Microsoft Improves Security for Windows Server Update Services
There haven’t been any significant changes to Windows Server Update Services (WSUS) for years. But recently, Microsoft released two updates that aim to make it easier to secure WSUS. In this article, I’ll look at how the two changes, introduced in September 2020 and January 2021, can help improve WSUS security.
By default, Windows clients connect to WSUS servers using HTTP on port 80. Microsoft doesn’t recommend this configuration be used in production environments and organizations should always configure WSUS to use HTTPS to prevent man-in-the-middle attacks. Without the additional security that HTTPS/TLS provides, an attacker could use a fake WSUS server to inject malicious code into Windows 10 clients.
User proxies no longer supported in WSUS environments not configured for TLS/HTTPS
In case you missed it, the September 2020 cumulative update (CU) for Windows 10 introduced a change to improve security for devices in environments where WSUS is not secured using TLS/HTTPS. If a Windows client connects to WSUS via a proxy server, after the September 2020 CU is applied, scans against WSUS will fail if only user proxy settings are configured. To ensure that Windows clients can continue to scan WSUS servers, system proxy settings must be configured on your client devices.
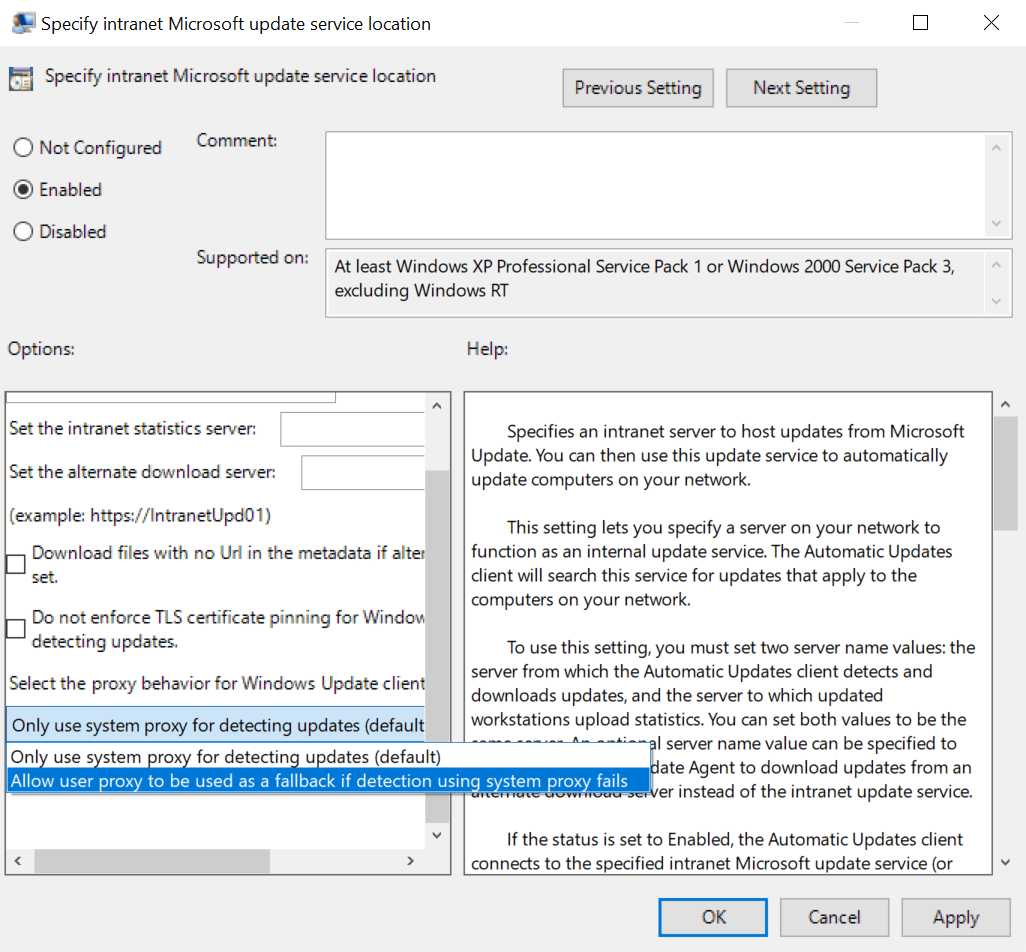
If you really need devices to have user proxy settings configured, you should set the proxy behavior to “Allow user proxy to be used as a fallback if detection using system proxy fails “ in Group Policy under Policies > Administrative Templates Windows Components > Windows Update > Specify intranet Microsoft update service location.
User proxy settings are configured in the Internet Options control panel applet under LAN settings on the Connections tab. System proxy settings are configured using netsh winhttp command. To configure the Windows Update client to use a system proxy instead of user proxy settings, check out Microsoft’s article here on using Group Policy to apply WinHTTP proxy settings.
Configure WSUS to use HTTPS
If you would like to configure your environment to use HTTPS with WSUS, then you can find instructions on how to do that here.
Certificate pinning provides highest level of security for WSUS in January 2021 update
Microsoft introduced another change in the January 2021 CU that prevents clients scanning WSUS using a system proxy if certificate pinning fails. Certificate pinning is used to limit which SSL certificates systems deem valid for specific URLs. Administrators can pin certificates that must be used for securing connections to WSUS instead of allowing use of any certificate that the client trusts. Certificate pinning helps to reduce the risk of a hacker using a certificate to get access to your client systems.
As you might expect, certificate pinning only applies to environments where WSUS is configured to use HTTPS. To facilitate certificate pinning for WSUS, there’s a new certificate store called WindowsServerUpdateServices. Administrators must place the certificates they want clients to use for securing WSUS communications in this new store.
If there are no certificates in the WindowsServerUpdateServices store, then certificate pinning is not enabled or enforced. When WindowsServerUpdateServices is populated, any other certificates a system trusts cannot be used for securing communications to WSUS. Attempts to use certificates that are not pinned will result in failed connections to WSUS.
If you want to really make sure that certificate pinning is disabled, set Do not enforce TLS certificate pinning for Windows Update client for detecting updates to Enabled under Computer Configuration > Administrative Templates > Windows Components > Windows Update > Specify intranet Microsoft update service location.
WSUS HTTPS and certificate pinning take security to the next level
Securing WSUS is important because it provides security and reliability updates to your Windows systems. Hackers can easily compromise the update mechanism if WSUS communications aren’t secured using HTTPS. And if you already have HTTPS implemented, certificate pinning provides an additional layer of security to help keep Windows clients protected.