Recovering Deleted Items in Active Directory
Active Directory is a hierarchical database that holds information about the network’s resources such as computers, servers, users, groups and more. The main purpose of Active Directory is to provide central authentication and authorization services. Normal administrative tasks when working with Active Directory include creating, managing, moving, editing and sometimes – deleting – various objects such as user accounts, computer accounts, groups, contacts and other objects. The Active Directory database is stored on Domain Controllers (or DCs), in a file called NTDS.DIT (that’s not everything, but it’ll do for a short intro…)
While deleting an object in Active Directory is usually something an administrator would think twice before doing, sometimes mistakes do happen, and then the administrator ends up with one (or more) deleted items that he or she cannot restore anymore.
I bet I’m not telling you stuff you don’t know, otherwise you wouldn’t be here, would you? As a skilled IT professional, one should always make sure he or she has a working backup of the current AD database. In Windows 2000 Server and Windows Server 2003 this can be easily accomplished by running NTBACKUP and performing a System State backup. However, let’s assume that, for this example, no such backup exists, or, if it does, certain issues are preventing us from using it to restore our deleted objects.
How does Active Directory treat deleted items?
When an object is deleted from Active Directory, it is not immediately erased, but is marked for future deletion. You see, Active Directory uses a replication model that is characterized as “multi-master loose consistency with convergence”. Changes can be made on any DC in the forest, and the changes are then incrementally replicated throughout the forest. Therefore, object deletions in this environment cannot simply remove an object, because doing so would remove the unit of replication itself.
The marker used to designate that an AD object scheduled to be destroyed is called “tombstone”. A tombstone is an object whose IsDeleted property has be set to True, and it indicates that the object has been deleted but not removed from the directory, much like a deleted file is removed from the file allocation table but the data is not actually removed from the drive. The directory service moves tombstoned objects to the Deleted Objects container, where they remain until the garbage collection process removes the objects. The garbage collection process by default runs every 12 hours on a DC. The length of time tombstoned objects remain in the directory service before being deleted is either 60 days for Windows 2000/2003 Active Directory, or 180 days for Windows Server 2003 SP1 Active Directory (by default). The tombstone lifetime must be significantly longer than the garbage collection frequency to ensure that deletion of objects is replicated to other DCs.
Considering all the above, a delete operation is essentially a special modify operation that:
- Sets the IsDeleted value to True.
- Sets the internal WhenDeleted column to the IsDeleted metadata’s TimeChanged time stamp.
- Sets the Windows NT security descriptor to a special value.
- Changes the relative distinguished name (RDN) to a value that is otherwise impossible, (that is, one that cannot be set by an LDAP program).
- Strips all attributes not needed at this point by Active Directory. Key attributes such as the following are hard-coded to survive deletion:
- Object-GUID
- Object-SID
- Object-Dist-Name
- USN
Note: You can make changes to the Active Directory that allow the survival of more attributes in case of an object deletion. This was covered in our article entitled – Protect Objects in Windows Server 2003 Active Directory from Accidental Deletion.
You must understand the difference between restoring an object that has long been deleted from the database, and no longer is present in it, not even as a tombstoned object, and restoring a tombstoned object. Restoring tombstoned objects from the Active Directory database is often known as “reanimation”, and this is what this article is about.
Because tombstoning an object strips it from many attributes, you must know that if you do elect to reanimate a deleted user or group, you will still have to recover the group memberships and any other linked attributes of which you might be in need. Also, without going too deep into this issue, know that you cannot reanimate objects that were deleted from the Configuration NC (or Partition). I will try to cover these issues in a future article.
Note: One of the Active Directory features that were introduced in Windows Server 2003 with Service Pack 1 was the Directory Service Backup Reminders. With this reminder, a new event message, event ID 2089, provides the backup status of each directory partition that a domain controller stores, including application directory partitions and Active Directory Application Mode (ADAM) partitions. If halfway through the tombstone lifetime a partition has not been backed up, this event is logged in the Directory Service event log and continues daily until the partition is backed up.
Methods for restoring deleted items in Active Directory
There are several methods of reanimating tombstoned objects from the Active Directory. Some are simple and easy to perform, some are more cumbersome. Some are freeware, some are more sophisticated and cost (a lot of) money. On this page I’ve listed some of the freely available tools. For those that cost money – hire a consultant (or me…).
