Understanding Microsoft Defender for Endpoint and How It Protects Your Data
Microsoft Defender for Endpoint (MDE, previously known as Microsoft Defender Advanced Threat Protection) is Microsoft’s endpoint security platform that goes far and beyond the traditional anti-malware engine and firewall to protect against the modern cybersecurity threats an organization faces. An evolving solution since it was first announced in 2016, MDE is part of the Microsoft Defender extended detection and response (XDR) service (an overview of the entire service is available here).
Enough of the abbreviations and security buzzwords. If new to Microsoft Defender, a number of questions likely come to mind. Why should you trust Microsoft’s security offerings? Why should you care about MDE? What’s wrong with the antivirus and firewall I’ve been using for so long? And, if I jump to MDE, where should I start?
This article is the first in a four-part series in which we’ll answer those questions.
- In part one, we’ll explain what Microsoft Defender for Endpoint is exactly, trying to cut through the “fluff” and tell you specifically why it’s something you should be interested in.
- Then, you’ll find out what you need to know about migrating your existing organization’s antivirus or endpoint solution to MDE, based on lessons from the field.
- In part three, the vast number of security settings and features that make up the MDE “stack” will be covered, so you know where to start hardening your environment against threats such as ransomware.
- In the final part of the series, we’ll discuss where to go next. By this point, you’ll know how to establish your organization in MDE, but that’s just the beginning of the Microsoft Defender journey. You’ll find out about advanced features, as well as a sense of direction into other areas of the Microsoft Defender world, where you can protect Office 365, SaaS apps, and your Active Directory identity infrastructure.
The threat landscape
Sorry, a bit of a white lie earlier: there will be more three-letter abbreviations (TLAs) and buzzwords. I promise we’ll keep these to a minimum and only so you can understand the current threat landscape and how the cybersecurity industry is responding.
Petri contributor Aidan Finn did a great job summarising this back in 2015 when news first hit about Microsoft “Sonar”, which would go on to become Microsoft Defender for Endpoint (and several other names before that!). Fundamentally, as devices have become more mobile and the world has become more connected to the public internet, the attack vectors changed and how we respond to them had to change too. The days of a firewall appliance acting as a single network boundary or guardian are largely behind us, especially as a result of remote work’s acceleration since March 2020. Similarly, the days of traditional signature-driven antimalware software are past us, with the rate of new malware impossible to keep up with using such a system, which would also be poor at preventing fileless attacks. Whereas we historically cared about protecting specific executables running based on block-lists, the world now has no shortage of high-profile advanced persistent threat (APT) attackers.
These actors are organized and have the resource to fund and sustain long-term campaigns against targetted organizations. Those organizations may be in scope for the attacker for a number of reasons: primarily, being an easy target (e.g. an exploitable, internet-facing vulnerability picked up by a scanner), or the organization’s profile (think of spear-phishing campaigns for political or ideological reasons). The big concern at the moment for victims of APTs is ransomware, due to the enormous financial incentives.
The important takeaway is that modern attackers have such a vast resource on hand and the ability to attack with methods that traditional endpoint security solutions don’t detect. Think about the typical (dare I say, legacy) antivirus deployed across your organization. If someone gained access to an endpoint with legitimate credentials or (commonly) an exploit in something such as Remote Desktop Protocol, how would you know? Your antivirus might pick up on any strange executables from the exploit, but what if it’s a zero-day, and what if the attacker simply logged in like a normal user with leaked credentials? If they started conducting discovery on your infrastructure, traversing the environment, jumping from server to server or device to device, again with legitimate credentials and created scheduled tasks or startup entries that – to your antivirus – were not weaponized or produced malicious results yet, how would you know?
The point being, you need a service that can detect look at patterns of behavior across your environment, and generate alerts about it – or at least enough noise that you can identify strange goings-on.
How Microsoft Defender for Endpoint protects against modern threats
MDE is a lot of things, but primarily it is recognized for its extended detection and response (EDR) offering. You can think of EDR solutions as what happens after the traditional systems of operating system hardening and antimalware engines. Gathering a tremendous amount of telemetry about what’s going on in an operating system, Defender’s EDR capabilities identify potentially dangerous activities and create alerts about them. Alerts can originate from a number of sources, and when patterns start to emerge, Defender creates incidents that can it can automatically investigate and remediate against.
