Using Microsoft 365 Defender Threat Analytics to Improve Security
In this article, I’m going to describe how to use Microsoft 365 Defender Threat Analytics to improve security in your organization. Over three Petri articles, we’ve dived into what Microsoft Defender for Endpoint (MDE) is, how you can migrate to it, and how it should be configured.
Part 1: Understanding Microsoft Defender for Endpoint and How It Protects Your Data
Part 2: How to Plan for Microsoft Defender Endpoint Deployments and Migrations
One thing remains: how you should use it in your ongoing security operations. This is where things extend beyond ‘just’ MDE and onto Microsoft 365 Defender as the larger extended detection and response (XDR) platform and security portal. This is important because to truly leverage MDE’s capabilities, we must understand how it integrates with the rest of the platform, and protect against threats as they move across the environment.
What is Extended Detection and Response (XDR) in Microsoft 365 Defender?
Extended Detection and Response (XDR) is a feature in Microsoft 365 Defender that unifies the protection, response, and protective capabilities of four core security services:
- Microsoft Defender for Endpoint (MDE)
- Covered in-depth over the last three parts of this series, MDE ultimately focuses on protecting your endpoints such as client computers, servers, and mobile devices.
- Microsoft Defender for Identity (MDI)
- Agents are deployed to your on-premises Active Directory environment to alert you about known attacks and suspicious behavior as they pertain to identity. For example, suspicious object access or movement of accounts across the domain.