Whatever you do, make sure you have a good and working backup of the domain controller’s System State. The System State contains the local Registry, COM+ Class Registration Database, the System Boot Files, certificates from Certificate Server (if it’s installed), Cluster database (if it’s installed), NTDS.DIT, and the SYSVOL folder.
You can easily backup the DC’s System State by using NTBACKUP or any range of 3rd-party tools that have that capability built in them. You do not need to backup all your DCs’ System States, usually backing up the first DC in the Forest + the first DCs in each domain is enough for most scenarios. You can read more about it on my “Backup Windows Server 2003 Active Directory” article (insert link).
Restoring the item from a previous backup
Restoring deleted items from a previous System State backup is not as simple as it sounds. In fact, this is not really reanimation, but actually a total restore of the deleted object. However, since restoring deleted items by usage of the NTBACKUP program and the System State backup involve shutting down the DC and booting it into “DS Restore Mode”, the reanimation mechanism is the only way to recover deleted objects without taking a DC offline.
There are several issues and steps that you need to perform, all are covered in my “Restore Windows Server 2003 Active Directory” article
Restoring the objects with LDP.EXE
As written in the beginning of this article, deleted objects in Active Directory are not really deleted, they are just “tombstoned” for a period of time that can either be 60/180 days, depending on your DCs’ operating system, or any other value, if it was ever changed by the system administrator.
Restoring objects with ADRestore.net
Guy Teverovsky, a fellow MVP from Israel, has written a cool tool that allows you to easily restore deleted AD objects. The tool is provided as freeware and has no kind of support, but from what I’ve seen, it works great. Some of the tools features include:
- Browsing the tombstones
- Domain Controller targeting
- Can be used with alternative credentials (convenient if you do not logon to your desktop as Domain Admin, which you should never do anyway)
- User/Computer/OU/Container reanimation
- Preview of tombstone attributes
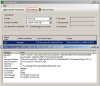
Enumerating tombstones
Previewing the tombstone attributes
Restoring a deleted user account
Download ADRestore.net
For more information on Guy’s tool, please see Guy’s blog entry announcing ADRestore.net
Restoring objects with Microsoft ADRestore (previously Sysinternals)
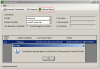
Formerly Sysinternals and now Microsoft, Mark Russinovich has created a command-line freeware application called ADRestore. The tool enumerates all of the currently tombstoned objects in a domain and allows you to restore them selectively, and provides a convenient command-line interface for using the Active Directory reanimation functionality. If you run it from the command line you will be prompted to choose which object you want to restore, and since there could be quite a few tombstoned objects, this process might take some time as you answer NO to each and every prompt.
To add a little selectivity to the restore operation, you can run ADRestore with a parameter to narrow down the search. For example:
adrestore -r daniel
would search for all objects with “daniel” as part of its name.
The -r switch forces the program to prompt the user for each restoration. Otherwise, all the objects found matching said criteria will be automatically restored. The default (no criteria supplied) is that all tombstoned objects will be enumerated and restored.
Note that deleted items may no longer be members of specific organizational units or OUs. Restoring these objects from deleted status will not automatically restore them to their respective OUs; this will need to be done manually.
Download ADRestore
How to restore deleted user accounts and their group memberships in Active Directory – 840001
Quest Object Restore for Active Directory
Quest Software, a leading provider of application, database and Windows management solutions, offers at no charge a graphical utility that helps Microsoft Active Directory administrators recover deleted objects using the Tombstone Reanimation feature of Windows Server 2003. This Microsoft recovery interface allows administrators to restore accidentally deleted objects online, without rebooting a domain controller. Quest Object Restore for Active Directory enhances this ability by providing a graphical interface, similar to the Windows Recycle Bin, for viewing and restoring Active Directory objects.
Restoring single, deleted objects in Active Directory can be a manual and time-consuming process requiring system downtime. Object Restore for Active Directory is a free, graphical utility that allows you to instantly recover deleted objects in a Windows Server 2003 environment without rebooting a Domain Controller. The freeware utility allows viewing Tombstoned objects in Active Directory and reanimating deleted items using Microsoft’s new Tombstone Reanimation interfaces for Windows Server 2003. When you download the Freeware, a 6-month key is built in. You will be prompted to re-register on our site at the end of each 6-month period.
In order to download their product you will need to go through a very nagging and unfriendly registration screen. Proceed from here:
Quest: Object Restore for Active Directory
Note that Quest has a great variety of tools for Active Directory management and recovery, however since they are not freeware I will not give them a free advertising ride…
Related Article: