Exchange Online Protection’s Ongoing Battle Against Malware
The Odd Attachment Containing a PayPal Receipt
When I researched the innards of anti-malware protection to write about how Exchange Online Protection (EOP) uses safety tips to flag potential scams, I looked at multiple messages with the aim of seeing how well the visual clues worked. In most cases, EOP did a good job of picking up spam and phishing messages and those items were stamped with the appropriate safety tips.
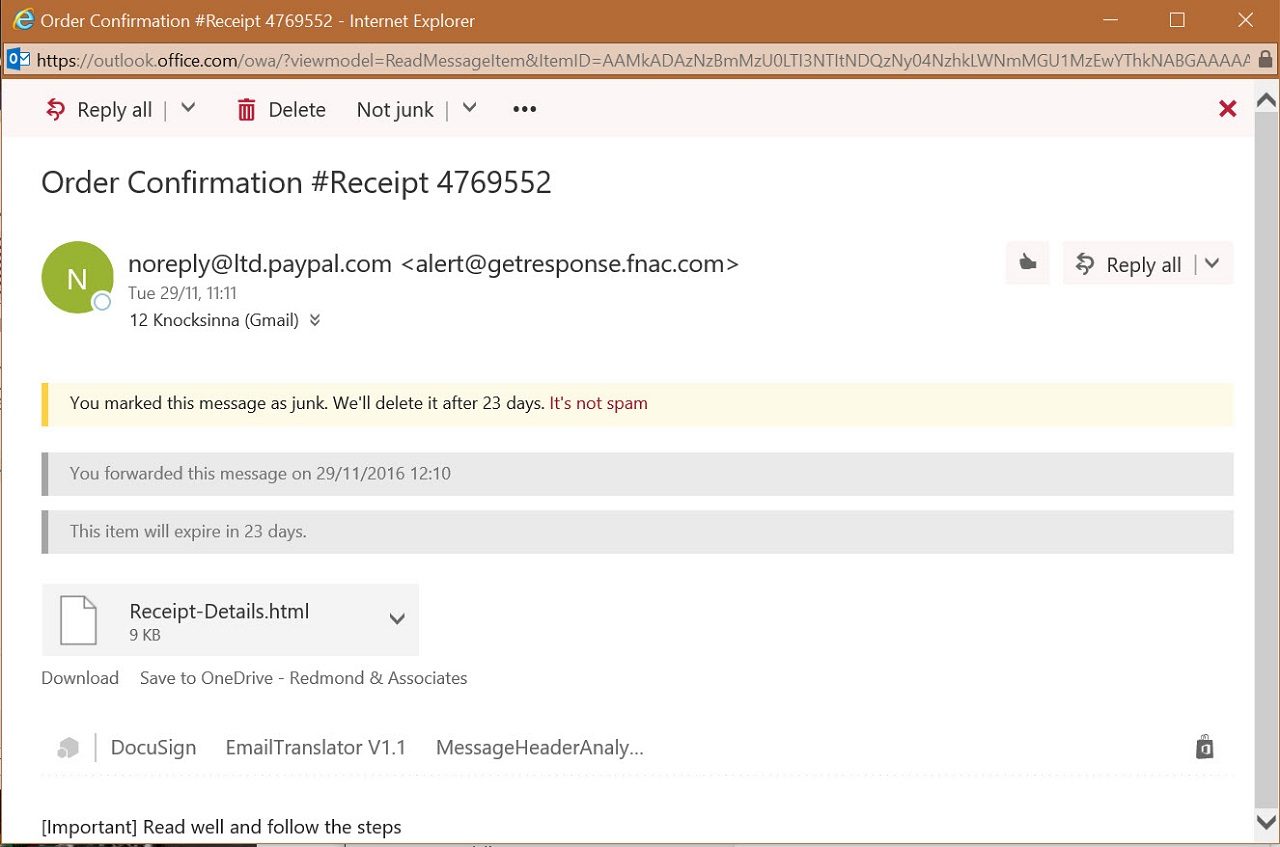
However, in one case, EOP seemed to miss a pretty obvious scam. I received a message that contained an HTML attachment informing me that I had used PayPal to pay $49.99 for some in-game purchases for Facebook’s Farmville game (Figure 1).
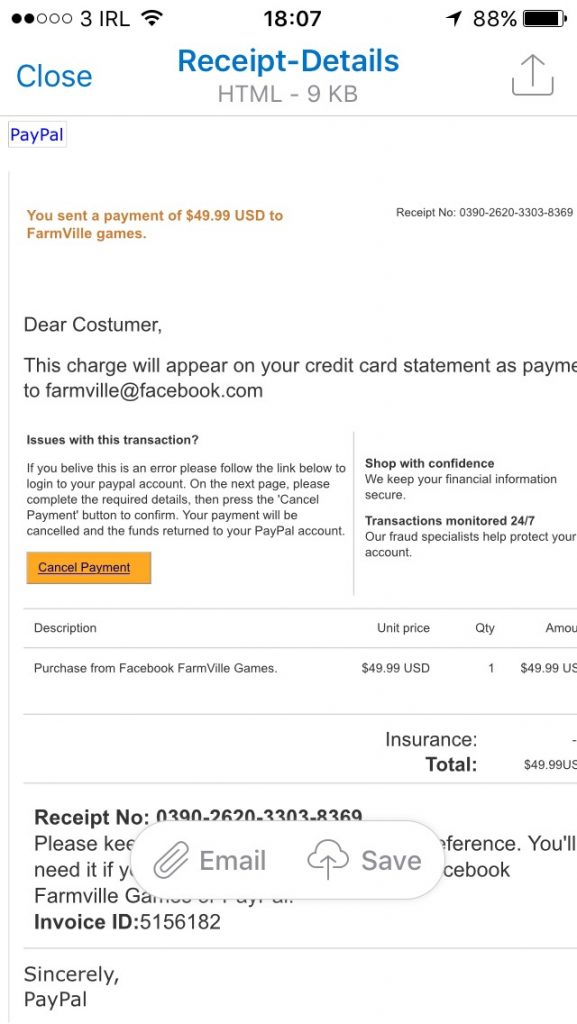
Naturally I was taken aback. The thought of playing Farmville let alone paying for the privilege was sufficient to rise my hackles. I imagine that many others who received similar messages would feel the same and hurry to click the “Cancel Payment” button, which is how people are lured into the web of lies and deceit woven by the phishers.
