Safety Tips Inserted by Exchange Online Protection Make Email Safer
Beware What Lurks in Email – It’s a Bad World Out There
It’s a reasonable certainty that even the stupidest user realizes that bad things can lurk in email. Or perhaps not. After all, if the assertion was correct, those who enjoy filling our inboxes with noxious spam wouldn’t continue to do so. And if that happened, the world would have to cope with a sudden lack of offers to gain millions of dollars for just a small investment; or perhaps a great deal on Viagra; or even the chance to confirm our identity to a bank because of a problem with our account.
But spam, malware, spoofing, and phishing are the sordid underworld of email. Messages from people you don’t know or don’t care to know keep on being sent in ever-increasing quantities. Evidence of this fact can be found in the statistics published by anti-spam companies. For instance, TrendMicro provides an interesting global spam map showing the overall volume of spam and the rate of spam in different countries.
The continuing growth of spam and the new and varying techniques used by spammers to get past anti-spam checks is why email service providers need to spend so much time and money suppressing crap before it hits user inboxes.
Exchange Online Protection and Anti-Malware
If you use Office 365 or Exchange Online Protection (EOP), you’ll know that Microsoft provides a wide range of tools to stop spam and malware. Safety tips were announced in April 2016. In a nutshell, safety tips are an attempt to highlight malicious email to users using visual cues. The idea is that people will notice the warnings and so won’t make mistakes and fall victim to scams, spoofing, and phishing attacks.
The delay between the initial announcement about safety tips and now is explained by the need for Microsoft to gather user reaction to the way that tips appeared in messages and the scenarios that were covered. The code to implement safety tips is now being distributed to EOP servers across Office 365 and will soon be effective.
Safety tips are also available in the Outlook.com consumer service. However, the implementation inside Outlook.com is simpler as it doesn’t need to cater for the ability of tenants to customize email delivery, such as deploying a transport rule to process certain messages by adding headers, applying protection, and so on.
Safety Tips inserted by Exchange Online Protection
Safety tips are exposed by email clients when message content is viewed. The intention is that the tip tells a user whether the message is safe (from a trusted party), spam, or just outright bad.
Two forms of safety tips are used. The first is a tag (sometimes called a “safety tattoo”) that is stamped onto messages as they are processed by EOP. This tag is used by OWA to allow users to interact with safety tips.
The second type is an inline safety tip. To allow the safety tips to be viewed by clients that don’t support tags, EOP inserts the text for the tip into the message and then rebuilds the message before it is delivered to the user. Because Office 365 supports 44 languages, EOP checks the language set for the destination mailbox to determine the localized version of the safety tip. If the message format is HTML, the text for the safety tip is written in HTML. If not, it is written in plain text.
OWA offers the most comprehensive support for safety tips. Table 1 describes the four types of tips that can appear in OWA.
| Color | Safety Tip | Condition |
| Red | Suspicious. These messages are likely to condition phishing scams and should not be opened. | EOP detects the presence of a known phishing message or the message characteristics are such that EOP considers it to be likely to be a scam. See this blog post for an explanation of why messages are assigned red safety tips. |
| Yellow | Unknown. The message is spam. | EOP has scanned the message and it has failed the standard anti-spam tests. |
| Green | Trusted. The message is from a trusted source. | Microsoft maintains a list of domains owned by trusted sources (such as itself). Messages from these domains are deemed to be trusted. |
| Grey | Safe. An informational tip. When used by EOP, it shows that the message has been passed safe by the tenant or user. | The message is from a domain considered to be safe by the tenant (for example, the IP address for the server is in the IP allowed list), or on the user’s safe senders list, or it was put in the user’s Junk Email folder and subsequently moved back to the Inbox to indicate its safe status. Microsoft plans to use this tip to provide other information to users in the future. For instance, it might be used to tell users that a message they’ve just received is the first they have got from that sender. |
Table 1: Types of safety tips
Initially, the desktop version of Outlook will only support the red (suspicious) safety tip, which is treated in the same way as a regular MailTip. All versions of Outlook supported by Office 365 can display MailTips, so no change is required to support the red safety tip.
OWA’s Interactive Safety Tips
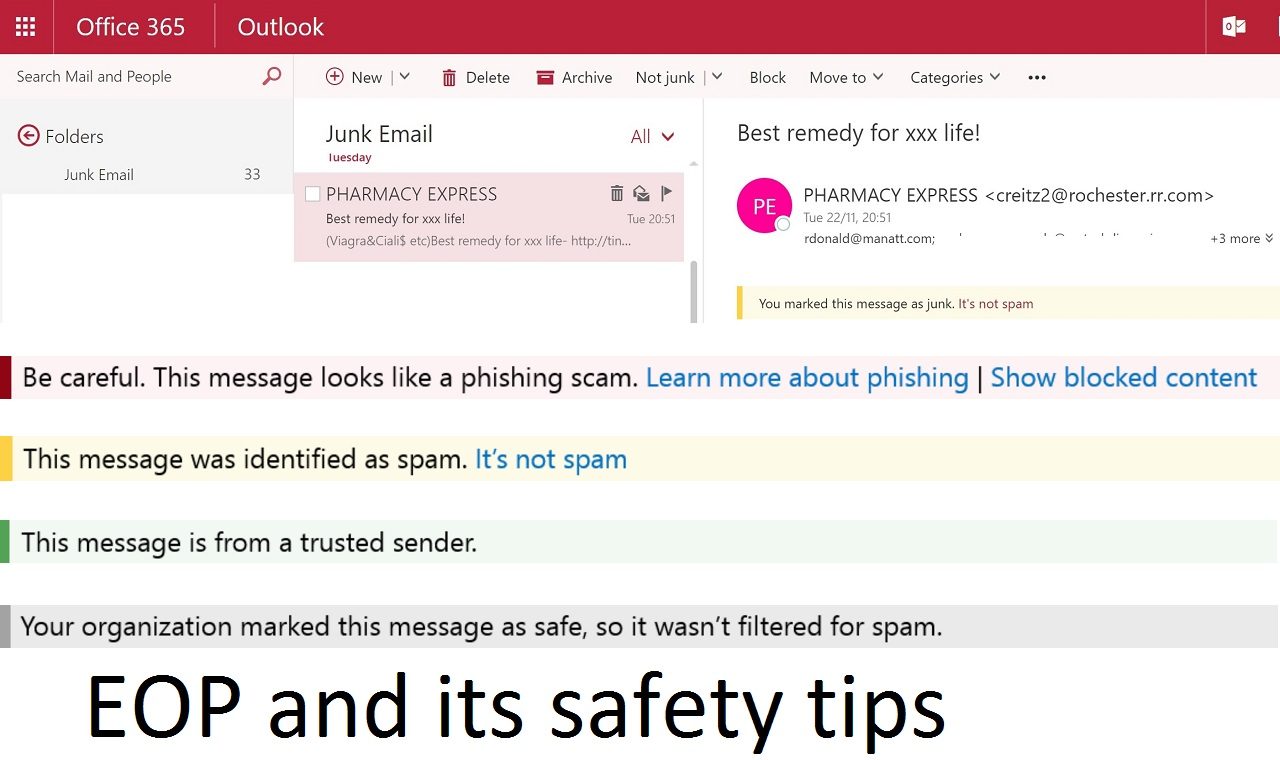
For example, Figure 1 shows a classic spam message from my Junk Email folder, complete with the earnest appeal to enrich my life by giving money to an online pharmacy. The yellow safety tip is clearly visible. In this instance, I marked the message as junk after it originally turned up in my Inbox, so the safety tip indicates that this is how the message arrived in Junk Email.
Given the array of checking techniques deployed by EOP to stop malware, it’s interesting that EOP passed the message for delivery to the Inbox. The fact that the message was delivered proves that combating spam is an ongoing process. For instance, trusted domains or trusted senders created by a tenant or user can override junk mail processing. In any case, some small percentage of spam is likely to get through and users need to be aware of what to do when this happens.
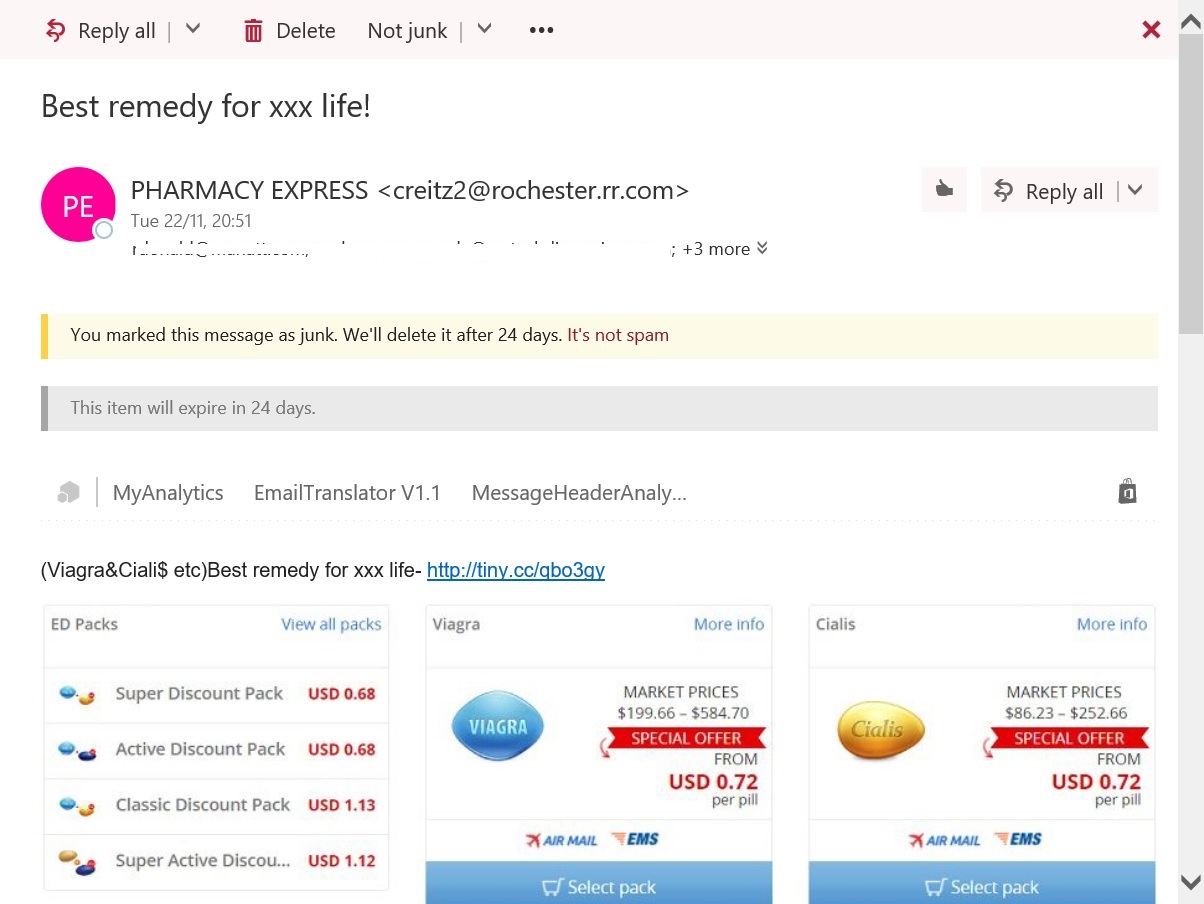
Figure 2 is an example of a message that was detected as spam and delivered direct to the Junk Email folder. You can see that the safety tip is different.
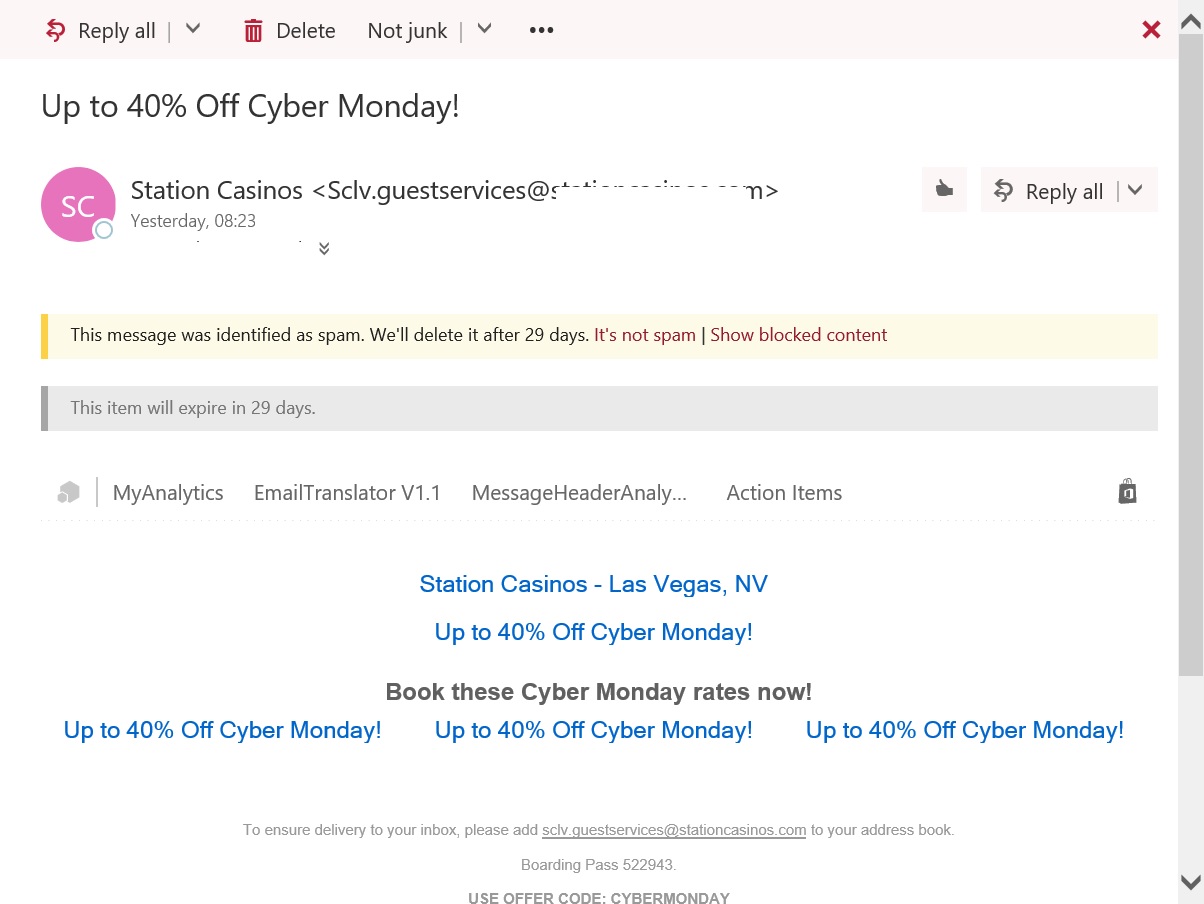
When OWA displays a message, it forms the various elements (header, body, properties) together using JavaScript so that the safety tip can be displayed as an element within the message. As you can see in both examples, some retention information is combined with the safety tip to inform the user when the message will be removed from the Junk Email folder.
To make the safety tip interactive, OWA enables whatever action is appropriate. In this case, the safety tip allows the user to mark the message as “not spam”. When this option is taken, the user can also opt to provide a report to EOP to help improve its anti-spam checks. After the user marks a message as not spam, the safety tip is removed.
Another interaction is when a message contains blocked content (graphics that might indicate to a spammer that you read the message or some other dangerous such as a link to a web site). Again, if you click “Show blocked content” (always a bad idea), you’re signaling that the message is not spam and the safety tip is removed.
Some of the infrastructure for safety tips is not fully activated. For instance, Microsoft has not yet published the list of trusted domains for Office 365 (they already exist for Outlook.com), so don’t expect to see any green safety tips until this happens.
Client Support for Safety Tips
Not all clients that connect to Office 365 understand how to display safety tips and make them interactive in the same way as OWA does. Part of the reason why is down to protocols, part is implementation. Protocols like IMAP4, POP3, and ActiveSync don’t support the concept of safety tips so there’s no way that a client can display an interactive tip. The same is true for the Outlook desktop client, but in this case it’s because the necessary GUI doesn’t exist in current versions. Outlook is therefore limited to displaying the red safety tip (Figure 3). It’s an advisory – nothing more.
