Microsoft has published guidance to help businesses protect their Windows devices against the BlackLotus UEFI bootkit. The company also detailed some mitigation strategies to recover from BlackLotus attacks in enterprise environments.
BlackLotus is a sophisticated malware that allows attackers to target the UEFI (Unified Extensible Firmware Interface). It enables threat actors to bypass Secure Boot and hijack the boot process even on updated Windows 11 machines. BlackLotus modifies the registry files to disable OS security mechanisms, including Windows Defender, BitLocker encryption, and Hypervisor-protected Code Integrity (HVCI).
Essentially, BlackLotus exploits the CVE-2022-21894 vulnerability to bypass Secure Boot and other advanced protections. Microsoft fixed this vulnerability in January 2022, but the signed binaries still need to be included in the UEFI revocation list
“It is critical to note that a threat actor’s use of this bootkit is primarily a persistence and defense evasion mechanism. It is not a first-stage payload or an initial access vector and can only be deployed to a device to which a threat actor has already gained either privileged access or physical access,” the Microsoft Incident Response team explained.
Microsoft has detailed a couple of artifacts that should be analyzed to track BlackLotus infections in enterprise environments. The company suggests IT admins to use the mountvol command-line utility to mount the boot partition, and find recently created and locked bootloader files. The Microsoft Incident Response team also recommends security teams to examine registry keys, network logs, Windows Event logs, and boot configuration files.
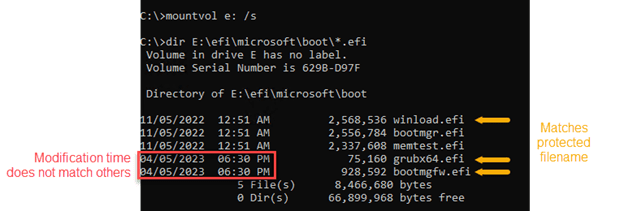
Effective strategies for recovery and prevention against BlackLotus attacks
Microsoft has provided some recommendations that should help organizations to recover Windows devices infected with BlackLotus. The company urges IT Pros to disconnect these devices from the network and reinstall with a clean operating system and EFI partition. It’s also possible to restore from a clean backup with an EFI partition.
It’s highly recommended that organizations should maintain credential hygiene, and restrict local administrative privileges to block BlackLotus attacks. Moreover, IT admins should ensure that their antivirus products are always up to date.