- Microsoft Defender for Office 365 (MDO)
- MDO is often compared to conventional email security gateways but it can be so much more. In addition to protecting against dangerous email, it can do the same for SharePoint Online/OneDrive for Business files, as well as educate your users with phishing training.
- Microsoft Cloud App Security (MCAS)
- As SaaS usage grows, MCAS offers a way to monitor your multi-cloud estate and proactively control it. You can also integrate MCAS with your endpoints and network appliances to monitor traffic for shadow IT use.
By combining signals across these, attacks that transverse just one “entity” can be monitored for a big picture view of what’s going on, with improved response capabilities. Additionally, Exchange Online Protection and Azure Active Directory (AD) Identity Protection are integrated, providing signals and remediation. These XDR capabilities are then managed in the Microsoft 365 Defender portal at security.microsoft.com.
Microsoft 365 Defender alerts vs incidents
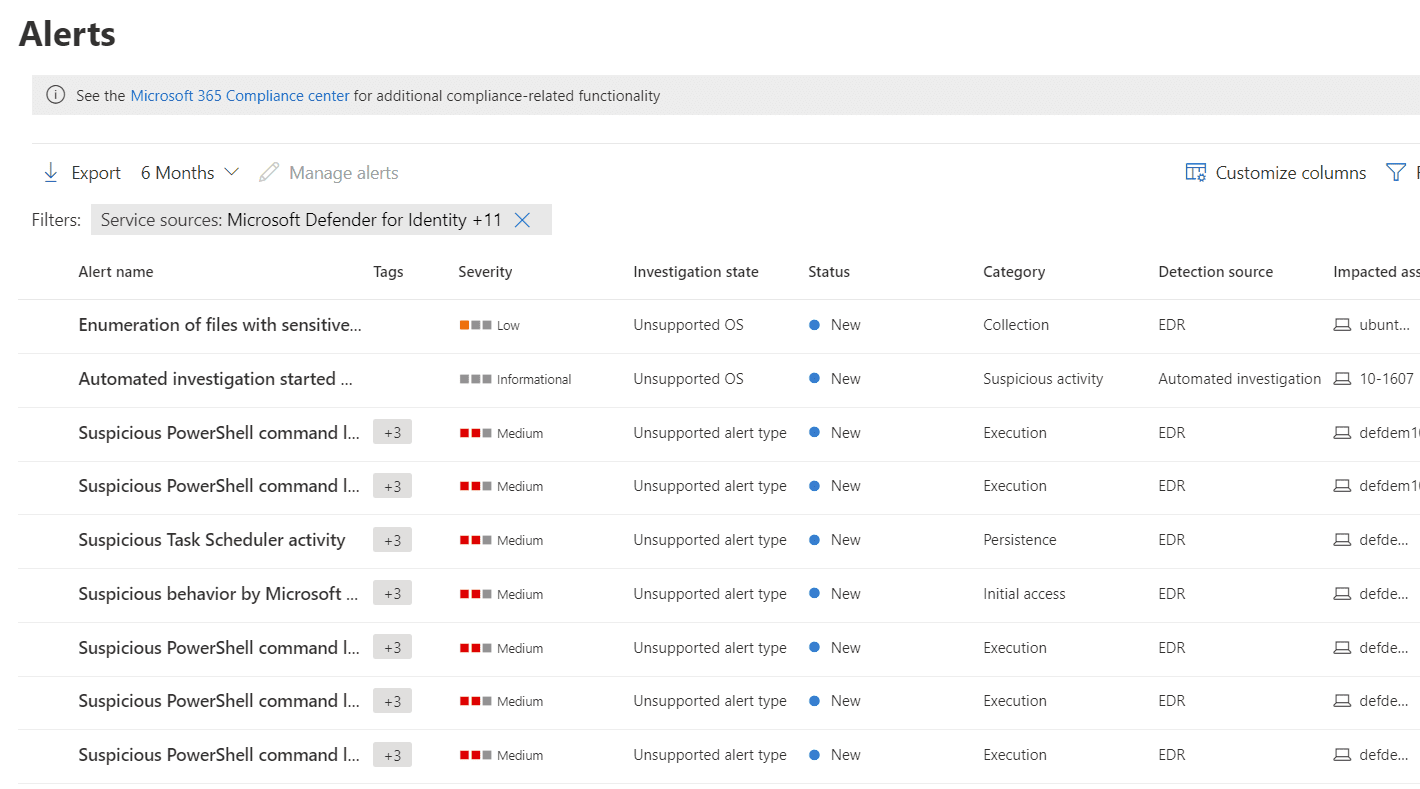
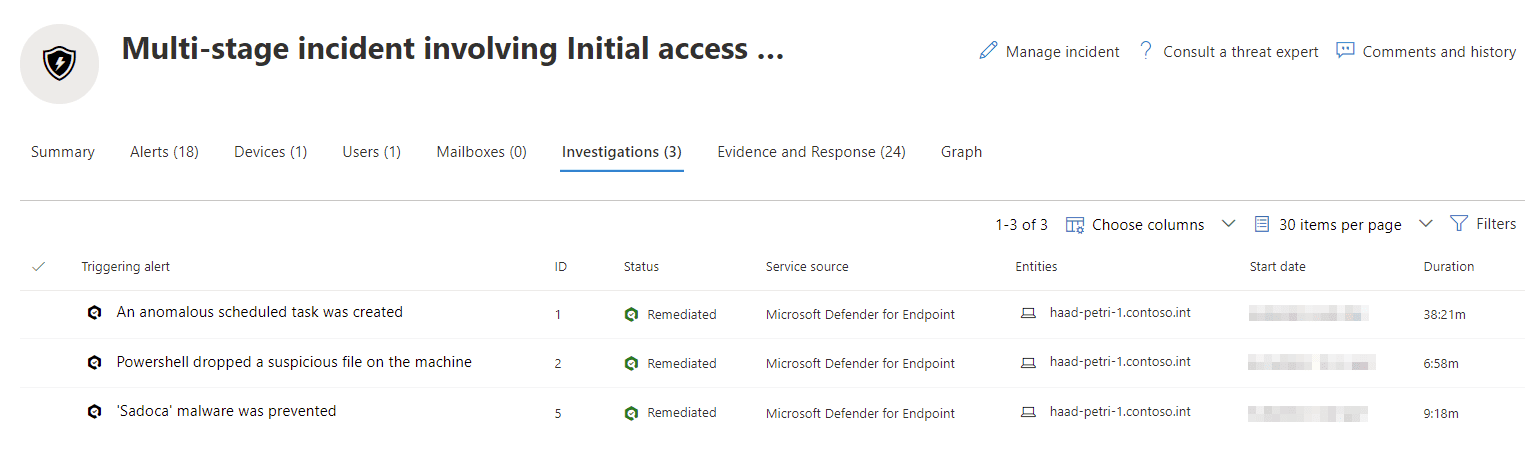
Think of a Microsoft 365 Defender alert as the lowest level of something worth knowing about. For example, a single instance of a suspicious Task Scheduler entry being created, or an abnormal number of files being deleted in Office 365. Alerts can be across the list of services described above. On their own, alerts may not mean much and, at any great scale, would become hard to manage and correlate.
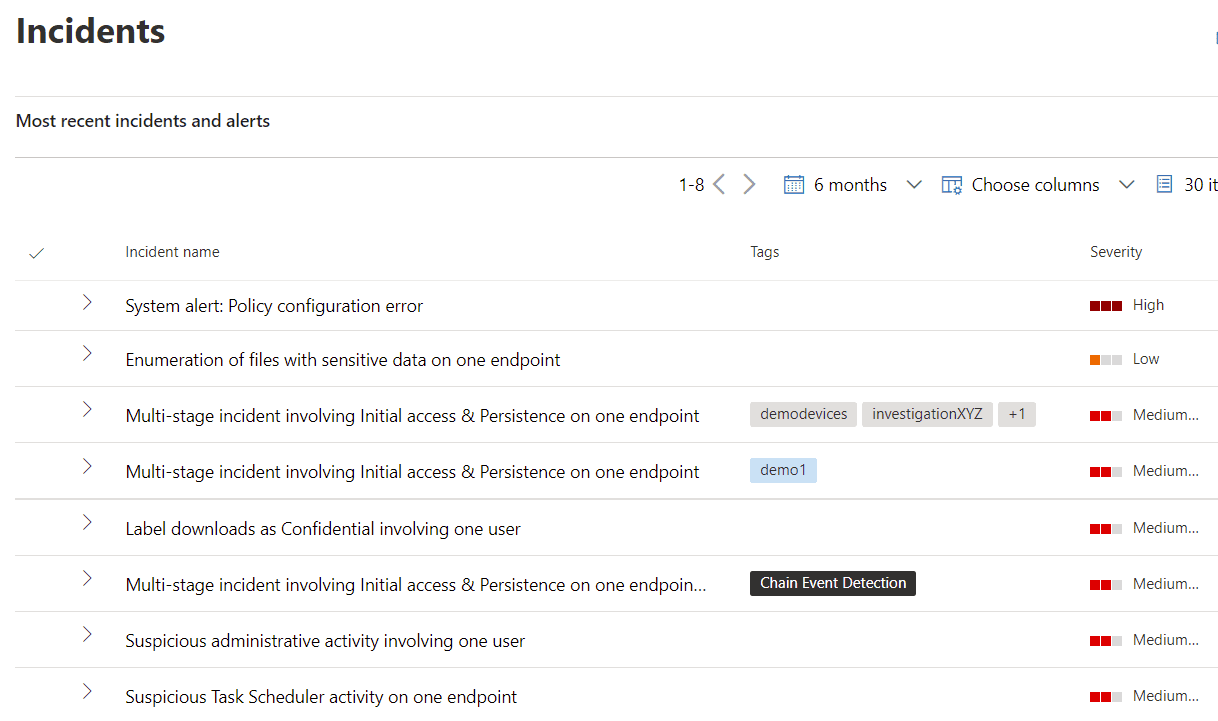
This is where incidents come into play. These are aggregations of alerts into a container that associates them all, using threat intelligence, for easier management and response. For example, if the same user is involved in the alerts for suspicious Task Scheduler items and abnormal levels of file deletion, and these alerts happen in close succession, this might form an incident.
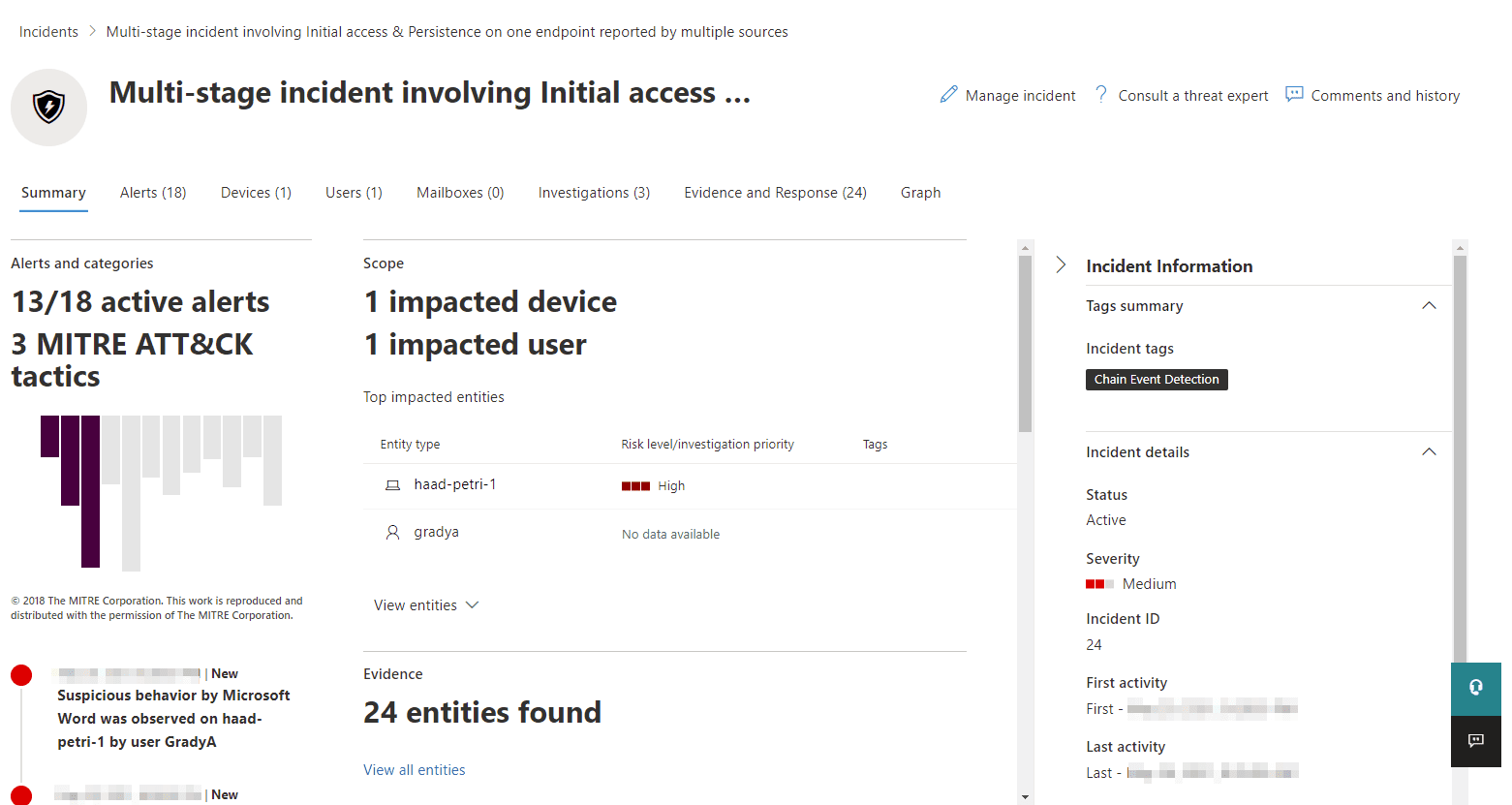
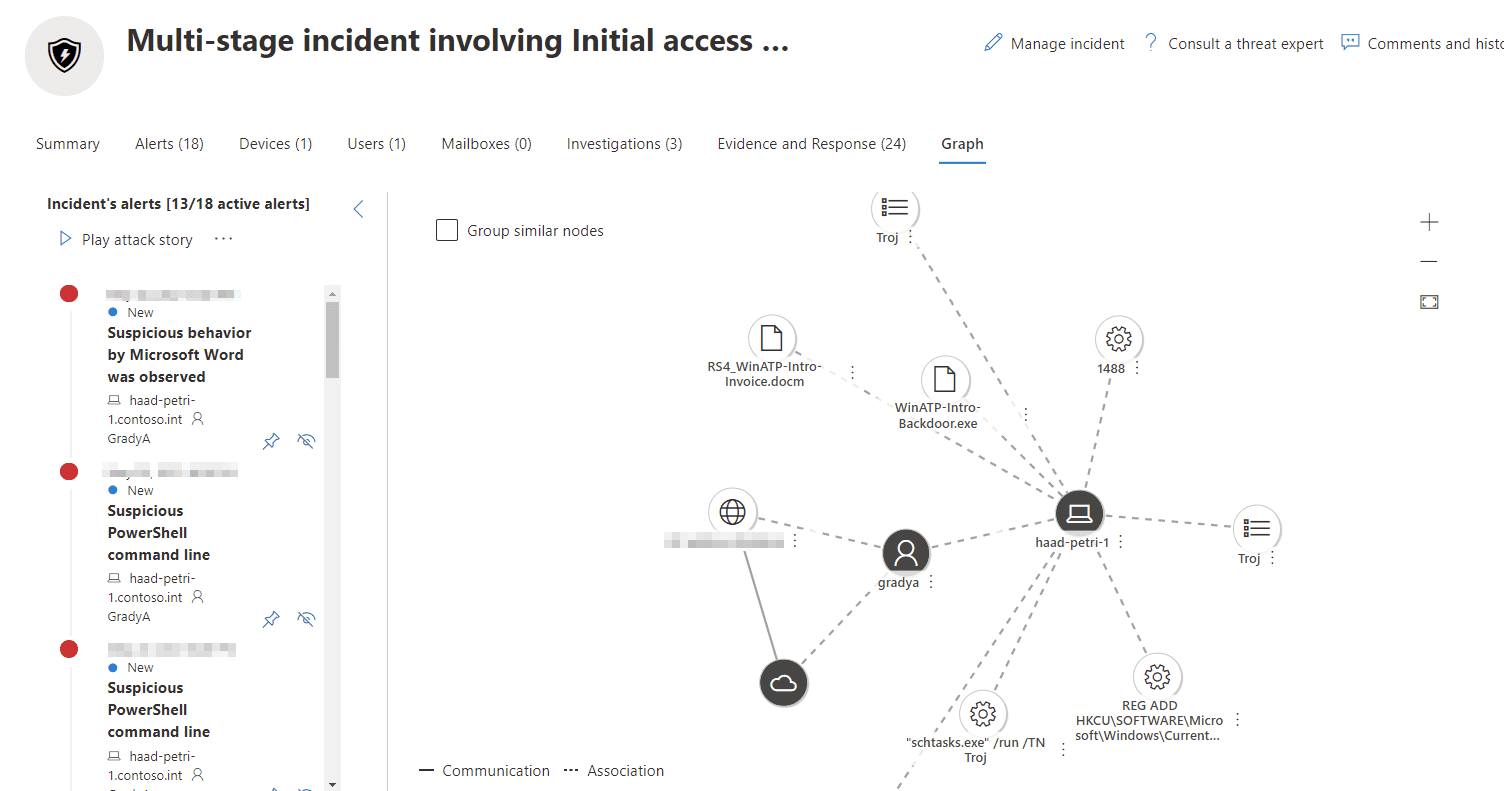
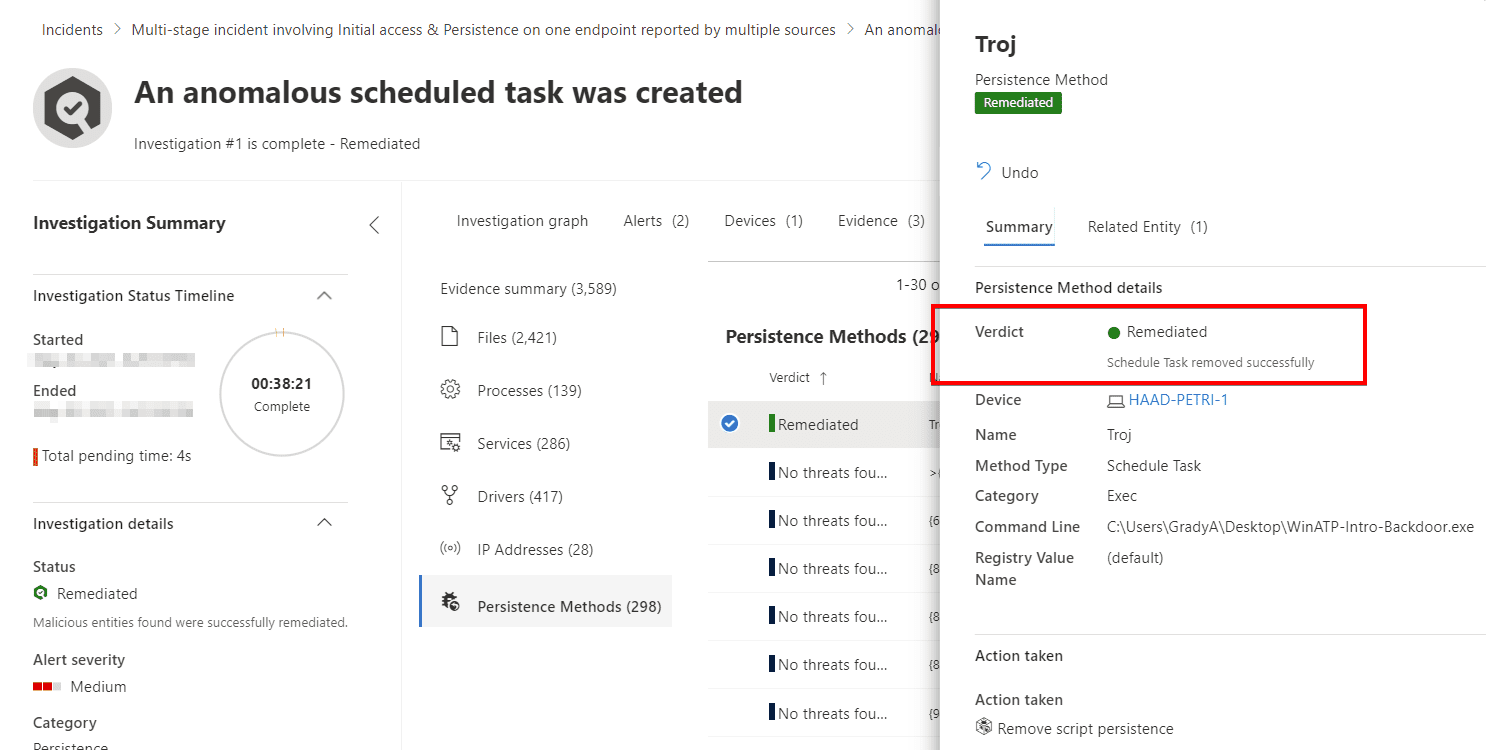
Using the example of a malicious Word document that has dropped a trojan and created a scheduled task, the graph does the job of painting the picture of what’s happened. It presents this in chronological order via the attack story and visualizes it by depicting the evidence, entities, and how they relate to each other in the attack.
Then, based on discoveries, the investigation system can remediate by killing processes, quarantining dangerous files, or, in the case of our example, removing a scheduled task. The work the investigation does is logged for you to review the evidence, and a log that contains what was investigated and done.
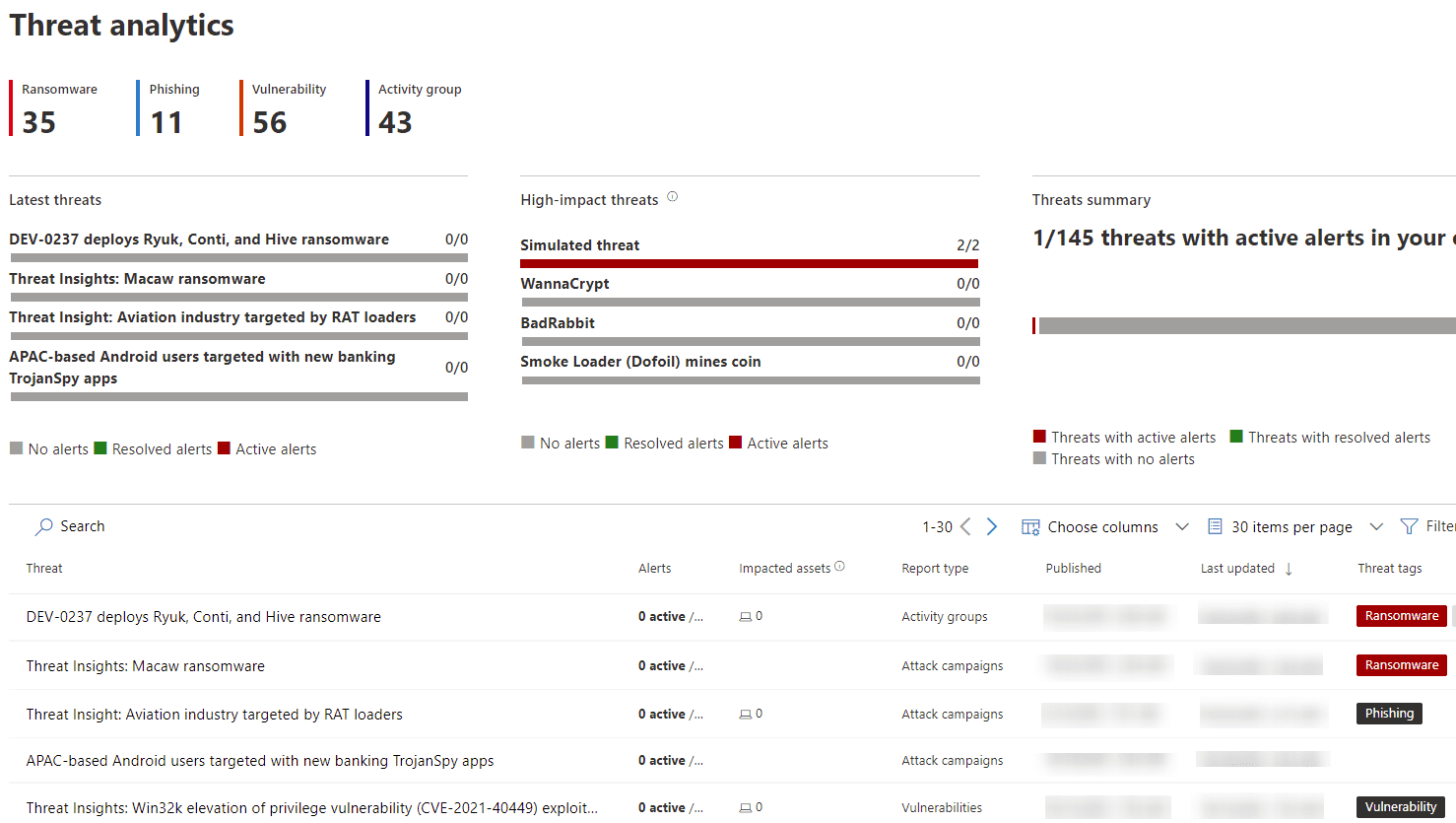
Vulnerability management
Threat Analytics is one way of proactively protecting your environment, and it leverages a feature of Microsoft Defender for Endpoint, managed via Microsoft 365 Defender, that requires additional explanation: threat and vulnerability management (TVM). It’s a given that unpatched software poses a risk, and TVM helps here by surfacing what software is outdated across our onboarded devices and what to do about it. TVM goes a step beyond just out-of-date or CVE-attached software, though, and also reports on the security posture of things like OS defaults.
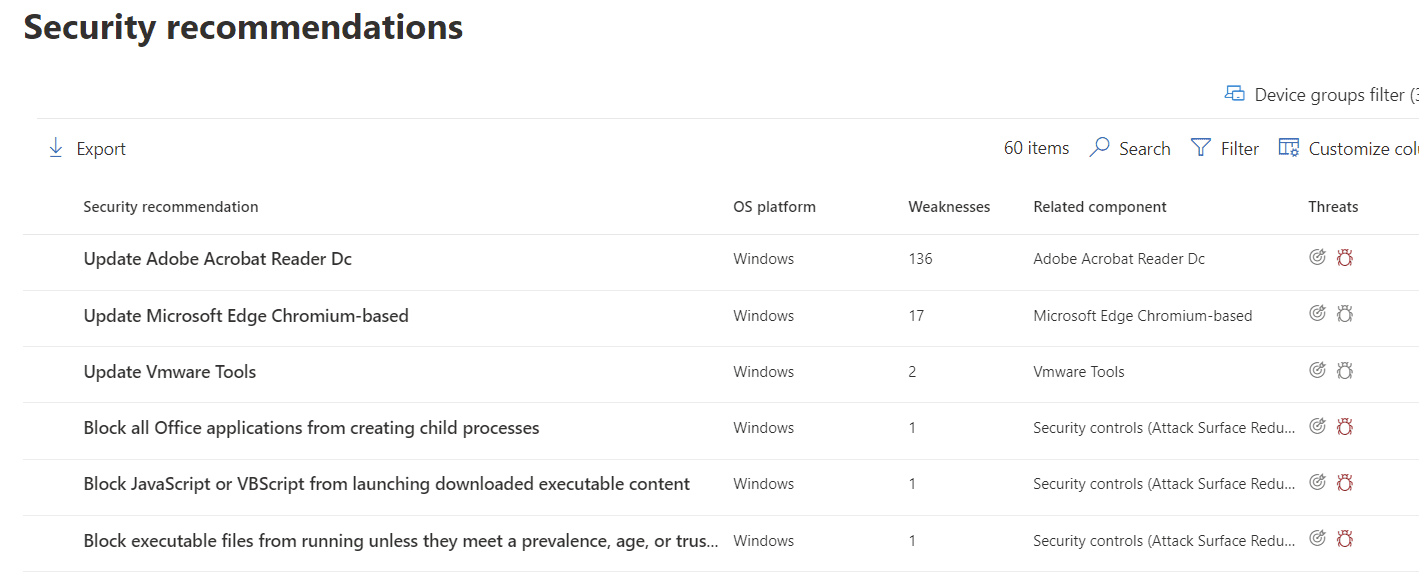
What this translates to is a very useful page in Microsoft 365 Defender called vulnerability management recommendations. This provides you with a to-do list on hardening and updating your environment. The recommendations tell you what to do rather than just telling you what the problem is. For example, you’ll see hardening recommendations such as disable ‘always install with elevated privileges’, as well as patching recommendations like update Adobe Acrobat Reader DC. If the software is recognized as at end of life, you’ll even get advice to completely uninstall it.
