Securing Remote Virtual Machines Using Azure Bastion
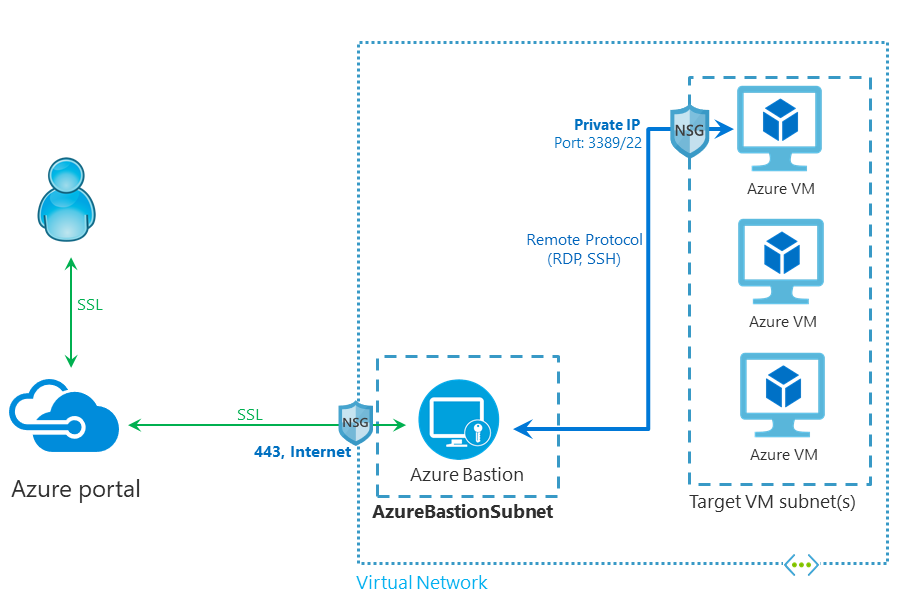
In June 2019, Microsoft announced Azure Bastion. As a managed Platform-as-a-Service (PaaS) offering, Bastion lets you connect directly to virtual machines (VMs) without assigning them a public IP address. It acts as a jump server that forwards secure SSL connections from a browser to VMs. General availability was announced at Microsoft Ignite last year.
Check out this link on Petri for more information on virtual machines.
In this article, I’ll explain in detail how Bastion works and how to configure it. You will learn how to create a Bastion host manually and how to create a Bastion by changing a VM’s settings.
Understanding Azure Bastion and remote connection protocol security
Remote Desktop Protocol (RDP) and Secure Shell (SSH) are both protocols used for accessing virtual machines (VMs) in the cloud. Azure uses RDP for Windows VMs and SSH for Linux. RDP is less than ideal as a secure protocol and it continues to see Microsoft regularly issue patches.
Bastion is useful in situations where it wouldn’t be cost effective to deploy your own secure connection solution in Azure or if you can’t connect to an Azure VNET using a virtual private network (VPN). If you are using Azure Virtual Desktop (AVD), you don’t need Bastion. VMs provisioned using WVD are already protected using an architecture like that provided by Bastion.
