Exploring NTFS file and folder permissions
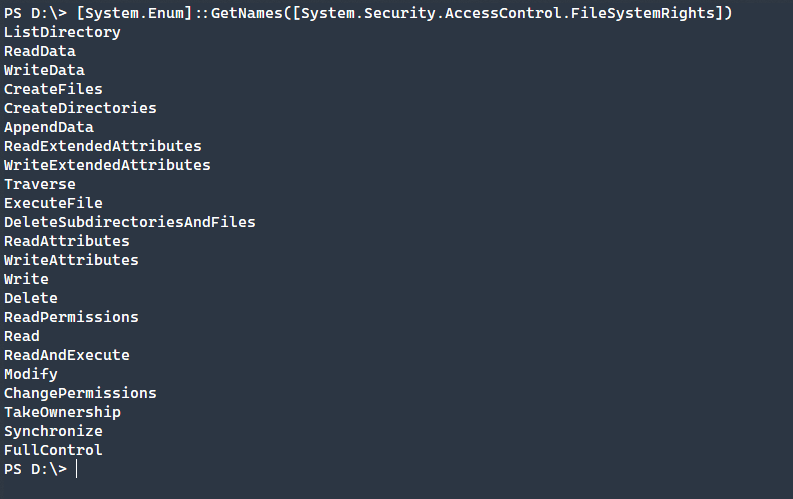
NTFS has a large number of permissions that are available to be set in various combinations on files and folders. To easily view all of the available permissions, you can output the[System.Enum]::GetNames([System.Security.AccessControl.FileSystemRights])It may not always be clear what these permissions can do though and they are broken up into basic permissions and advanced permissions. Basic Permissions
- Full Control: Users can modify, add, move and delete files and directories, as well as their associated properties. In addition, users can change permissions settings for all files and subdirectories.
- Modify: Users can view and modify files and file properties, including deleting and adding files to a directory or file properties to a file.
- Read & Execute: Users can run executable files, including script
- Read: Users can view files, file properties and directories.
- Write: Users can write to a file and add files to directories.
- Traverse Folder/Execute File: Allow navigation through folders, even if the user has no explicit permissions to those files or folders. Additionally, users can run executable files.
- List Folder/Read Data: The ability to view a list of files and subfolders within a folder as well as viewing the content of the files contained within.
- Read Attributes: View the attributes of a file or folder.
- Write Attributes: Change the attributes of a file or folder.
- Read Extended Attributes: View the extended attributes of a file or folder.
- Write Extended Attributes: Change the extended attributes of a file or folder.
- Create Files/Write Data: Allow creation of files within a folder, whereas write data allows changes to files within the folder.
- Create Folders/Append Data: Create folders within an existing folder and allow adding data to a file, but not change, delete, or overwrite existing data within a file.
- Delete: Ability to delete a file or folder.
- Read Permissions: Users can read the permissions of a file or folder.
- Change Permissions: Users can change the permissions of a file or folder.
- Take Ownership: Users can take ownership of a file or folder.
- Synchronize: Use a file or folder for synchronization. This enables a thread to wait until the object is in the signaled state.
Retrieving access permissions on a file and folder using Get-Acl
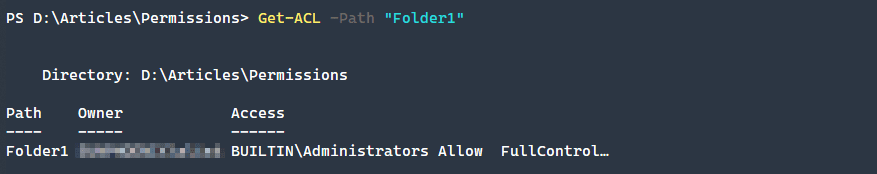
Now that we know what the permissions are, we can look at a given folder and see what the assigned permissions are. Using theGet-ACL cmdlet we can easily retrieve the access rules on an object.
Get-ACL -Path "Folder1"The default view doesn’t give us a ton of information, so let’s expand the
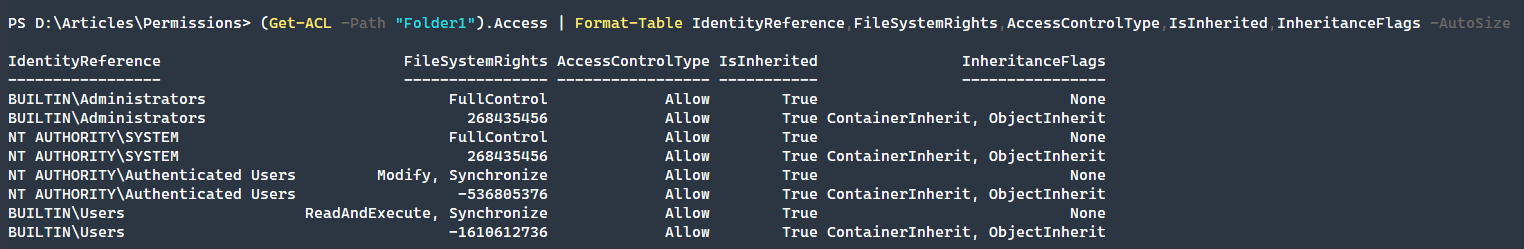
access property more to see what permissions are set on this folder.
(Get-ACL -Path "Folder1").Access | Format-Table IdentityReference,FileSystemRights,AccessControlType,IsInherited,InheritanceFlags -AutoSizeAs you can see there are a lot more permissions here than seen at first glance. What is seen above are typical user permissions on a newly created folder. What if we create a new file and see what its permissions are?
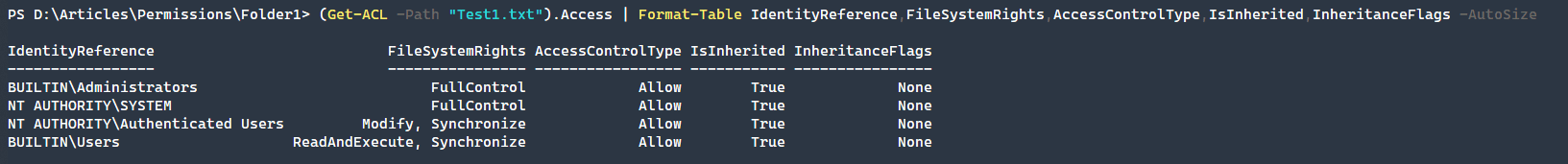
(Get-ACL -Path "Test1.txt").Access | Format-Table IdentityReference,FileSystemRights,AccessControlType,IsInherited,InheritanceFlags -AutoSizeAs you might be able to tell, these are a bit different and don’t container the much of the inheritance type of access rules that folders need.
Modifying files and folder permissions with Get-Acl and Set-Acl
How do we go about updating file and folder permissions then? What if we wanted grant a new user read access to file? To do this in PowerShell it’s easiest to follow this four step process.- Retrieve the existing ACL rules
- Craft a new
FileSystemAccessRuleto apply - Add the new ACL rule on the existing permission set
- Apply the new ACL to the existing file or folder using
Set-ACLTo craft the rule itself, we need to create theFileSystemAccessRulewhich has a constructor like so: Identity String, FileSystemRights, AccessControlType.
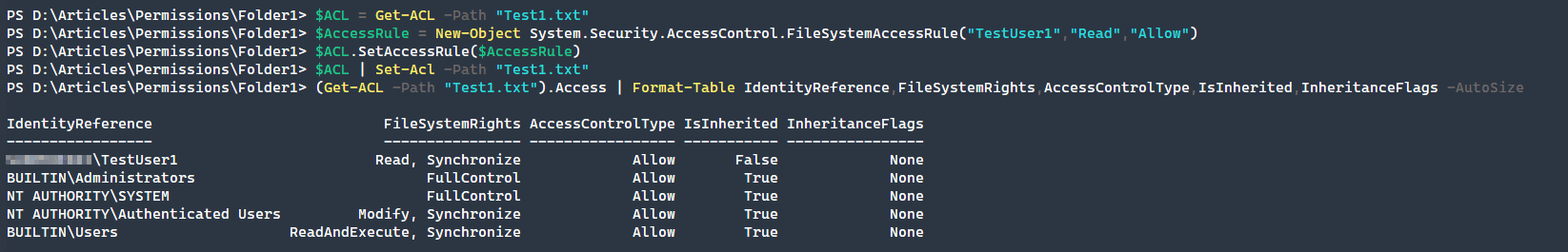
$ACL = Get-ACL -Path "Test1.txt"
$AccessRule = New-Object System.Security.AccessControl.FileSystemAccessRule("TestUser1","Read","Allow")
$ACL.SetAccessRule($AccessRule)
$ACL | Set-Acl -Path "Test1.txt"
(Get-ACL -Path "Test1.txt").Access | Format-Table IdentityReference,FileSystemRights,AccessControlType,IsInherited,InheritanceFlags -AutoSize
As seen in the above process, it is quick and easy to change the permissions and the constructors for the FileSystemAccessRule object are straightforward.
Copying permissions to a new object with Get-Acl and Set-Acl
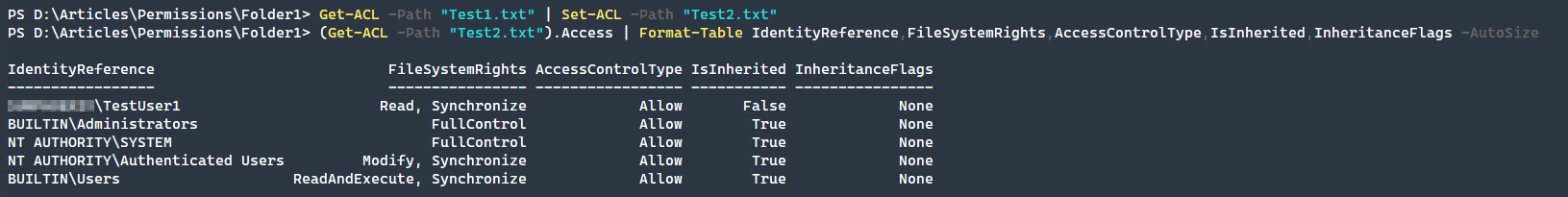
Since we have setTestUser1 to have Read access to our file, what if we wanted to copy that same permission set to another file? Since we have already done the hard work of adding the new access rule, we can use the PowerShell pipeline ability to transfer the permissions from one object to another.
Get-ACL -Path "Test1.txt" | Set-ACL -Path "Test2.txt" (Get-ACL -Path "Test2.txt").Access | Format-Table IdentityReference,FileSystemRights,AccessControlType,IsInherited,InheritanceFlags -AutoSize
Removing file or folder permissions with Get-Acl and Set-Acl
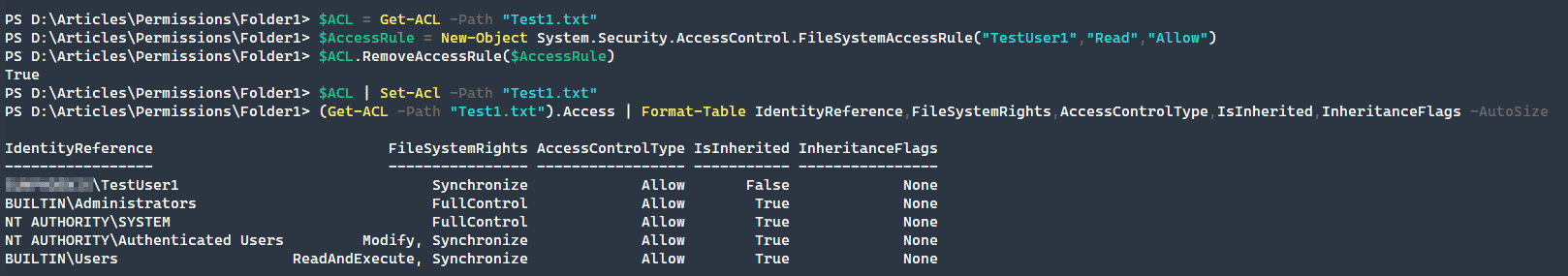
After adding these permissions, we have decided thatTestUser1 shouldn’t have permission to the Test1.txt file. The difference in removing the rule is that we need to recreate the exact FileSystemAccessRule that we want to remove. This is an explicit means of removing permissions that removes ambiguity about what permission to remove. We will approach this very similar to how we added a permission.
$ACL = Get-ACL -Path "Test1.txt"
$AccessRule = New-Object System.Security.AccessControl.FileSystemAccessRule("TestUser1","Read","Allow")
$ACL.RemoveAccessRule($AccessRule)
$ACL | Set-Acl -Path "Test1.txt"
(Get-ACL -Path "Test1.txt").Access | Format-Table IdentityReference,FileSystemRights,AccessControlType,IsInherited,InheritanceFlags -AutoSize
As you can see above, we removed the read permission from this object. The synchronize permission is a special permission that the operating system uses to maintain proper control over the file and folder permissions.
