How to Check if a PowerShell Script is Running with Admin Privileges
- Blog
- PowerShell
- Post
If you are using PowerShell to automate administrative functions on Windows, sometimes it can be useful to check if the script is running in the context of a local administrator account. This is known as ‘running elevated’ or ‘elevation’. Many Windows 10 configuration settings, especially those that are system-wide and affect all users, require admin rights to change.
But PowerShell doesn’t have a cmdlet or built-in function that lets you check whether the logged-in user is a member of the Administrators group, which can lead to your scripts failing. To solve the problem, you can build a function to check the logged-in user’s security status. In this article, I’ll show you how to create the function and how to call it in your code.
Using the .NET WindowsIdentity class to check for elevation
PowerShell is based on .NET, so that allows us to call .NET APIs when there is no cmdlet to solve a problem. The .NET WindowsIdentity class, which is accessible in .NET and .NET Core, let’s you perform various checks including obtaining a Windows account token and check if a user has elevated permissions.
The first step is to use the WindowsIdentity class to create a new PowerShell object containing security information about the logged-in user. We do that in two steps. The first step is to get information about the current user and store it in a variable ($id). Then using that information, create a new PowerShell object ($p) that we use later.
$id = [System.Security.Principal.WindowsIdentity]::GetCurrent() $p = New-Object System.Security.Principal.WindowsPrincipal($id)
Now we can confirm the status of the logged in user with an IF/ELSE statement. If the user is an administrator, we write ‘True’ to the pipeline. Otherwise, we write ‘False’.
if ($p.IsInRole([System.Security.Principal.WindowsBuiltInRole]::Administrator))
{ Write-Output $true }
else
{ Write-Output $false }
Now let’s bring all the code together to define the function and give it a name. Let’s call it Check-IsElevated:
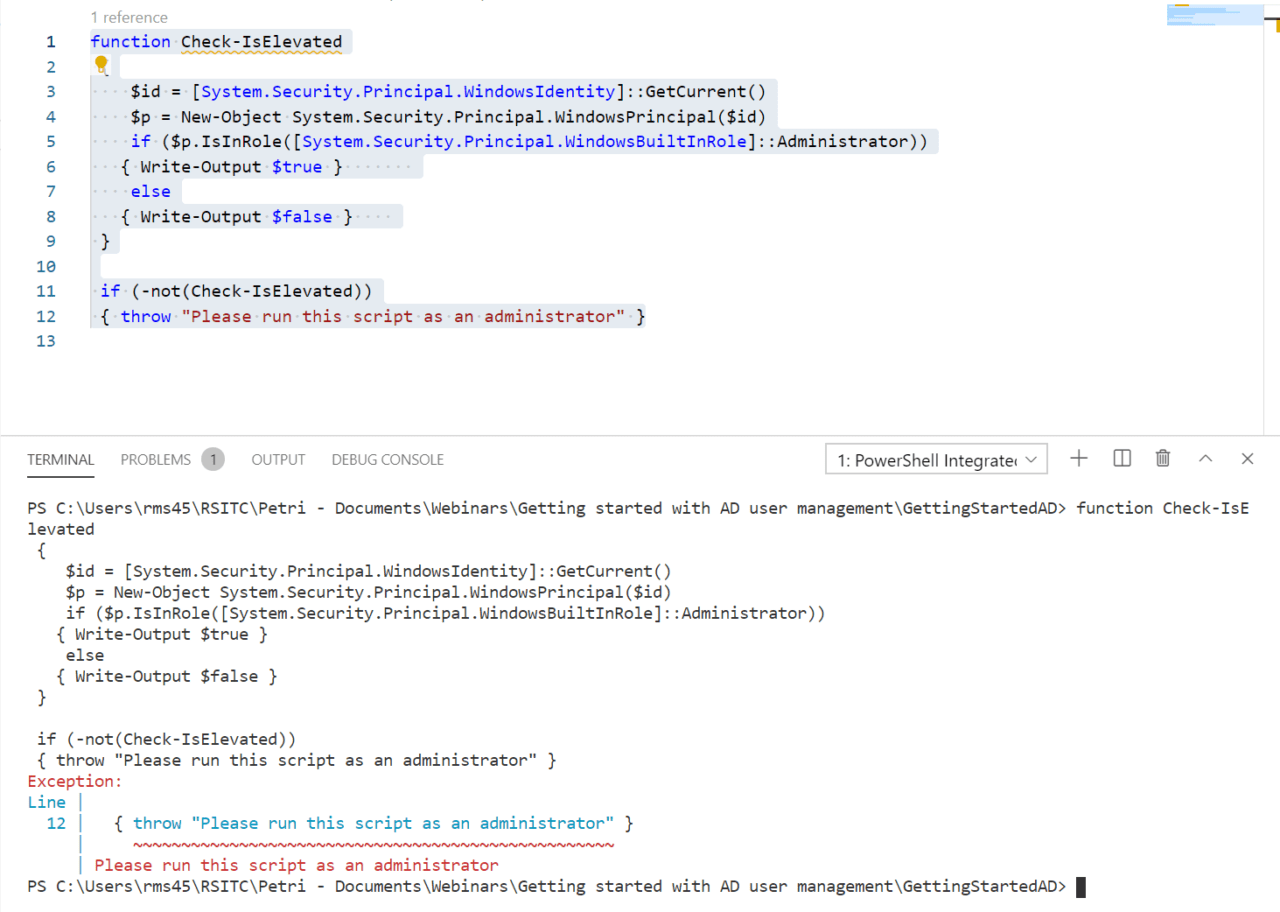
function Check-IsElevated
{
$id = [System.Security.Principal.WindowsIdentity]::GetCurrent()
$p = New-Object System.Security.Principal.WindowsPrincipal($id)
if ($p.IsInRole([System.Security.Principal.WindowsBuiltInRole]::Administrator))
{ Write-Output $true }
else
{ Write-Output $false }
}
Call the function from your PowerShell code
All that’s left to do is call the function to check whether the user is an admin. We can use an IF statement with the -NOT operator to call the function and throw an error to stop the script if the user isn’t an administrator.
if (-not(Check-IsElevated))
{ throw "Please run this script as an administrator" }
If the user is an administrator, PowerShell will continue and run the rest of your script.
Related Article: