Windows Server 2016: Short-Lived Active Directory Group Membership
In today’s Ask the Admin, I’ll show you how to temporarily add users to Active Directory groups.
The Just-in-Time (JIT) administration model was introduced in Windows Server 2016 and allows system administrators to grant users privileges for a limited period of time. Adding to PowerShell Just-Enough-Administration (JEA), which restricts users to a pre-defined list of cmdlets, parameters, and modules in a PowerShell session, the JIT model has two objectives. The first is to prevent privilege creep where users are granted elevated privileges for much longer than necessary or indefinitely. And secondly, to avoid permanently assigning privileges that might only be required for short periods of time.
The ability to add users to groups with a time-to-live (TTL) value is a feature of the JIT model. This can be useful in scenarios where you do not have the resources to set up Microsoft’s recommended infrastructure for JIT administration but would still like to benefit from short-lived Active Directory (AD) group membership.
For more information on PAM in Windows Server 2016 and Microsoft’s recommendations for implementing JIT administration, see Windows Server vNext Privileged Access Management on the Petri IT Knowledgebase.
Use Short-Lived Active Directory Group Membership
I am not going to show you how to set up a Privileged Identity Management (PIM) trust or how to configure Shadow Principals but just how to add users to AD groups and have them automatically removed after some time.
Before you can use short-lived AD groups, you need to enable Privileged Access Management, which is an optional AD feature. The changes made to your domain when you add the PAM feature are irreversible. The PAM feature is designed to be used in bastion domains and not production domains, so you should decide whether you want to add it to your production domain.
Log in to a domain controller using an account that has permission to change the AD schema. Replace ad.contoso.com with the name of the domain you want to update.
Enable-ADOptionalFeature ‘Privileged Access Management Feature’ -Scope ForestOrConfigurationSet -Target ad.contoso.com
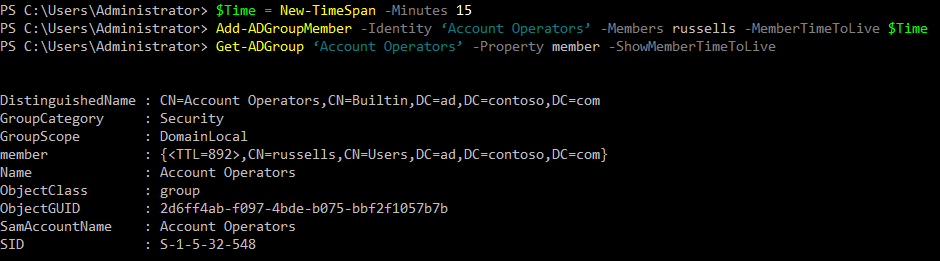
Now let’s add an account to the Account Operators group with a TTL of 15 minutes. Replace russells with the name of the AD account you want to add to the group.
$Time = New-TimeSpan -Minutes 15 Add-ADGroupMember -Identity ‘Account Operators’ -Members russells -MemberTimeToLive $Time
To see whether the account was added, we can use Get-ADGroup to show the group members and their associated TTL values:
Get-ADGroup ‘Account Operators’ -Property member –ShowMemberTimeToLive
Note that the member property of the returned object shows the group members and their TTL values. In my domain, Account Operators only has one member. The TTL value is shown in seconds. If you run Get-ADGroup again after 15 minutes, you will see that the user account you added to Account Operators will have been removed.
Be aware that adding an account to special AD groups, like Account Operators, might cause the adminCount attribute for the user account to be changed to 1 if the account is in the group long enough for the AdminSDHolder mechanism to make the account a protected object. When the account is removed from the group, the adminCount attribute remains set to 1.