Modifying inheritance and ownership with Get-Acl and Set-Acl
Finally, two additional file system tasks that are very useful to know are enabling and disabling inheritance on a folder and the changing of a files owner.Disable/enable permissions inheritance
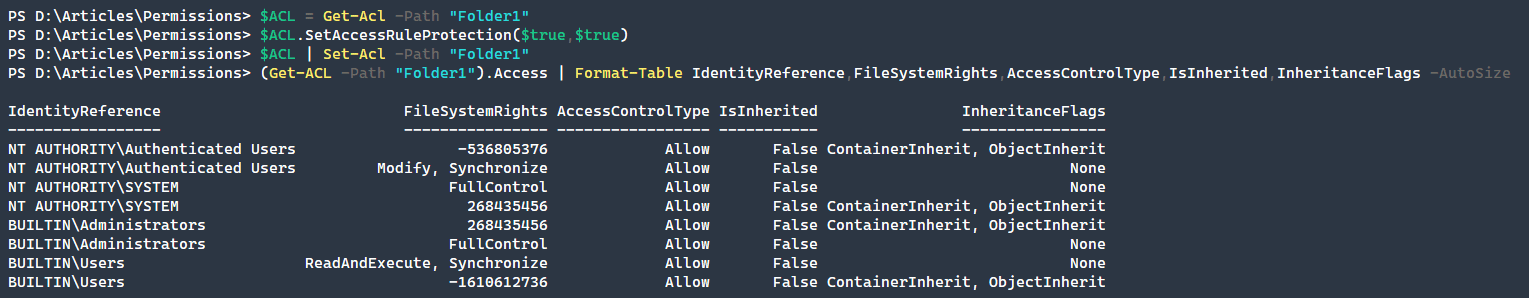
To modify the inheritance properties of an object, we have to use theSetAccessRuleProtection method with the constructor: isProtected, preserveInheritance. The first isProtected property defines whether or not the folder inherits its access permissions or not. Setting this value to $true will disable inheritance as seen in the example below.
The secondary property, preserveInheritance allows us to copy the existing inherited permissions onto the object if we are removing inheritance. This can be very important so that we do not lose our access to an object but may not be desired.
$ACL = Get-Acl -Path "Folder1" $ACL.SetAccessRuleProtection($true,$false) $ACL | Set-Acl -Path "Folder1"
You may get an error of, Set-Acl: The process does not possess the 'SeSecurityPrivilege' privilege which is required for this operation. which means that you should run this process under an Administrator account.
Note how the permissions are no longer true under IsInherited. This means that we have copied over the permissions successfully and broken inheritance on this folder.
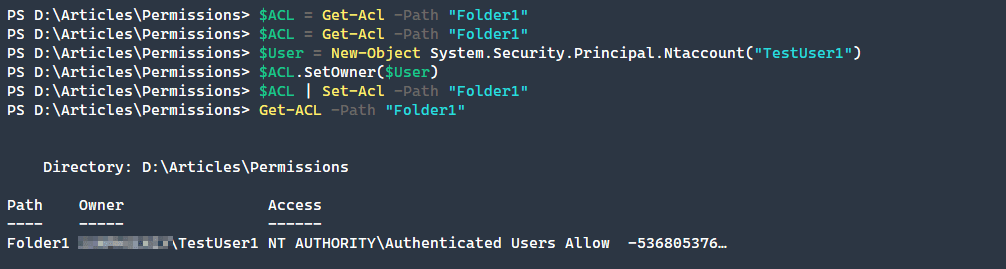
Change ownership with Get-Acl and Set-Acl
Finally, if you want to change the owner of a file, you can do this simply by using theSetOwner method. After running a Get-ACL command, we can see that the owner has changed to our new user.
$ACL = Get-Acl -Path "Folder1"
$User = New-Object System.Security.Principal.Ntaccount("TestUser1")
$ACL.SetOwner($User)
$ACL | Set-Acl -Path "Folder1"
Get-ACL -Path "Folder1"
Conclusion
PowerShell is able to quickly create, modify, and delete file and folder permissions within the Windows NTFS file system. Many system administrators rely on scripts to modify permissions over a large number of files and PowerShell makes this process quick and easy, easily saving hundreds of hours of GUI operations! Related articles:Table of contents
Table of contents
- Exploring NTFS file and folder permissions
- Retrieving access permissions on a file and folder using Get-Acl
- Modifying files and folder permissions with Get-Acl and Set-Acl
- Copying permissions to a new object with Get-Acl and Set-Acl
- Removing file or folder permissions with Get-Acl and Set-Acl
- Modifying inheritance and ownership with Get-Acl and Set-Acl
- Conclusion