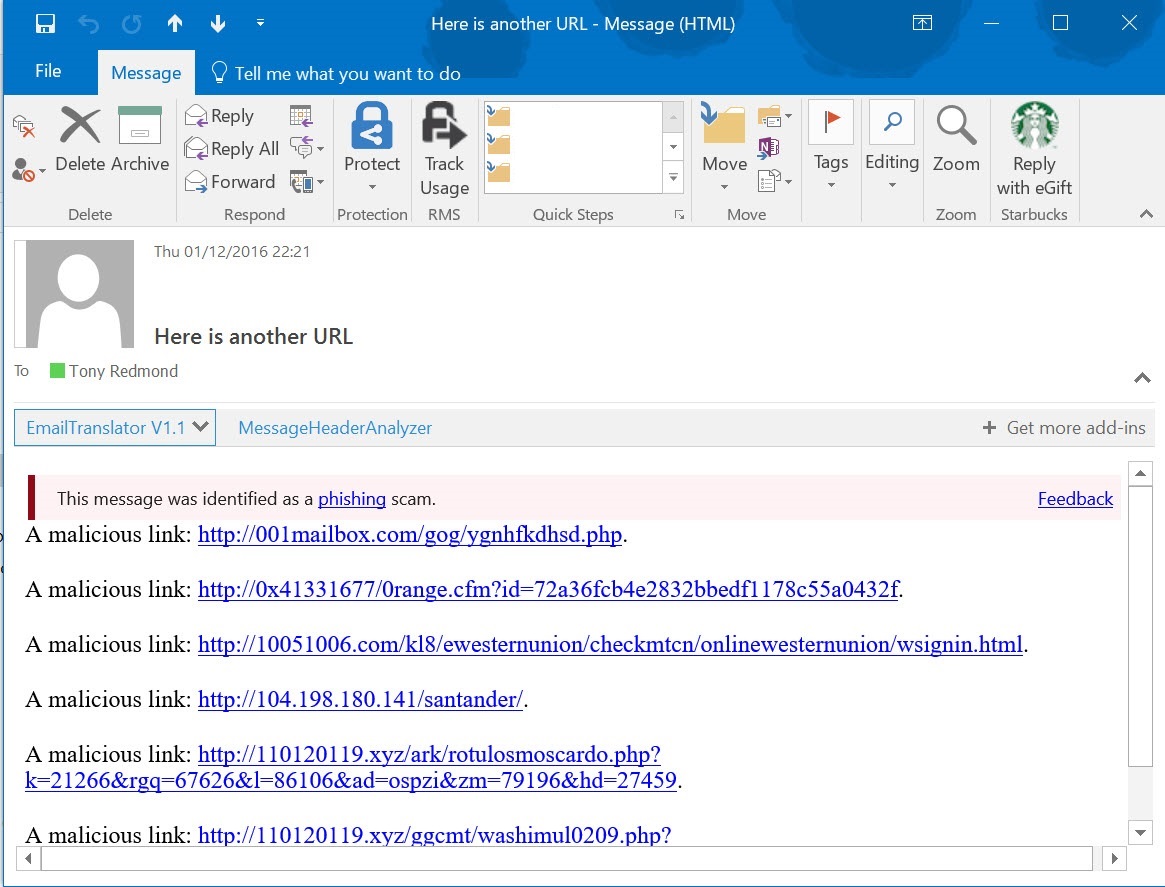
However, because EOP inserts the text for safety tips into messages, all clients are capable of displaying that text as a safety tip. The user won’t be able to interact with the tip, but they are warned that something might be amiss. The value of this approach is that no client updates are required to display the safety tips because they appear along with the other message content.
A case can be argued that it doesn’t really matter all that much if mobile clients didn’t support a feature like safety tips. Mobile clients are often used as triage devices to allow users to run through a busy Inbox as quickly as possible, leaving messages that need more time or processing until they can be accessed on a PC. It’s less likely that someone will fall for a phishing attempt using a mobile device (and if they do, their sanity might be questioned). In addition, because of dependencies on PC components, malicious code contained in malware might not be able to work on a mobile device.
Nevertheless, given the increasing importance of mobile apps in a cloud first, mobile first world, it is good to see that Microsoft has thought about how to surface safety tips in as broadly as possible.
Protected Email is Ignored
Inline safety tips depend on their ability to inject HTML or plain text into messages for clients to display. However, any interference with the content of an encrypted message renders that message void. Accordingly, EOP does not attempt to inject safety tips into messages protected with Information Rights Management (IRM), S/MIME, and PGP.
