How to Automatically Hybrid Azure AD Join and Intune Enroll PCs
On-premises Active Directory domain-joined PCs have typically been managed with tools such as Group Policy. At larger scales, you may have Configuration Manager or third-party tools. The availability of Intune (part of Endpoint Manager) in Microsoft 365 subscriptions such as Business Premium and E3 has opened up an alternative. The benefit many are seeing over their existing Windows Server-based toolkit is that Intune-managed devices can be controlled over the public internet. Unlike Group Policy, they do not require line of sight to an on-premises infrastructure to retrieve settings and software, which means less reliance on things such as your VPN when users are off-site (which, you may have noticed, is a big thing now). Configuration Manager lets you do something similar with Cloud Management Gateway, but there is an infrastructure cost to that, which isn’t the case with Intune.
Getting your domain PCs into a position they can be managed by Intune is called enrollment: you enroll your PC into an MDM, in our case Intune. This can be achieved (somewhat ironically given the earlier comments) by Group Policy on Windows 10 version 1709+, which is called auto-enrollment. After the policy applies, the devices will appear in Endpoint Manager and you can control them from the cloud.
One of the important prerequisites to automatic enrolment is that devices must first be Hybrid Azure AD Joined (HAADJ). In this state, the device remains joined to your on-premises Active Directory, and users still authenticate against on-premises Domain Controllers. However, the device is also “joined” to Azure AD (recently renamed Microsoft Entra ID). Under the hood, this join to Azure AD allows it to perform SSO to Azure AD resources, thereby allowing it to get the necessary access tokens to retrieve your cloud policies.
In this article, you’ll be guided through how to first enable Hybrid Azure AD Join for your devices, then how to enroll them automatically.
Hybrid Azure AD Join
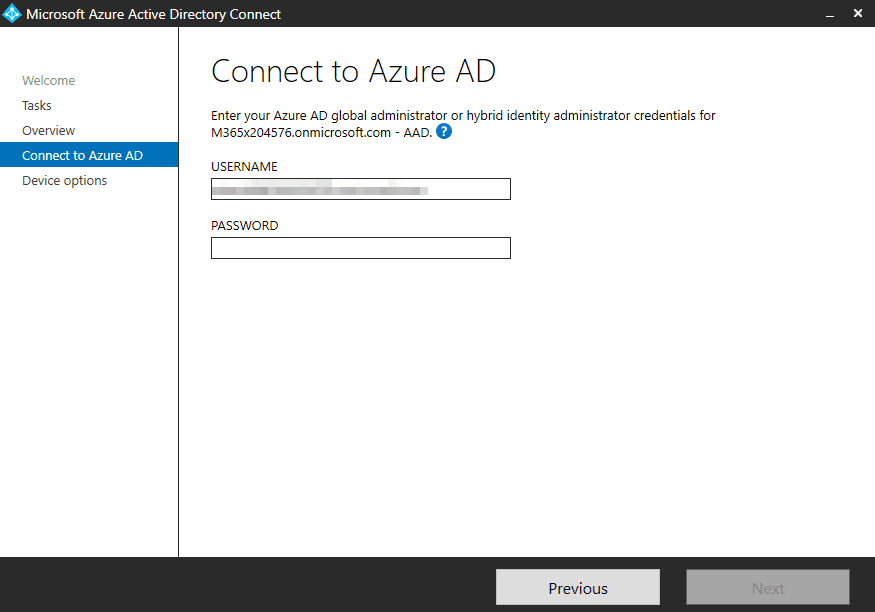
1. On your Azure AD Connect server, launch the Azure AD Connect setup wizard and choose to configure its settings.
2. Hybrid Azure AD Join is then configured within the configure device options menu
3. If you have Azure AD Connect 1.6.2.4, you can authenticate to Azure AD using an account with the Hybrid Identity Admin role in Azure AD. If you are on an earlier version, you will need to use a Global Admin account.
