
Microsoft has patched a critical in Azure Service Fabric dubbed “FabricScape” that affects containerized workloads on Linux. The software giant urges customers to upgrade their clusters as soon as possible to prevent successful exploits.
Azure Service Fabric is basically a distributed systems platform that allows developers to build and host microservices-based cloud apps. It powers several Microsoft services, including Microsoft Intune, Skype for Business, Cortana, Dynamics 365, Azure Event Hubs, Azure SQL Database, Azure Cosmos DB, and Azure Data Factory.
Cybersecurity researchers from Palo Alto Networks first disclosed the security vulnerability (CVE-2022-30137) in January this year. The flaw enables threat actors to perform a privilege escalation attack on the host Service Fabric node and potentially take over the entire cluster.
Microsoft noted that attackers will need Runtime access to the container to exploit this vulnerability, which is unfortunately granted by default. The company has also detailed the steps that can be taken for a successful attack, and you can check out the security advisory for technical details.
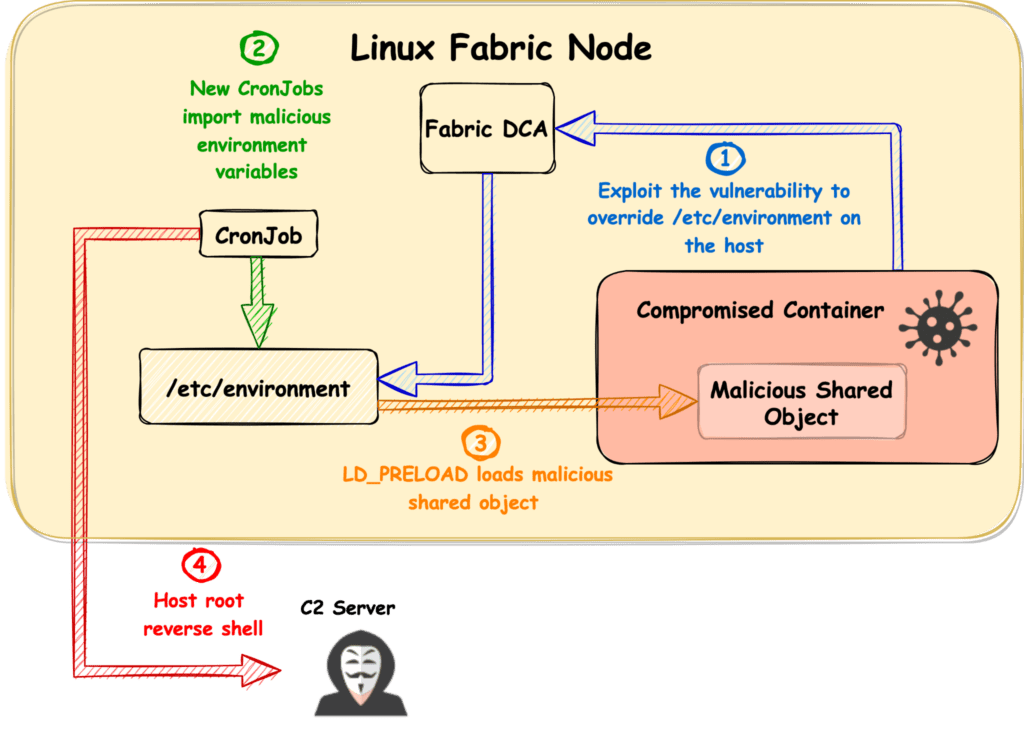
The Redmond giant confirmed that the bug is present in both Windows and Linux, but the problem only affects Linux containers. “Though the bug exists on both Operating System (OS) platforms, it is only exploitable on Linux; Windows has been thoroughly vetted and found not to be vulnerable to this attack,” the company explained.
Update Azure Service Fabric clusters
Microsoft released security patches to address the FabricScape vulnerability on June 14. The company says that customers with automatic updates enabled should have already received the fix. Meanwhile, Microsoft has also sent notifications about the issue via Azure Service Health to all customers who don’t use the auto-update mechanism.
As of this writing, there is no evidence that attackers have successfully exploited the security flaw. However, it is still recommended to patch Azure Service Fabric clusters and follow Microsoft’s best practices.
“While we’re not aware of any attacks in the wild that have successfully exploited this vulnerability, we want to urge organizations to take immediate action to identify whether their environments are vulnerable and quickly implement patches if they are,” said Palo Alto Networks.



