Using Azure Key Vault to Encrypt Data in the Cloud
Azure Key Vault gives organizations access to Hardware Security Module (HSM) appliances in the cloud, providing the ability to better secure VMs and SQL Server data. In this Ask the Admin, I’ll look at some of the potential use scenarios.
Security is often cited as the primary concern for organizations looking to move data to the cloud. But if carefully planned, cloud solutions can provide a secure platform on which to host corporate data. At the end of 2014, Microsoft released Azure Key Vault in public preview to several regions, providing scalable and secure Hardware Security Module (HSM) appliances in the cloud, giving customers access to a technology which can sometimes be costly to implement on premise.
Azure Key Vault
Using FIPS-validated HSMs, Azure Key Vault provides a cryptographic key management service that can be used to store encryption keys or other sensitive information, like passwords and SQL connection strings. Case uses include storing sensitive password information for your line-of-business applications running in the cloud, improving SQL Server encryption, and full-boot volume BitLocker encryption for Azure virtual machines.
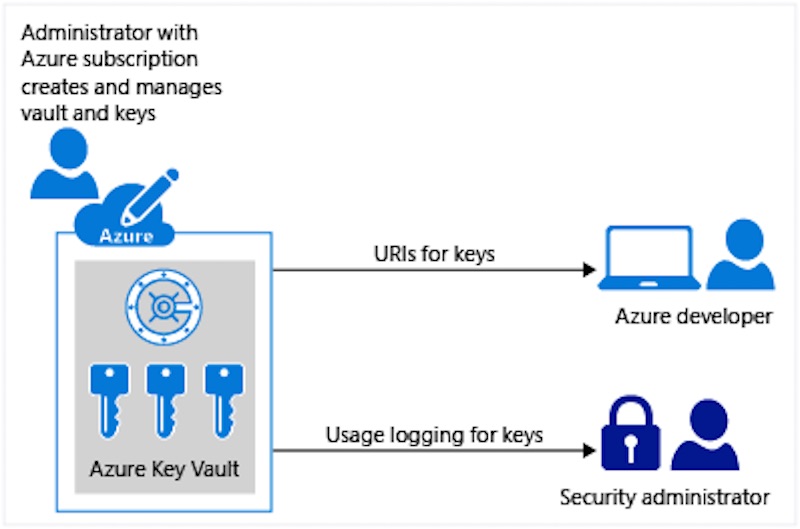
Azure Key Vault allows organizations to separate encryption keys, operations, development and auditing duties, for applications running on premise and in the cloud. Rather than embed secrets in applications, which might expose them to operations staff and developers, only applications and host VMs are able to see generic secrets, such as SQL connection strings. Extra protection is provided if an app needs access to an encryption key: it calls the Azure Key Vault service, and the cryptographic operation is performed for the app without the key ever being revealed.
Encrypting VMs
Microsoft doesn’t support BitLocker in the cloud, because there’s no way to access Trusted Platform Modules (TPMs), which are required to store encryption keys. However, CloudLink SecureVM can enable boot volume encryption and a fully automated boot cycle, utilizing Azure Key Vault if VMs are located in the cloud; or RSA Data Protection Manager or Active Directory to store encryption keys in hybrid/private cloud scenarios.
CloudLink Center is a virtual appliance that can be configured to use Azure Key Vault as its key store. A small agent is deployed to each VM and boot volumes. Additional volumes can be encrypted with BitLocker from CloudLink Center, if required. Apart from specifying the IP addresses of the VMs to be encrypted in CloudLink Center, no other configuration is required to get the solution working. Linux VMs are also supported, utilizing native encryption technology.
SQL Server Encryption
Azure Key Vault can be used in conjunction with SQL Server Extensible Key Management (EKM), which provides extra protection for keys used with Transparent Data Encryption (TDE), Column Level Encryption (CLE), and encrypted backup — three technologies used to protect SQL data at rest. TDE encrypts data and log files, and CLE is used to encrypt columns of data.
Extensible Key Management provides a means of protecting SQL Server’s symmetric data encryption keys, used for bulk data encryption, with an asymmetric key stored in an external cryptographic provider, giving organizations greater flexibility in managing keys and data by clearly delineating administrative duties. SQL Server Connecter can be downloaded from the Microsoft Download Center and is used to connect SQL to Azure Key Vault. Not only can Azure Key Vault be used to provide protection for SQL Server encryption keys in the cloud, but also to protect on premise SQL workloads.