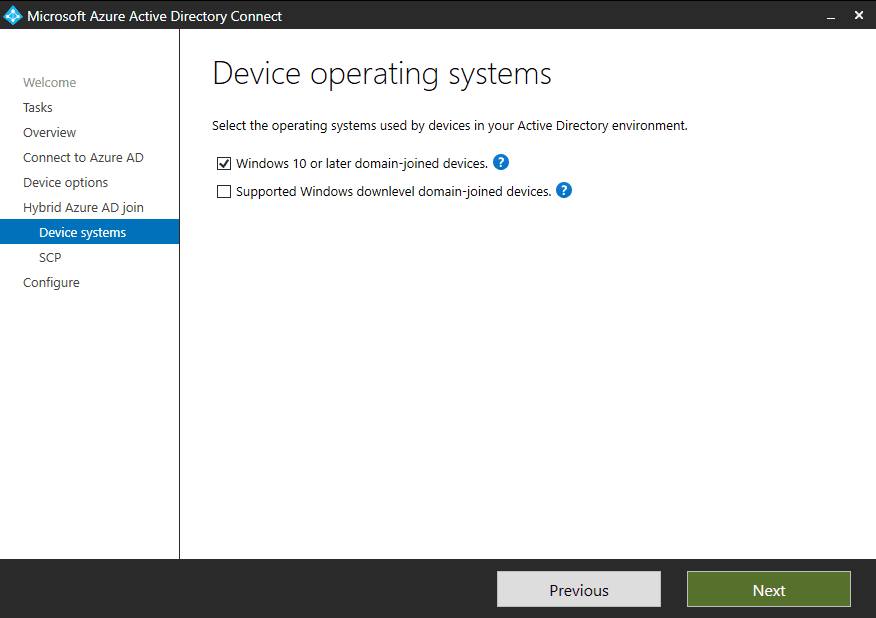
4. After authenticating, choose to configure Hybrid Azure AD join, after which the device operating systems page allows you to scope Windows 10 devices or downlevel devices, which is Microsoft-speak for Windows 8.1 or 7. These operating systems cannot be onboarded to Intune using automatic enrollment (and you should be replacing them with Windows 10 anyway).
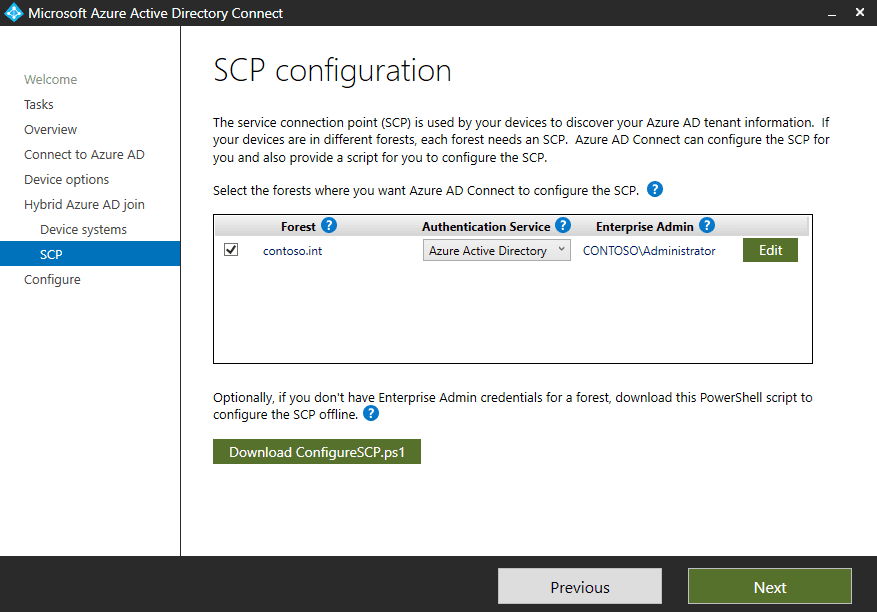
5. In order for your Windows 10 devices to know to join Azure AD and which Azure AD tenant to join, Azure AD Connect populates Active Directory with a service connection point (SCP), configured on the SCP configuration page. Choose the forest(s) that should be configured in and click Add to specify credentials against each to allow it to do so.
6. That’s you done with the configuration wizard. A final page asks you to confirm you want to proceed, so click configure. You can control the scope of devices becoming HAADJ the same way you control users in Azure AD Connect scope, such as by OU.
