Microsoft Removes Edition Checks for AppLocker Deployment on Windows 10 and 11

Microsoft has made some changes to the way the AppLocker application control policies work on Windows PCs. The company has quietly removed the checks that were previously used to identify the specific edition of Windows 11 or 10 installed on a system
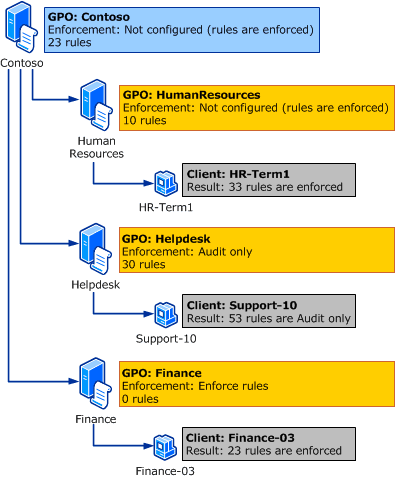
AppLocker is a security feature that enables IT Pros to enforce policies to manage applications that users can run on their systems. These policies can be configured to allow or block specific packaged apps, installers, scripts, EXE, and DLL files.
AppLocker policies can be configured to allow or block specific applications, scripts, installers, and DLLs. Administrators can create the policies with the Group Policy Editor or PowerShell. The AppLocker rules can be applied on a per-user or per-group basis.
IT Admins can now apply AppLocker policies across all Windows editions
Previously, AppLocker application control policies were enforced based on the Windows edition and the endpoint management method. “For instance, systems managed by mobile device management (MDM) enforced AppLocker policies on all editions of Windows 10 and Windows 11. Also, systems managed by Group Policy only enforced AppLocker policies on Windows 10 and Windows 11 Enterprise or Education editions,” Microsoft explained.
According to Microsoft, IT admins can now deploy the policies across Windows 11 versions 22H2 and 21H2 as well as Windows 10 versions 2004, 20H2, and 21H1. The change allows administrators to enforce AppLocker policies on more managed Windows 10 and 11 PCs.
Moreover, it can help to free up some extra time to focus on other important tasks, including managing security updates and troubleshooting issues. You can check out this support page to learn more details about AppLocker deployment on Windows 11 and Windows 10.



