
Microsoft has discovered a new massive AiTM phishing campaign that can steal credentials even if the user account is protected with multi-factor authentication (MFA). The company has warned that the threat actors have targeted over 10,000 organizations since September 2021.
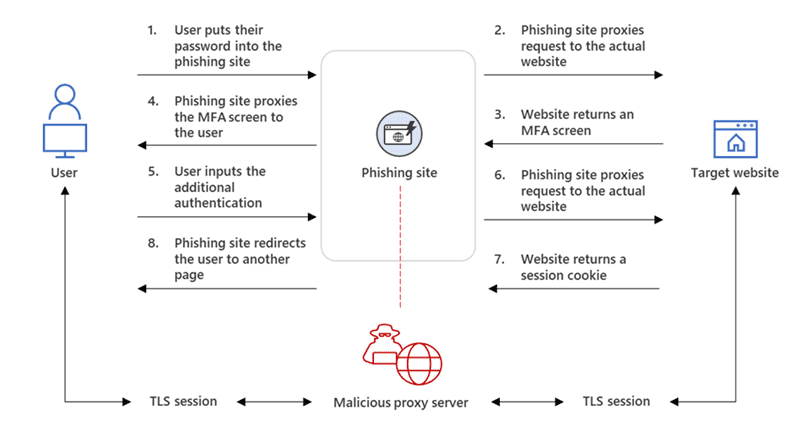
According to Microsoft researchers, the AiTM campaign involves inserting a proxy server between a target user and the website the victim intends to visit. Once the user logins to the proxy site, the attackers hijack session cookies sent by the legitimate website. This technique lets them get authenticated regardless of the sign-in method used by the victim.
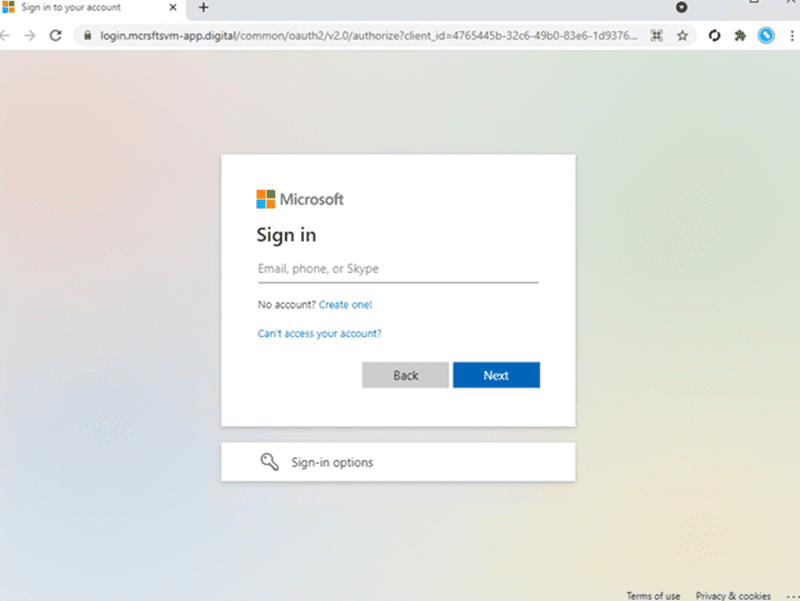
In the phishing campaign observed by Microsoft, the victim received an email with an HTML attachment that led to the proxy server. The threat actor took less than five minutes to complete the authentication process on the user’s behalf to perform secondary attacks within the targetted organization.
“From our observation, after a compromised account signed into the phishing site for the first time, the attacker used the stolen session cookie to authenticate to Outlook online (outlook.office.com),” the Microsoft 365 Defender Research Team and the Microsoft Threat Intelligence Center explained. “In multiple cases, the cookies had an MFA claim, which means that even if the organization had an MFA policy, the attacker used the session cookie to gain access on behalf of the compromised account.”
Over the next few days, the attackers accessed business emails and confidential files in order to commit payment frauds. They managed to trick co-workers or business partners into making payments. Additionally, the threat actors moved phishing emails to an archive folder to hide traces of unauthorized access from the hacked employee.
How to defend against AiTM phishing campaigns
It is important to note that some forms of MFA (such as one-time passwords (OTP)) can’t protect customers from phishing attacks and account takeovers. It is recommended that organizations use MFA methods (physical security key and biometrics) that comply with FIDO Alliance standards.
Meanwhile, Microsoft encourages customers to set up Conditional Access in Azure Active Directory (AD) to mitigate AiTM attacks and prevent phishing attempts. The company says that businesses should also invest in advanced anti-phishing solutions and continuously monitor suspicious activities



