Why You Need to Upgrade from Windows XP (and Windows Server 2003)
Support for Windows XP ends in April 2014, with Windows Server 2003 following in July 2015. But what does this mean for users and organizations still running these products? Microsoft recently warned that Windows XP users face ‘zero-day’ vulnerability forever on their PCs, as once the company stops releasing security updates, the defenses built-in to the aging OS won’t be enough to fend off today’s sophisticated attacks.
Windows’ OS Infection Rate
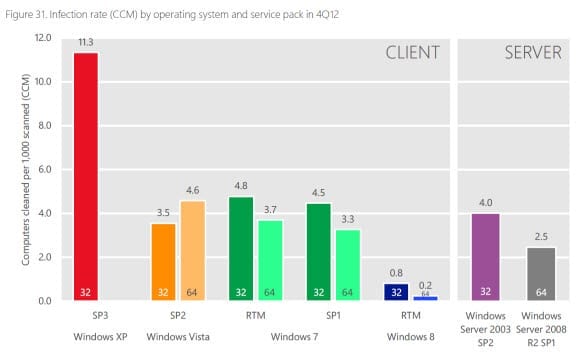
What struck me was not this piece of unsurprising information, but the results of Microsoft’s Security Intelligence Report 14 from the fourth quarter of 2012, which uses data gathered directly from the install base of each OS. As you can see in the figure below, while it’s no surprise that Windows XP is considerably more prone to infection than later versions of Windows, it’s twice more likely to be infected than Windows Vista. The data in the report is normalized, so a sample of one thousand computers was analyzed for each operating system version.
Windows 8 has a particularly low infection rate, but that could be due to the fact the OS had only just been released at the time the report was published, when attacks that specifically target the improved defenses of the OS were few. Additionally, it’s worth remembering that Windows 8 is the first version of Windows to include signature-based malware protection out of the box. With the imminent release of Windows 8.1, we may see those figures improve further as Windows Defender adds network-level inspection to the mix.
Microsoft’s Security on the Server
Microsoft wasn’t able to collect enough data on Windows Server 2012 to provide reliable measurements to include in the report. However, we can see that Windows Server 2008 R2 SP1 is infected a lot less than Windows Server 2003 with Service Pack 2, and I think we can safely assume that Windows Server 2012 will show good results in the next report.
As servers are not generally used interactively in the same way as desktop PCs, with the exception of terminal servers, they are at less risk. So replacing Windows XP might be more of a priority than upgrading to Windows Server 2012. Furthermore, it may not be easy for organizations to move legacy applications away from old versions of Windows Server for compatibility reasons.
Nevertheless, you should consider planning to upgrade Windows Server 2003 to Windows Server 2012 before 2015. This may also allow you to utilize Server Core, which provides a more secure OS than the GUI version of Windows Server. If it’s not possible to move from Windows Server 2003, special attention will need to be paid to securing the server post-2015.