
Microsoft has recently discovered a new ransomware campaign that’s targeting organizations within the transportation and logistics industries across Poland and Ukraine. The novel Prestige ransomware strain was first found on October 11, and the attackers targeted a wide range of systems within an hour.
The Microsoft Threat Intelligence Center (MSTIC) explained that it has been unable to track the hacking group behind the ransomware attacks. The security researchers observed that the ransomware campaign is similar to previous attacks by Russian state-backed threat actors that impacted Ukraine government agencies. However, the Prestige ransomware is explicitly targeting the networks of Ukrainian enterprises.
Microsoft is tracking the ransomware campaign as DEV-0960, a term used for previously unidentified threat actors. The hacking group abused several publicly available tools for remote-code execution to steal highly privileged administrator credentials within the victim’s network.
Specifically, the attackers used three different methods to obtain privileged access to the compromised environment to deploy the Prestige payload. Once deployed, the operators dropped a ransom note called “README.txt” in the root directory of each encrypted drive on the target device.
“For this DEV-0960 activity, the methods used to deploy the ransomware varied across the victim environments, but it does not appear to be due to security configurations preventing the attacker from using the same techniques. This is especially notable as the ransomware deployments all occurred within one hour,” the Microsoft Threat Intelligence Center explained.
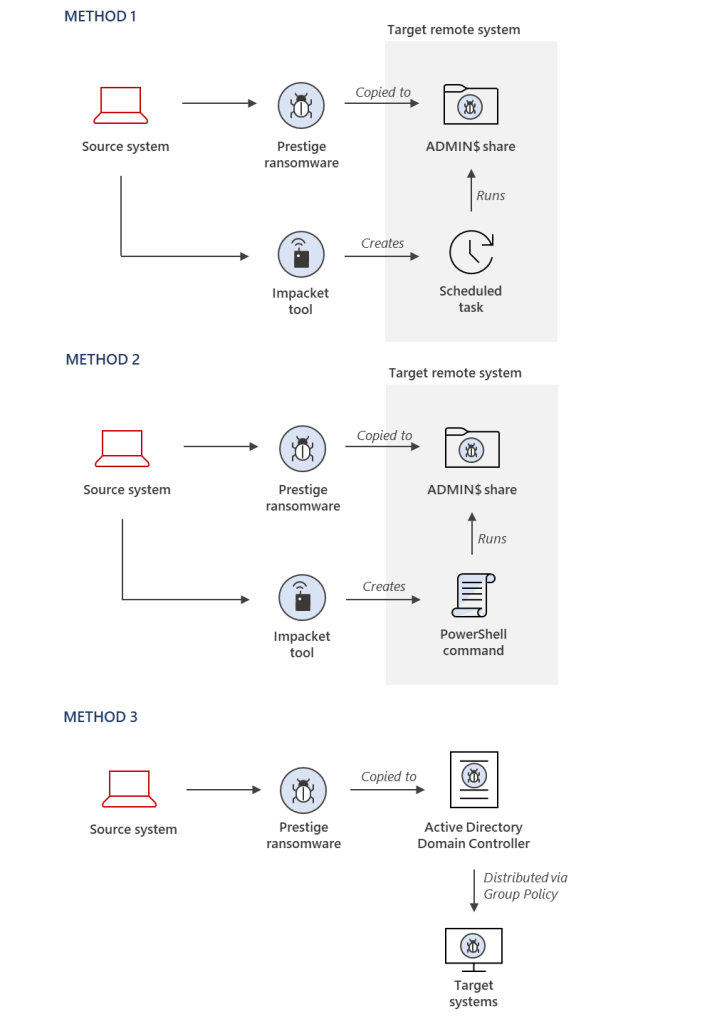
Microsoft details indicators of compromise to detect the Prestige ransomware
Microsoft suggests that organizations should follow the best security practices to prevent ransomware attacks. The company advises customers to set up multi-factor authentication (MFA), tamper protection, and cloud-based protection in Microsoft Defender.
Moreover, Microsoft has advised IT admins to look for a series of indicators of compromise (IoCs) within enterprise networks, and you can find more details in Microsoft’s blog post.



