
Key takeaways:
- W3LL, a sophisticated cyber threat group, has successfully targeted more than 8,000 Microsoft 365 corporate accounts across the US, Europe, and Australia.
- W3LL’s tactics include bypassing multifactor authentication (MFA) and employing convincing Microsoft Outlook animations to deceive victims into opening malicious attachments.
- To defend against such threats, organizations are urged to implement FIDO 2.0 authentication solutions, enforce strict access policies, and bolster email protection tools.
Security researchers have discovered a new threat actor that has been using a highly advanced phishing kit to bypass multifactor authentication (MFA) safeguards. The cyber threat group has successfully compromised over 8,000 Microsoft 365 corporate accounts across the US, Europe, and Australia.
According to a report released by Group-IB, the hackers had built a highly sophisticated phishing kit (W3LL Panel) with multifactor authentication (MFA) bypass capabilities. The security researchers believe that the custom tools were used to breach over 56,000 Microsoft 365 accounts between October 2022 and July 2023.
Group-IB found that the cyber threat group targeted several industries, including IT, healthcare, legal services, manufacturing, consulting, and financial services. The researchers estimate that the W3LL crew had generated more than $500,000 during the last 10 months.
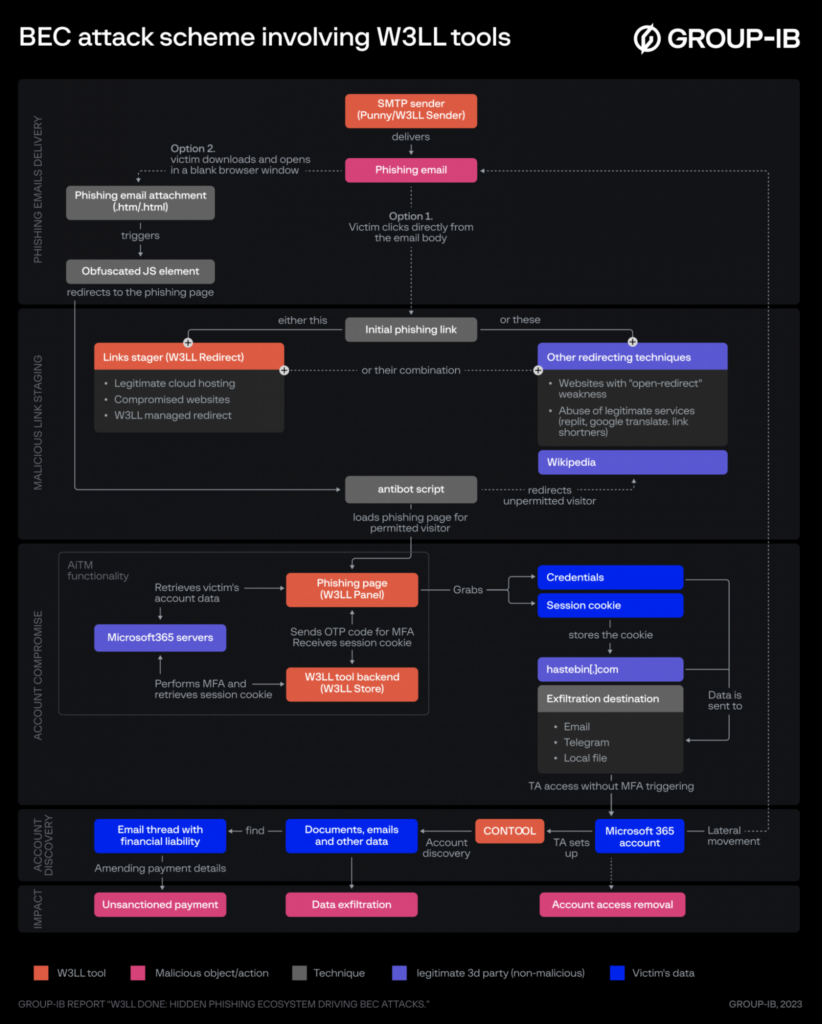
The attacker first gained access to a mailing list of potential victims and used the W3LL custom email validator tool to scan the list. Then, the hackers used additional custom tools (such as link stagers and phishing kits) to create a phishing lure.
“Once the victim has downloaded and accessed an attachment, a new blank browser window opens with a genuine-looking MS Outlook animation designed to make the victim think that the action is legitimate,” Group-IB explained. “What the phishing attachment actually does is load a W3LL Panel phishing page in the newly opened window.”
Group-IB suggests a layered defense approach to block W3LL phishing attacks
The phishing toolkit uses Adversary-in-the-Middle (AitM) attacks to steal session cookies and Microsoft 365 credentials. Finally, the attacker could abuse the unauthorized access for malicious activities such as malware distribution, impersonation, and data theft.
Group-IB recommends that organizations should take a layered approach to minimize the risk of cyberattacks. Enterprise customers should implement FIDO 2.0 authentication solutions and enforce strict conditional access policies. It’s also advised to configure additional email protection tools and review security policies.


