
Key Takeaways:
- Microsoft’s Digital Crimes Unit successfully disrupted Storm-1152, a cyber threat group based in Vietnam, by seizing domains crucial to their operation.
- Microsoft took down several websites selling identity verification bypass tools and seized platforms marketing these services.
- The cybercriminals used various tactics such as scripts, automation, DevOps practices, and AI to bypass security measures.
Last week, Microsoft disrupted a Vietnam-based threat group called Storm-1152. Microsoft’s Digital Crimes Unit (DCU) gained control of the domains used by the group to sell millions of fraudulent Microsoft accounts to other cybercriminals.
The DCU team has obtained a court order from the Southern District of New York to take down the US-based digital infrastructure of the cybercrime-as-a-service group. As part of this operation, Microsoft has disabled several websites that were selling identity verification bypass tools, such as 1stCAPTCHA, AnyCAPTCHA, and NoneCAPTCHA. The company has also seized a website that was selling fake Outlook accounts known as Hotmailbox.me, as well as social media sites that were being used to market these illegal services.
“Storm-1152 runs illicit websites and social media pages, selling fraudulent Microsoft accounts and tools to bypass identity verification software across well-known technology platforms,” said Amy Hogan-Burney, General Manager for Microsoft’s DCU. “These services reduce the time and effort needed for criminals to conduct a host of criminal and abusive behaviors online.”
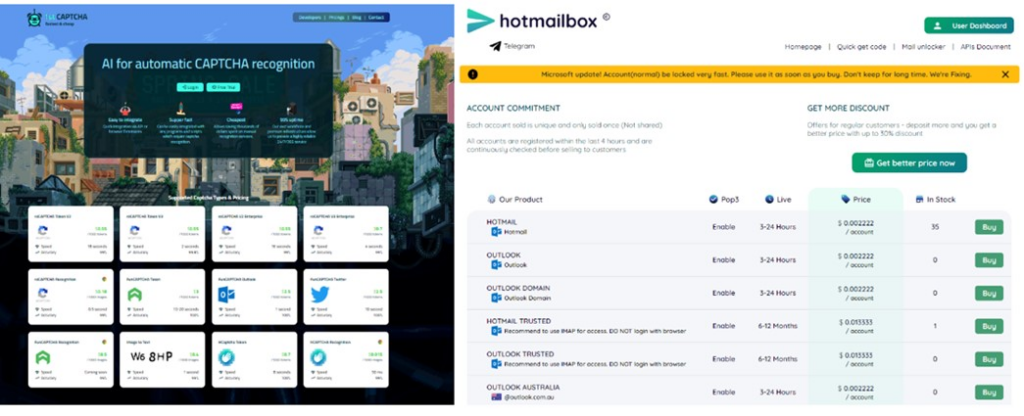
How Storm-1152 bypassed security measures to create scam Microsoft accounts
According to Microsoft, the cybercriminal group (Storm-1152) utilized a combination of scripts, automation, DevOps practices, and AI to bypass security measures such as CAPTCHA. This allowed them to create more than 750 million fraudulent Microsoft accounts sold for millions of dollars. The cybercriminals produced video tutorials with step-by-step instructions on using their products and offered chat services to other cybercriminals who wanted to utilize their fraudulent services.
Microsoft explained that this move is part of its efforts to disrupt malware and state-backed cyberattacks. The company has also partnered with other organizations to improve its machine-learning algorithms that quickly monitor and detect fraudulent accounts. “As we’ve said before, no disruption is complete in one day. Going after cybercrime requires persistence and ongoing vigilance to disrupt new malicious infrastructure,” Hogan-Burney added.
Cybersecurity experts recommend using advanced security algorithms to detect malicious activities. It is highly recommended to implement strong multifactor authentication (MFA) mechanisms for account creation. MFA goes beyond traditional password protection, requiring users to provide additional verification factors such as biometrics or one-time codes.