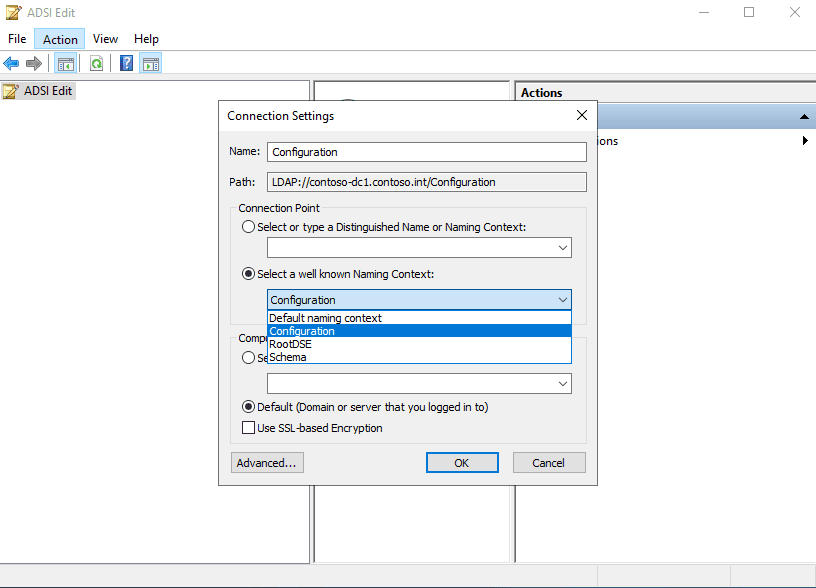
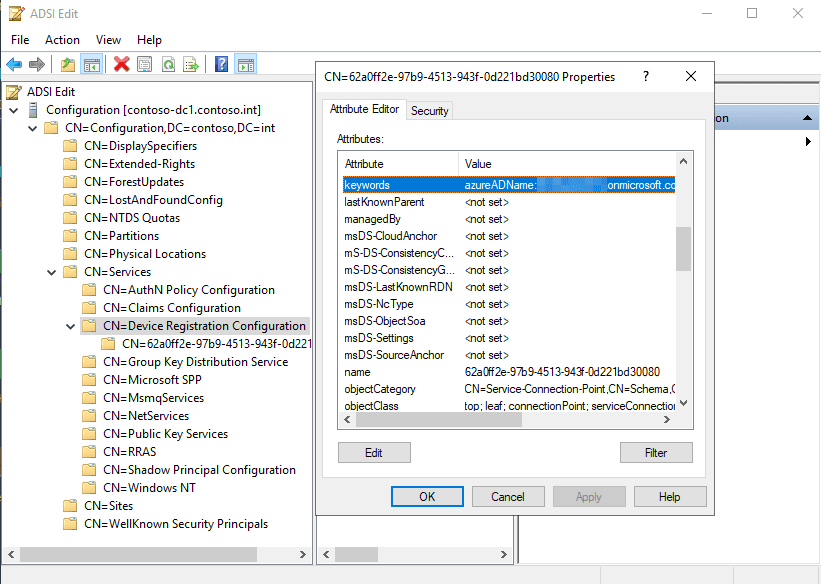
7. When complete, if you’d like to double-check you’re good to go, open ADSI Edit then Action > Connect to. Specify the configuration naming context then expand the navigation tree to Services\Device Registration Configuration. In the properties of the object within, you’ll find the keywords attribute which contains the SCP tenant information.
As devices connect to Active Directory and retrieve this information, they will automatically become Hybrid Azure AD Joined. You will see this by visiting the Azure Active Directory portal, which will report Hybrid Azure AD Joined as the device state. While this confirms they are authenticating to Azure AD, you don’t have much management over them yet. That’s done with Intune.
Intune Auto-Enrollment
After a device is Hybrid Azure AD Joined, it can apply Group Policy to auto-enroll into Intune. Note that although HAADJ is a prerequisite for this method of Intune enrollment, you don’t have to micro-manage the sequence of events. If the Group Policy applies when not HAADJ, it will simply keep retrying until it is. Similarly, the authenticating user must have appropriate licensing and be in scope for Intune MDM within Azure AD.
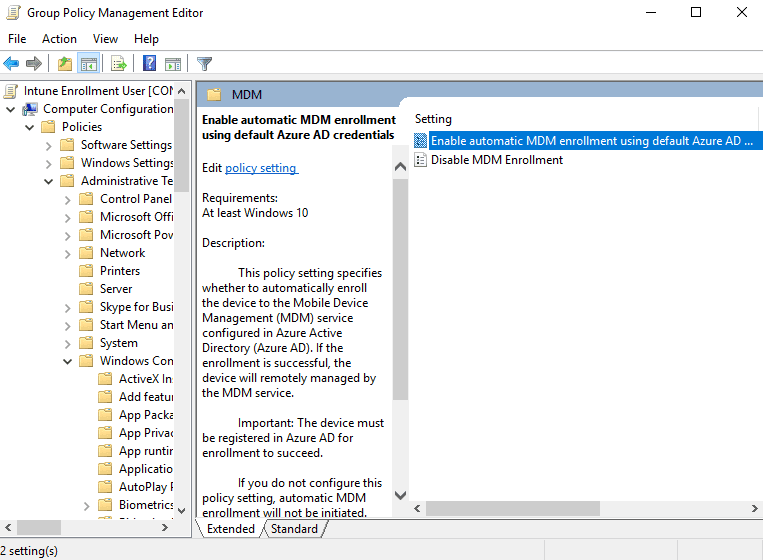
1. In the Group Policy Management console, create a new Group Policy Object and open it in the Group Policy Management Editor.