How to deploy Azure Bastion
First check that the Azure region you want to use supports Bastion. You can find an up-to-date list of supported regions on Microsoft’s website here. You’ll also find detailed instructions on how to create an Azure Bastion host.
Create a Bastion host resource manually
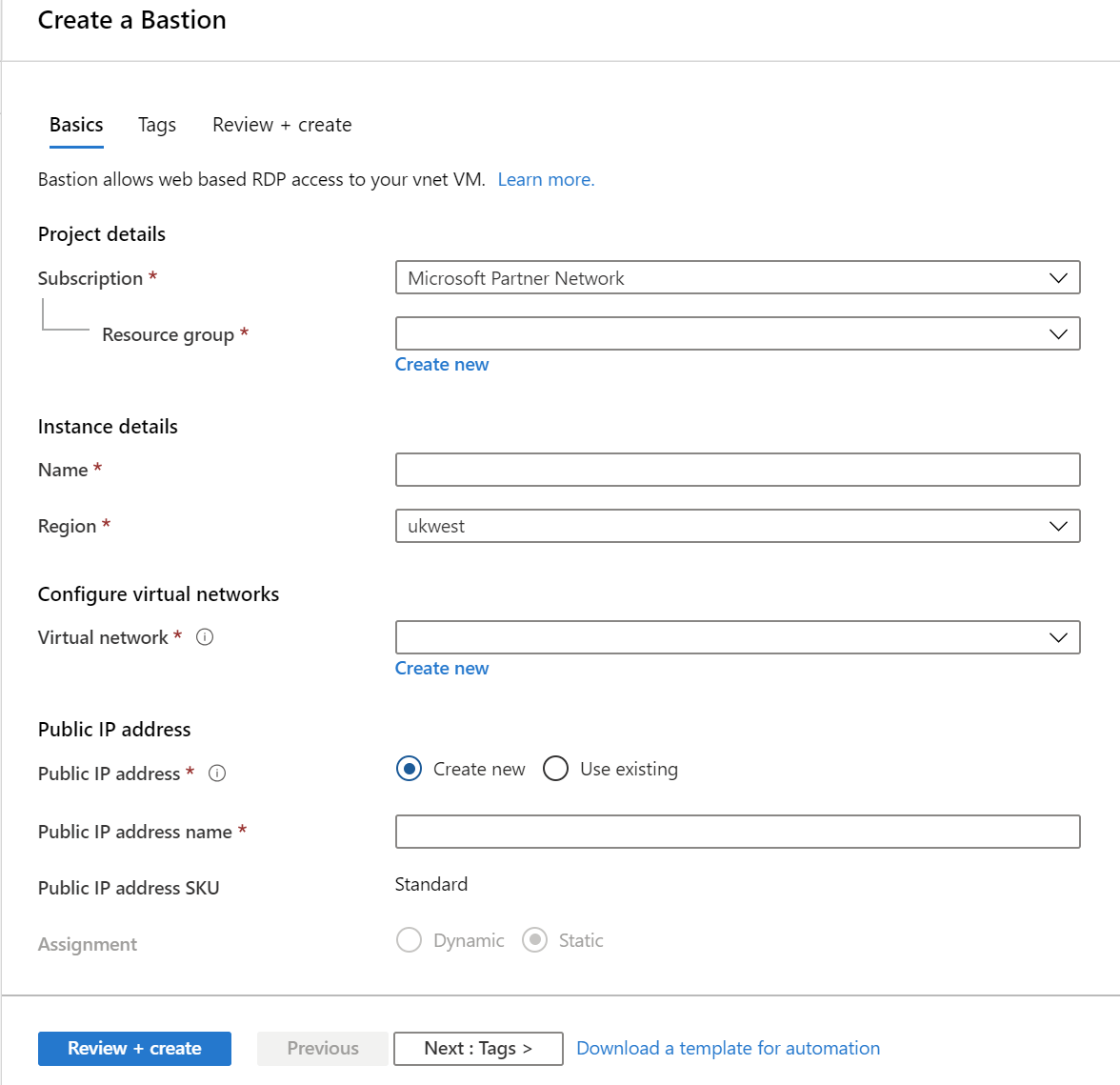
There are two ways you can set up Bastion in the Azure management portal. The first is to create a Bastion host resource manually. The process involves three main steps:
- Select a subscription, resource group, giving the Bastion host a name and assigning a region.
- Select an existing VNET or create a new one. The VNET must contain a subnet called AzureBastionSubnet with a prefix of at least /27.
- Finally, you need to assign a public IP address. You can select an existing IP address or create a new one.
Once the three main configuration steps are completed, you can also assign tags and review the settings before provisioning.
Create an Azure Bastion host by changing VM connection settings
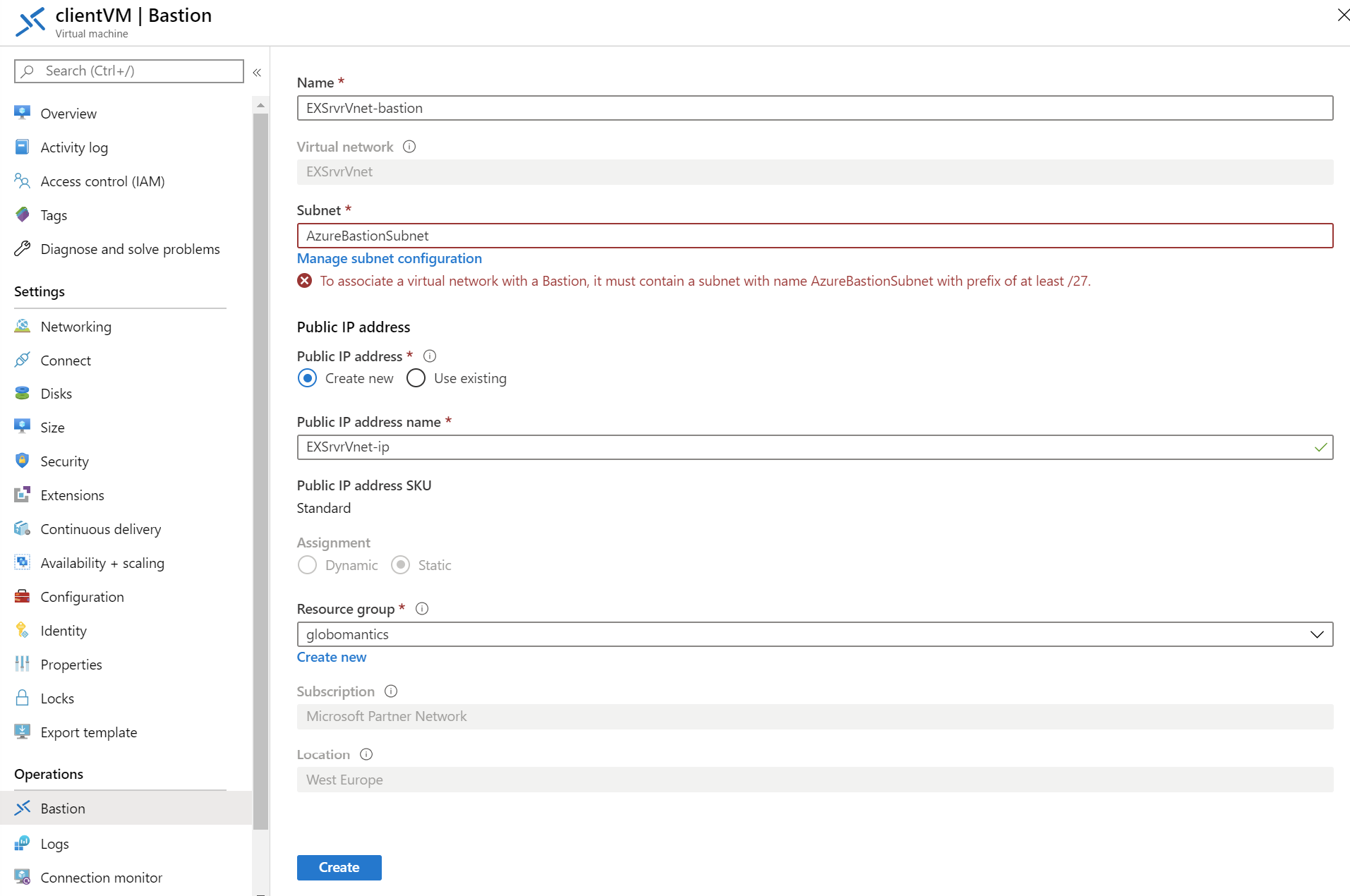