Why Some Spam Gets Through
The experience led to the question of why did EOP allow a message that looks to be so obviously a phishing attack to be delivered to my inbox? I posed the question to Microsoft’s Terry Zink, a program manager working on EOP who writes an excellent blog covering the trials and tribulations of fighting spam.
The message had originally been delivered to my Gmail account and then forwarded to Office 365. I do this with several other email accounts in order to have all my email come to the one place, which seems logical.
Terry pointed out that messages forwarded from another email service to Office 365 create difficulties for EOP when it comes to detecting malware. The messages have already been through the anti-malware processing for the other email service and come to EOP looking all clean and shiny. There are many technical reasons why it is difficult to reprocess mail coming in from another service, all explained in this post.
Multiple Hygiene Services Can be a Bad Thing
The difficulties that exist are why Microsoft recommends that the MX records for tenant domains point to EOP rather than going through another mail hygiene service. In a nutshell, if you apply anti-malware filtering before EOP gets to do its stuff, the following might occur:
- IP reputation blocks, and IP throttling, do not work properly
- DNS checks that use the sending IP do not work properly, such as PTR lookups, SPF checks, DMARC checks, and even DKIM if you route it through a mail server that modifies the message content
- IP Allow entries do not work properly because the original sending IP has been lost
- Some rules in the spam filter will not work properly because they look for a particular IP range or sending PTR
- The Bulk mail filter does not work properly
- The anti-spoofing checks do not work properly
Given the amount of threat circulating in email, losing those elements of protection is enough to concentrate the mind.
Random IT Phishing
My response was that I thought that EOP should have caught this message because it’s so obviously false. In technical terms, the message is an example of a “random IT phish”, or a message that appears to come from a legitimate source such as an IT department.
In this case, the spammer had carefully inserted a plausible display name into the message, counting on users not to check the actual return address.
From: “[email protected]” <[email protected]>
It’s easy to miss detail like this when messages are scanned quickly, which is exactly what the spammer counts on to snare victims.
EOP Generic Protection Coming to Catch Non-Domain Spoofing
EOP added protection for exact domain spoofing (spoofing your own domain) or Business Email Compromise earlier this year (one of the features that requires the MX record for a tenant to point to EOP). Exact domain spoofing won’t catch spoofing like this because PayPal is being spoofed rather than the tenant. But “generic protection”, where the apparent email address doesn’t have to be the tenant’s domain, will. And the good news is that this feature is due to be fully deployed across Office 365 very soon.
Punycode
According to security company Avanan, Office 365 suffers from a security defect where a method for encoding domain names with Unicode characters is used to conceal a phishing attack aimed at stealing user credentials. Punycode is used to allow non-ASCII characters in a URL. Avanan alleges that the Office 365 anti-malware techniques can’t detect when URLs redirect users to a false log-in site that resembles Office 365. Apparently, the attack was discovered on December 9.
According to a statement issued to SC Media, Microsoft says that “the anti-phishing filters found in Office 365 are not fooled by this attack.” Microsoft also says that “Office 365 can and does mark this type of attack as spam.” The generic protection referred to above is one of the ways that EOP will catch phishing of this nature.
Avanan has been down the road of “exposing” Office 365 frailties before, most recently in June 2016 when they caused a lot of fuss and bother about an apparent day-zero ransomware attack against Office 365 users. That attack came to naught and I suspect that this one will too. Good marketing seeks to increase the need for your products and that happens in the security arena as well as in other parts of IT.
Suffice to say that I have heard no evidence that any Office 365 user credentials have been stolen. But feel free to accept Avanan’s offer of “a free tool to scan your Office 365 inboxes and see if you were a victim of this attack”. Stranger things have happened, but unless the attacker has left their calling card behind, quite how examination of an inbox would reveal that you’ve been a victim of an attack is beyond me.
The Fight Goes On
What the Punycode report does prove is that new scams and attack techniques appear all the time. If you use email and don’t have good protection, you can expect problems. If you don’t know how to manage anti-malware technology, go get some help.
No single change will stop spam. The fight continues on an ongoing basis. New spam techniques are introduced, analyzed, and then suppressed. And then the cycle restarts. All of which means that combating malware is a long-haul fight instead of a simple battle. I rather like that Microsoft is doing the heavy lifting for Office 365 tenants in this area. Their security experts are certainly smarter than I am!
Follow Tony on Twitter @12Knocksinna.
Want to know more about how to manage Office 365? Find what you need to know in “Office 365 for IT Pros”, the most comprehensive eBook covering all aspects of Office 365. Available in PDF and EPUB formats (suitable for iBooks) or for Amazon Kindle.