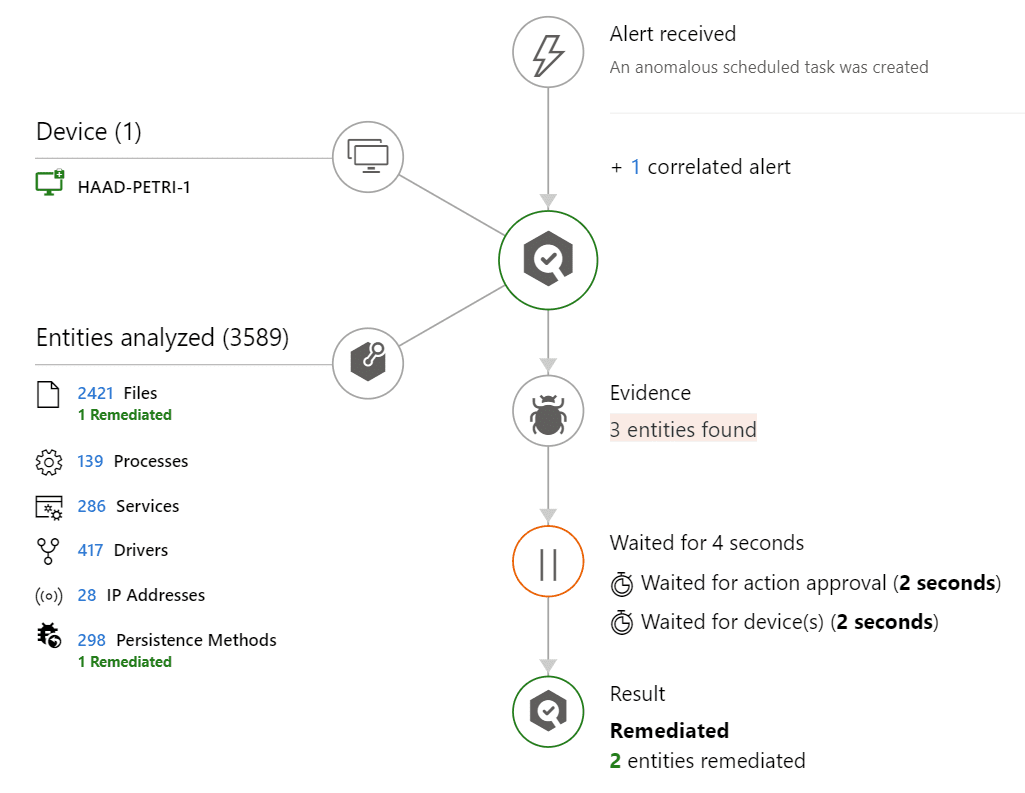
For example, an Excel macro spawns a PowerShell subprocess, which creates a Task Scheduler entry that runs another script when triggered, and this could happen across several devices. All the scripts and activities may not match the checks a traditional antivirus looks for (such as file hashes), but the EDR identifies the patterns of behavior – such as a strange new scheduled task. It then, automatically, looks into evidence and tries to answer the question: is there a threat, and should I do anything about it? In this example, other files, processes, drives, and services are analysed from the associated devices, as well as IP addresses communicated with, or known persistence methods. If you have enabled automatic remediation, it will then, for example, remove the scheduled tasks or take other remedial action.
All the telemetry collected to identify these threats is also held for security professionals to query themselves using a language called kusto query language (KQL) in a feature branded advanced hunting. This provides a powerful tool for bespoke alerts if certain types of activity are discovered, or for your own “hunting” into threats or behaviors that MDE is not automatically surfacing.
As well as this EDR capability and automated investigations/remediation, Microsoft Defender for Endpoint has a number of other pillars, as Microsoft describes its key features. Those include, but aren’t limited to, the following:
- The core antimalware engine (branded as next-generation protection) that powers a lot of MDE’s features on the endpoint
- Attack surface reduction (ASR) tools which harden the operating system by, for example, prohibiting certain types of actions altogether, such as the aforementioned example of Office generating child processes; or protecting your network traffic with web content filtering to block dangerous web traffic or types of websites against organizational policy
- An assessment called Secure Score for Devices, which, much like the “scores” found elsewhere in Microsoft 365, provides recommendations for securing your endpoint estate based on telemetry gathered. For example, to enable certain ASR rules.
- Threat and vulnerability management (TVM), which looks at your software (and, very recently, network appliance) inventory and lets you know what software needs patching (first and third party), what exploits it may be vulnerable to, and a system of managing those vulnerabilities, including opening tickets in Microsoft Endpoint Manager.
Why Microsoft?
Other vendors offer these types of security platforms, with all the EDR bells and whistles, so why go for Microsoft’s solution? First, let’s look at a reason C-level types may be interested.
