Verifying Administrator Access to Office 365 User Content
Office 365 Administrators Always Have Access to User Data
Shortly after posting the article explaining how to use compliance records captured for Teams and Skype for Business Online conversations in eDiscovery, I received a question asking if Office 365 administrators can access user content through eDiscovery. Of course, the answer is “yes.”
Administrators have always been able to access user content and don’t need eDiscovery functionality to do this. Administrators can log onto someone’s mailbox or give themselves permission to access a user’s OneDrive account, or use the Search-Mailbox cmdlet to copy messages from user mailboxes to another mailbox. And they can run content searches to scan mailboxes, SharePoint, OneDrive, Teams, Office 365 Groups, and public folders and export whatever they find to PST files, ZIP files, or individual files. In short, many ways are available to an Office 365 administrator to poke around in user content if they so wish.
The Need to Control Access
Those of us who have been around Microsoft Office server technology for a while don’t consider this news or shocking. Someone has to hold the keys to the kingdom and when you grant administrative permissions to a user, you create a contract that holds that person responsible for how they use that access. With great power comes awesome responsibility.
Given the existence of regulations like GDPR, organizations need to define how administrators access user information in their data governance policy. The policy should set out the circumstances when administrators are allowed to access user information, including requesting permission from a higher authority, notifying the owner, and restricting access to whatever is absolutely needed. The company’s legal advisors should be involved in drafting the policy and all managers, administrators, and users should be aware of its existence. It should be clear that unauthorized access to user information can lead to severe disciplinary action.
Practical Actions
After defining a policy, here are some practical steps you can take to exert control over unauthorized administrative access to user information.
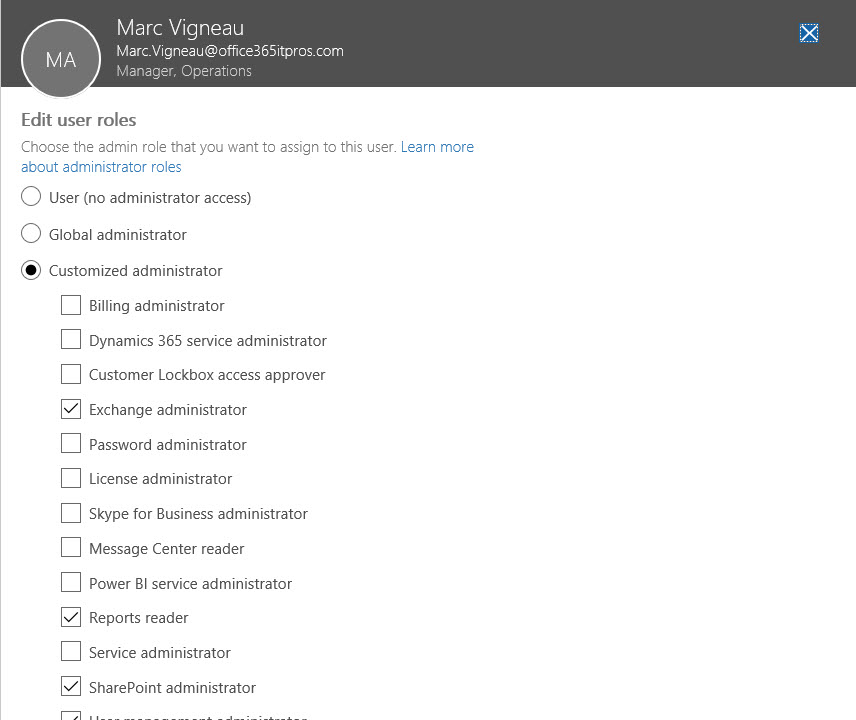
First, limit administrative permissions to people who really need the access. For example, you cannot run the Search-Mailbox cmdlet unless your account is assigned the Mailbox Search or Mailbox Import Export RBAC roles. By default, these roles are not assigned to any of the default Exchange Online role groups, so no one can use Search-Mailbox unless an administrator adds the role to a role group or creates a new role group and includes the role, and then assigns the use to the role group with the role.