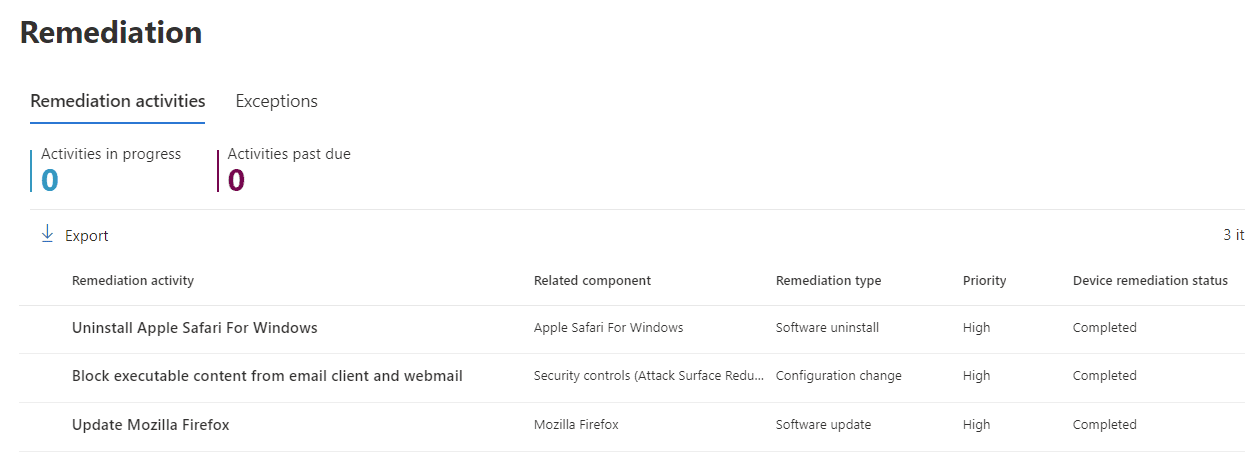
Within recommendations, you can harness Endpoint Manager integration with the request remediation option. This creates a ticket for Azure AD joined devices in Microsoft Endpoint Manager (MEM) to manage the recommendation through to completion: particularly useful in environments where different teams manage different elements.
Be proactive, leveraging capabilities like Threat Analytics and TVM
Managing your security posture and responding to threats is an ongoing operation. Deploying Microsoft Defender for Endpoint and starting with Microsoft 365 Defender is just that: the start. There are no “install it and its done” solutions to the ongoing security problems our industry faces.
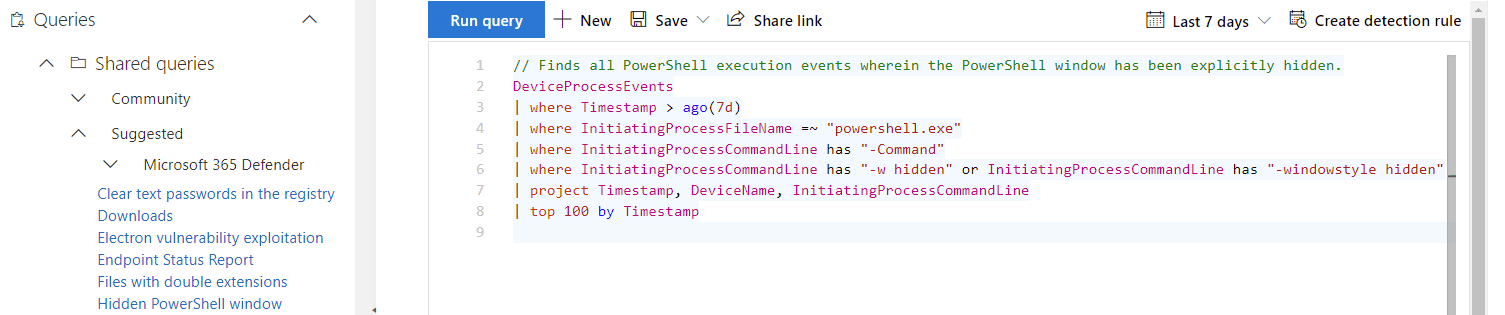
Through this blog series, however, you’ve hopefully learned how to start with Microsoft Defender for Endpoint. Alerts and investigations will keep you in the loop with what threats MDE has identified (and, potentially, auto-remediated), but you’ll probably need to go one step further and dive into advanced hunting to stay ahead of the game. Be proactive, leveraging capabilities like Threat Analytics and TVM too: the easiest threats to manage are ones you’ve already mitigated against.