Alternatively, you can create a Bastion from the settings pane of an existing VM. Regardless of whether you have a Bastion host already deployed in your subscription, when connecting to a virtual machine using the Azure management portal, there is the option to select Bastion instead of RDP or SSH.
Assuming a Bastion isn’t already associated with the VNET where the virtual machine is located, you will be given the opportunity to create a Bastion. The process differs slightly from that described above in that you only need to specify the Bastion subnet, public IP address, and resource group.
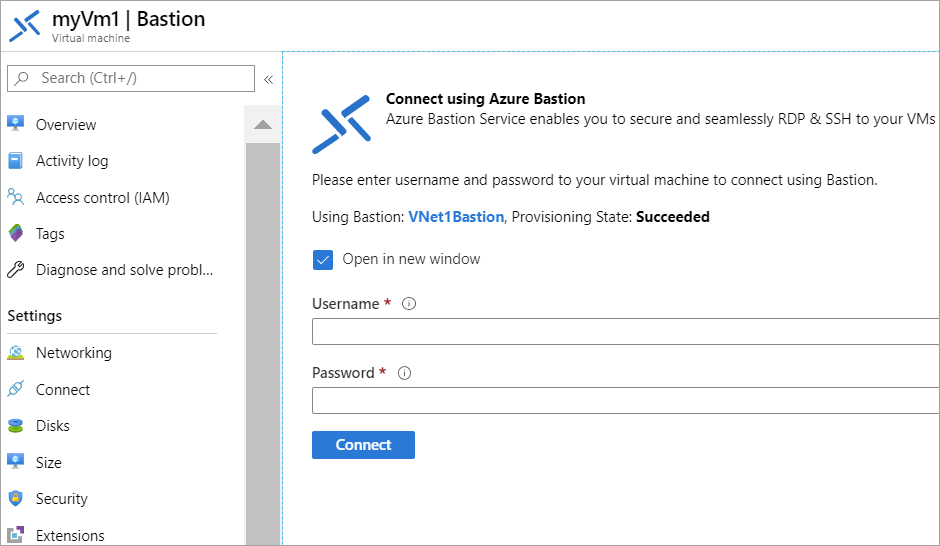
Once the Bastion has been created, regardless of the method, you can connect securely to the VM by selecting Bastion instead of RDP or SSH when connecting via the Azure management portal from Edge or Google Chrome.
What else should you know before setting up Azure Bastion?
There are some disadvantages to using Bastion. It’s not free, so be sure to check out pricing before you commit. IPv6 isn’t supported and nor are some advanced RDP features. Only text copy and paste are currently available. If you want to use features like drive redirection, you’ll need to connect to your VM directly using RDP. We also have a separate guide on using Azure Bastion native client support to log into VMs with the Windows RDP client. You can find a full list of frequently asked questions about Azure Bastion on Microsoft’s website.