Ignoring protected messages is not a problem. Spammers depend on their ability to send millions of messages in a short time and depend on the fact that some small percentage of those messages will penetrate defenses and arrive in user inboxes. It is highly unlikely that a spammer will send encrypted messages because of the extra complexity and processing power required to encrypt spam. It’s a question of cost-benefit. Too much trouble for too little return.
Disabling Safety Tips
Like any technology, there are probably those who don’t care for safety tips and will want to turn them off. Safety tips are controlled by a setting in a content filter policy. Every Office 365 tenant has a default content filter policy where the InlineSafetyTipsEnabled determines whether inline safety tips are on or off. You can’t disable the interactive safety tips used by OWA; these are always enabled whether you like them or not.
It doesn’t seem like a good idea to disable inline safety tips, but if you really insist, the instructions are online. Rather than wading through multiple levels of GUI, it’s quickest to twiddle the setting with PowerShell using the Set-HostedContentFilterPolicy cmdlet. For instance, this command disables safety tips for all mailboxes covered by the default content filter policy:
[PS] C:\> Set-HostedContentFilterPolicy -Identity "Default" -InlineSafetyTipsEnabled $False
Being Safe is Good
I like the thinking behind safety tips. It’s a simple yet powerful way to indicate to users that a message might not be all that it seems. Hopefully, those who see red safety tips react appropriately. Those who don’t and plunge into the mad world of Nigerian 419 scams and other email attacks probably deserve what they get.
Follow Tony on Twitter @12Knocksinna.
Want to know more about how to manage Office 365? Find what you need to know in “Office 365 for IT Pros”, the most comprehensive eBook covering all aspects of Office 365. Available in PDF and EPUB formats (suitable for iBooks) or for Amazon Kindle.