
Key Takeaways:
- Microsoft has issued a warning about Forest Blizzard (STRONTIUM), a Russian state-sponsored hacking group, actively exploiting a critical Outlook flaw to gain unauthorized access and steal sensitive data.
- The hackers persist in targeting unpatched Exchange Servers, focusing on government, transportation, energy, and non-government organizations in the US, Europe, and the Middle East.
- Microsoft urges organizations to apply patches and enforce multi-factor authentication.
Microsoft has warned customers that a Russian state-sponsored hacking group (dubbed Forest Blizzard (STRONTIUM)) is actively exploiting an Outlook flaw to target Exchange Servers. The vulnerability could potentially unlock unauthorized access to emails and pave the way for the pilfering of sensitive information.
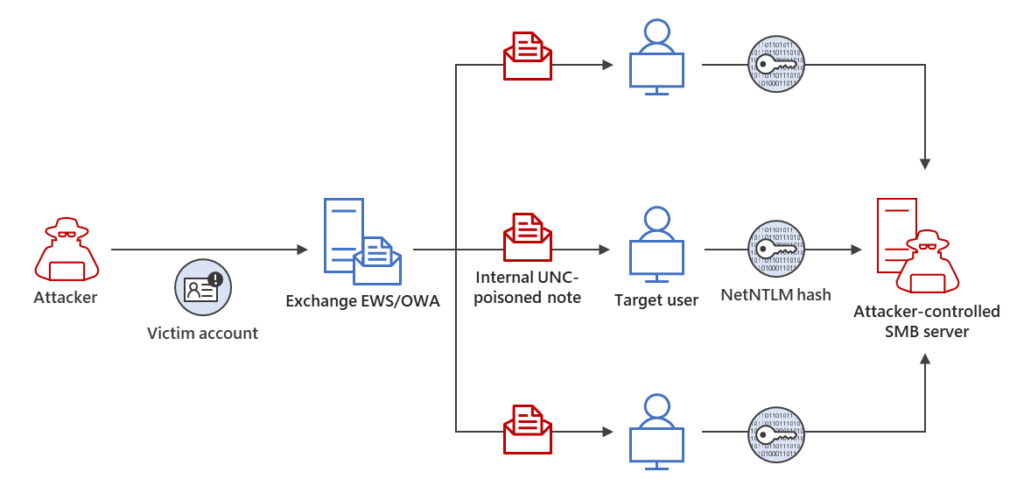
In March, Microsoft disclosed a critical vulnerability in Outlook for Windows that attackers could potentially exploit to gain elevated privileges. The security flaw, tracked as CVE-2023-23397, allows threat actors to send a specially crafted message that can steal NTLM hashes. These hashes can then be used to launch NTLM relay attacks for remote authentication without user intervention.
Microsoft released the March Patch Tuesday updates to address a zero-day flaw that was found on vulnerable machines. However, it has been observed that Russian hackers are still exploiting the privilege escalation vulnerability against unpatched instances. The Forest Blizzard hacking group is targeting government, transportation, energy, and non-government organizations in the US, Europe, and the Middle East.
“Forest Blizzard continually refines its footprint by employing new custom techniques and malware, suggesting that it is a well-resourced and well-trained group posing long-term challenges to attribution and tracking its activities. Microsoft continually updates detections and protections against this threat group based on our telemetry and research,” the Microsoft Incident Response team explained.
Recommendations to mitigate Forest Blizzard attacks
Microsoft has partnered with the Polish Cyber Command (DKWOC) to identify the techniques used by the Forest Blizzard hackers. Organizations are advised to apply the patch for CVE-2023-23397 on their vulnerable Exchange Server to block sophisticated attacks. Additionally, Microsoft has released a script that can assist administrators in identifying compromised systems within their networks.
Microsoft recommends that IT administrators reset passwords for accounts that have been compromised and enforce multi-factor authentication (MFA) for all users. It is highly recommended to disable NTLM and limit SMB traffic by blocking connections to ports 135 and 445 from all inbound IP addresses.