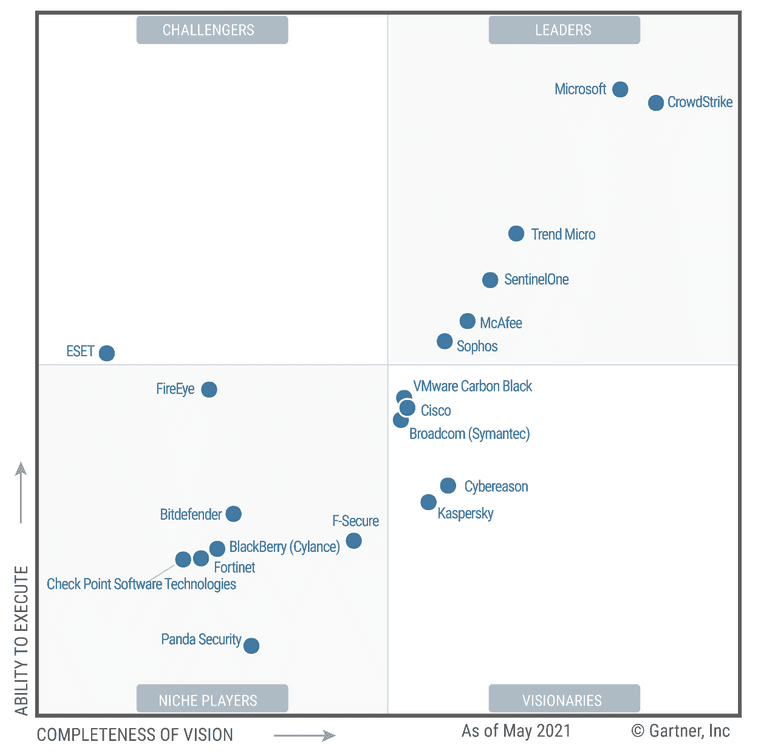
In the last publication of Gartner’s magic quadrant for endpoint protection platforms, excels in the top right corner; towering above most alternatives.
When you buy into Microsoft Defender, you need to look at the entire platform rather than “this feature vs. that feature” with other vendors. This is true of most Microsoft solutions, and what I mean by this is that there are plenty of other vendors out there that may offer software and services that beat the Microsoft Defender for Endpoint solution in certain specific areas, but not when we consider the whole picture.
Microsoft Defender for Endpoint is typically licensed as part of Microsoft 365 E5 or E5 Security (an add-on to Microsoft 365 E3). Included in these subscriptions are other elements of the Microsoft 365 Defender family. Without getting too much into those – that’s for another article – they protect against email threats, Office 365 files, your SaaS apps (including third parties), and on-premises Active Directory and VPN sign-ins. When you buy into the Defender platform, you’re getting built-in integration with all these areas of security concern out-of-the-box. Having multiple vendors and solutions that all speak a different language introduces overheads: the initial setup, ongoing management, and (frankly) the security risk of ensuring all these different systems talk to each other using something like a security information and event manager (SIEM). Whereas lots of vendors and different solutions have been seen by some as best practice, in reality, the opposite is probably true: with the rise of APTs, you need different areas of your security infrastructure to converge administration, reporting, and investigation. One heavily resourced, constantly evolving suite that covers it all is what you should be looking to introduce.
Where does Defender for Endpoint fall short?
No product is perfect, and although MDE is a great security solution, you need to be aware of some weaknesses, or at least “gotchas”.
Firstly, let’s look at OS support. Defender for Endpoint has come leaps and bounds recently, introducing support for Linux servers and macOS as well as Windows. If you still have “down-level” Windows operating systems, however, you won’t get feature parity on those with later versions. Starting with Windows 10, the EDR elements of MDE are built-in, with Microsoft Defender Antivirus integrated with the OS. Windows 7 SP1 and 8.1 are supported, but only insofar as you’ll get alerts and telemetry: the R within EDR is missing, as it cannot perform any of the automatic responses discussed earlier. For Windows 10, you’ll also need to ensure feature version 1709+ is installed. This is also the case for Windows Server versions of the same era: 2008 R2 SP1, 2012 R2, and 2016 cannot support automatic response, but you’ll still get telemetry and notifications of suspicious behavior.
Sticking with OS support, although macOS is now supported, it also lacks feature parity with Windows 10. Automatic investigations cannot remediate, but you will at least get the telemetry and alerts. Windows 10 is also the only desktop OS to support a feature called network protection, which integrates SmartScreen technology across the whole networking stack rather than just the browser. This is what powers web content filtering and the like, so that you can, for example, blanket ban certain categories of website, such as adult material or legally dubious.
You’ll also want to know that there’s a bit of a misleading indication as to how long you can work with the data and telemetry MDE gathers. When you first set up your environment, you can choose to store data for up to 180 days, however, this only applies to alerts and incidents; it does not apply to the advanced hunting data, which only lasts for one month.
Lastly, how you configure endpoint settings with MDE is perhaps not as consistent – or obvious – as with other vendors. Other vendors typically offer one console to manage all things: reports, configuration, etc. With MDE, the service is administered from a web portal, security.microsoft.com, however, the actual settings that apply to devices, such as scan frequency, the attack surface reduction rules, etc, are configured using other endpoint management tools such as Endpoint Manager or Group Policy. That can break your flow and, worst case, cause confusion or inconsistencies. It does, however, allow you to delegate responsibilities a little more effectively, as in large enterprises the security team and endpoint management team can be separate entities.
What’s next?
In the next article of this series, we’ll get into how you can build an approach to change your existing, traditional security software with Microsoft Defender for Endpoint. We’ll cover the various operating systems it supports, including servers and mobiles. You’ll learn how best to plan the move to MDE, minimizing any unprotected windows as you change the solution.
Related Articles:
- How to Protect Windows Devices with Microsoft Defender for Endpoint
- Protect iOS and Android Devices with Microsoft Defender for Endpoint