2. Navigate to Computer Configuration > Policies > Administrative Templates > Windows Components > MDM.
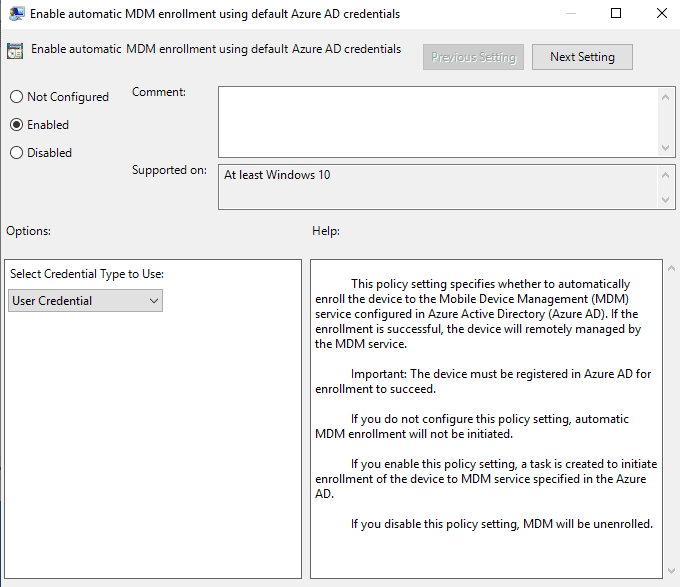
3. The Group Policy setting which enables auto-enroll is enable automatic MDM enrollment using default Azure credentials.
5. After you choose OK against the Group Policy setting, it’s configured, and you only now need to scope the Group Policy Object to OUs with devices that should be auto-enrolled. The advantage of this approach is you can deploy the policy to proof-of-concept devices first to confirm success.
When Group Policy next updates on those devices to which the setting is scoped, they will pull down the setting for Windows 10 to attempt to enroll to Intune with no user interaction required. This is achieved by the setting creating a recurring Task Scheduler entry called Schedule created by enrollment for automatically enrolling in MDM from AAD.
Confirming success
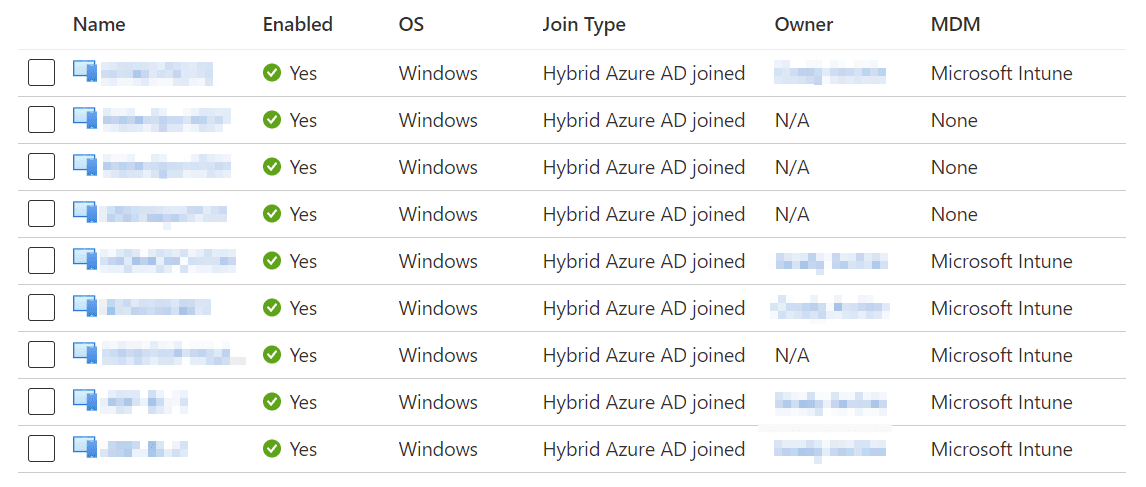
Hybrid Azure AD Joined devices will report as such in the Azure Active Directory admin centre’s device list. Additionally, a field in the admin centre reports devices’ MDM which, if reported as Intune, confirms the client has successfully executed the scheduled task created by Group Policy. If the MDM reports as none, this means that the task has not enrolled the device into Intune yet, so you may wish to view the device’s Event Viewer logs, found under Applications and Services Logs \ Microsoft \ Windows \ DeviceManagement-Enterprise-Diagnostic-Provider. Although devices will show in the Azure AD admin centre just by being Hybrid Azure AD Joined, they won’t show in Endpoint Manager until they are Intune enrolled. If you find devices are not even showing in Azure AD, they are likely not correctly becoming HAADJ. The command line too dsregcmd /status is a useful diagnostic tool on the client for troubleshooting this.