Check Exchange RBAC Roles
To check the accounts that hold the Mailbox Import Export role, we can run the Get-ManagementRoleAssignment cmdlet. Here’s what I found in my tenant:
Get-ManagementRoleAssignment -Role 'Mailbox Import Export' -GetEffectiveUsers | ? {$_.AssignmentMethod -eq "RoleGroup"} | Format-Table EffectiveUserName, Name
EffectiveUserName Name
----------------- ----
TRedmond Mailbox Import Export-Organization Management-Delegating
James Redmond Mailbox Import Export-Organization Management-Delegating
PCunningham Mailbox Import Export-Organization Management-Delegating
Marc.Vigneau Mailbox Import Export-Organization Management-Delegating
Brian Weakliam Mailbox Import Export-Organization Management-Delegating
TempAdmin Mailbox Import Export-Organization Management-Delegating
Administrator Mailbox Import Export-Organization Management-Delegating
TRedmond Import Export Org Management
James Redmond Import Export Org Management
PCunningham Import Export Org Management
Marc.Vigneau Import Export Org Management
Brian Weakliam Import Export Org Management
TempAdmin Import Export Org Management
Administrator Import Export Org Management
Apart from the list of accounts who can run the cmdlet, the most interesting thing that I discovered from this exercise was that the Organization Management role group included the role. Because Organization Management had the role, a special role group called ExchangeServiceAdmins_53add inherited the role (these are the accounts with the Mailbox Import Export-Organization Management-Delegating entry).
You can’t manage the membership of the ExchangeServiceAdmins_53add role group (Figure 1) because it is linked to accounts assigned the Exchange Administrator role through the Office 365 Admin Centre.
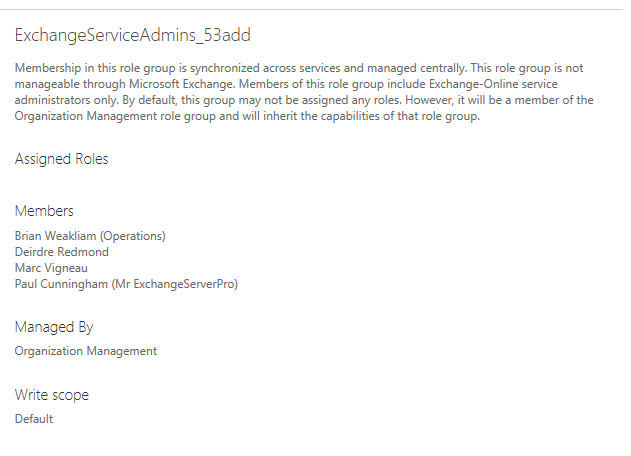
Running the check prompted me to review the accounts in the Organization Management role group and those assigned the Office 365 Exchange Administrator role. I cleaned up my act; you should do the same for your tenant.
Auditing Content Searches
When administrators perform eDiscovery actions, Office 365 captures details in its audit log. The key to analyzing Office 365 audit records is to understand the names of the events you want to find. This is easily done by looking through the results of the audit log search in the Security and Compliance Center. We can then look for records over a period and analyze what we find.
In this example, we look for records captured when users exported the results of a content search or viewed the results of a content search. You can add other activities to the mix, but these are the ones most likely to reveal any irregular activity. The output is to a CSV file, shown in Figure 2.
$Records = (Search-UnifiedAuditLog -StartDate 31-May-2018 -EndDate 29-Aug-2018 -Operations "SearchExportDownloaded", "SearchViewed", "ViewedSearchPreviewed" -ResultSize 1000)
If ($Records.Count -eq 0) {
Write-Host "No audit records for content search activities found." }
Else {
Write-Host "Processing" $Records.Count "audit records..."
$Report = @()
ForEach ($Rec in $Records) {
$AuditData = ConvertFrom-Json $Rec.Auditdata
$ReportLine = [PSCustomObject][Ordered]@{
TimeStamp = $AuditData.CreationTime
User = $AuditData.UserId
Action = $AuditData.Operation
Status = $AuditData.Status
Exchange = $AuditData.ExchangeLocations
SharePoint = $AuditData.SharePointLocations
Query = $AuditData.Query }
$Report += $ReportLine
}}
$Report | Export-Csv c:\temp\SearchAuditRecords.csv -NoTypeInformation
Often Excel is enough to understand the audit records, but you can also import the CSV file into Power BI to chart and graph it in various ways.
Another Service Delivered by GDPR
GDPR has done the IT industry a favor by elevating the need to protect user information and making organizations aware of the consequences that can flow if they do not take action. Limiting and checking administrative access to user data is something all tenants should do. It just makes sense.
Follow Tony on Twitter @12Knocksinna.
Want to know more about how to manage Office 365? Find what you need to know in “Office 365 for IT Pros”, the most comprehensive eBook covering all aspects of Office 365. Available in PDF and EPUB formats (suitable for iBooks) or for Amazon Kindle.