Microsoft Intune App Protection Policies Get Improved Targeting Capabilities
With Microsoft Intune Service Release 2109, released the week of 27th September 2021, there have been some significant improvements in how targeting for App Protection Policies can be achieved. These new capabilities come alongside an array of new Intune capabilities available in this new update.
What are Microsoft Intune App Protection Policies?
According to Microsoft, “App protection policies (APP) are rules that ensure an organization’s data remains safe or contained in a managed app. A policy can be a rule that is enforced when the user attempts to access or move “corporate” data, or a set of actions that are prohibited or monitored when the user is inside the app. A managed app is an app that has app protection policies applied to it, and can be managed by Intune.”
Previous experience
Prior to this new release, Microsoft Intune administrators were required to specify the list of applications that would be targeted by App Protection Policies. This static list approach meant that when new applications were released or made available, they would not automatically be included in App Protection Policies.
The problem with static assignments
App Protection Policies are usually configured to restrict data movement into and out of Corporate and Non-Corporate apps, such as preventing cut/copy/paste of data from Outlook to Facebook. However, as new applications are released, for example a new Microsoft application that users are permitted to use to access corporate data, these applications would need to be manually added to the App Protection Policy to ensure corporate data accessed by that application is protected.
In the example above, users logging into a newly released app that is not targeted by an App Protect policy may be permitted to send data to other unmanaged apps and prevented from sharing data with managed apps, which is pretty much the opposite of what most administrators are aiming toward!
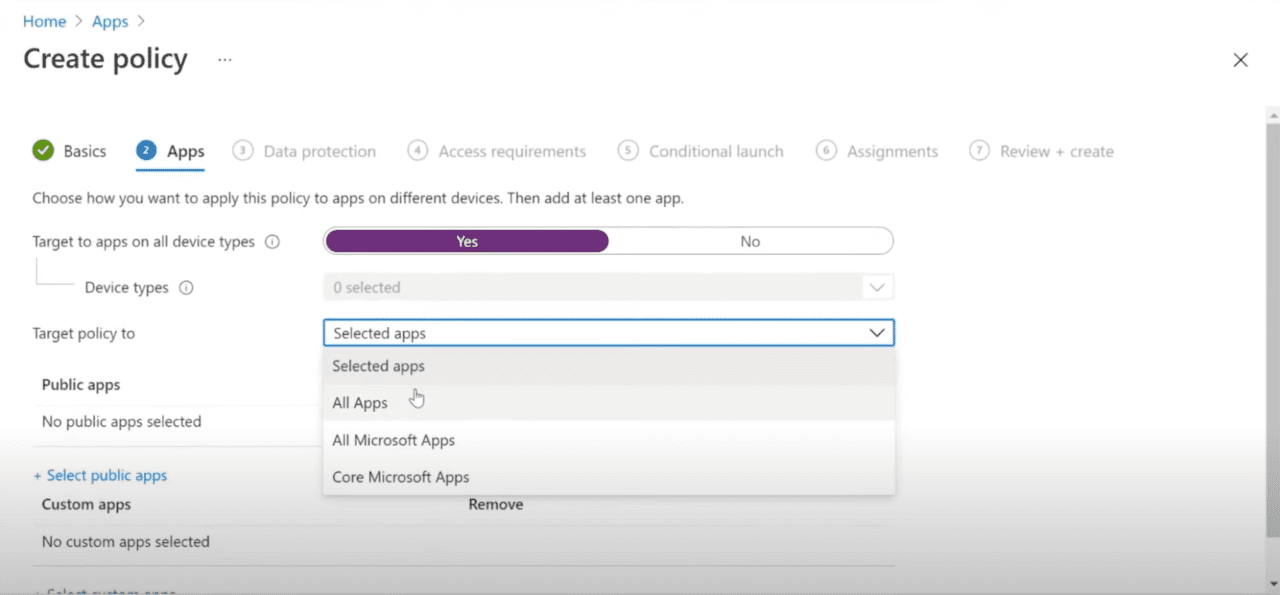
App Protection policies now support targeting to categories of applications
With the release of Intune Service Release 2109, App Protection policies now support targeting to categories of applications.
The following categories are available:
All Apps: This category contains all apps that support the App Protection Policy feature set. This list will be dynamically updated as a new application becomes supported by Intune App Protection.
All Microsoft Apps: This category contains all supported apps from Microsoft themselves – this includes apps that are legacy, such a Skype for Business, as well as apps that are less well known, such as Lists.
Core Microsoft Apps: This category contains all apps that Microsoft considers “Core”. This includes apps such as Outlook, Word, Excel, and PowerPoint.
With this new approach, administrators no longer need to individually select which applications are targeted by App Protection policies. This reduces the administrative requirement whilst initially building policies, but it also means that any future application releases can be automatically included in existing App Protection Policies.
Once an App Protection policy has been created with a specific category targeted, administrators can select “View a list of the apps that will be targeted” to view a list of the apps that will be affected by their policy, allowing administrators to visualize which applications will be included in their policy.
Shortcomings – categories and manually selected applications can’t be mixed
Whilst this new feature is very welcome for many Intune administrators, it is not possible to mix both categories and manually selected applications. Where organization requirements dictate a specific third-party application be included alongside Core Microsoft Apps, the entire targeted list would need to be manually selected to achieve this.
As with all Microsoft Intune features, this release is expected to be improved and updated in the future. Perhaps in a few months we will see the ability to mix specific application selection with Core Microsoft Apps. In the meantime, administrators should use a static list containing all apps they require, rather than deploying two separate policies because policies are distinct bubbles, and can’t be combined to share data
Prevent users deliberately or accidentally sharing data to unmanaged apps
App Protection policies are useful to ensure users can’t deliberately or accidentally share data from corporate managed apps to non-corporate / unmanaged apps. They can be assigned to managed and unmanaged devices alike, giving control and flexibility when deploying this security solution.
When deployed correctly, App Protection policies give a real alternative to the requirement for full device management on mobile devices, meaning organizations can move towards allowing users to be productive and secure on any device they choose.