
Microsoft introduced a new automatic attack disruption feature in its Microsoft 365 Defender solution at Ignite 2022. The company announced yesterday that the feature can now protect enterprise customers against business email compromise (BEC) campaigns.
Automatic attack disruption leverages extended detection and response (XDR) technology to contain ongoing ransomware campaigns or other sophisticated attacks across identities, endpoints, email, and SaaS applications. The feature immediately suspends all compromised accounts and isolates infected devices to reduce the attack’s impact.
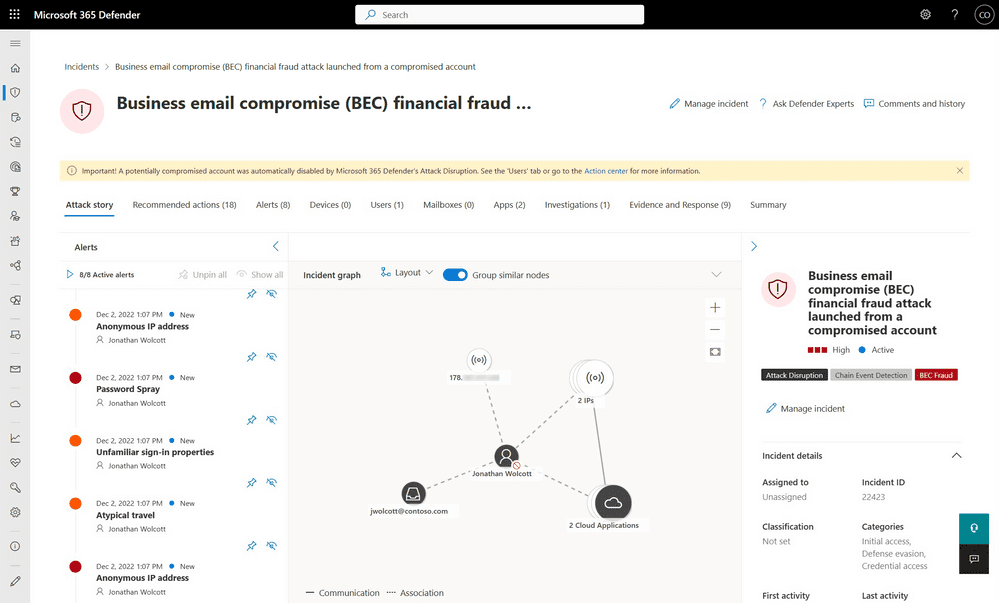
Previously, Microsoft 365 Defender’s automatic attack disruption feature only provided protection against human-operated ransomware attacks. The latest release adds support for detecting and disrupting business email compromise (BEC) campaigns. It’s a type of phishing attack that enables attackers to steal sensitive data and money from target organizations.
“BEC attacks commonly involve cybercriminals impersonating a company’s executives or vendors to trick employees into transferring money or sensitive information – causing financial losses and reputational damage. Automatic attack disruption can help detect these attacks and remove the attacker’s access to the environment by disabling the compromised account, limiting their ability to send a fraudulent email, and preventing money transfers and financial losses,” Microsoft explained.
How automatic attack disruption works in Microsoft 365 Defender
Microsoft explained that the automatic attack reduction feature works in 3 phases. First of all, Microsoft 365 Defender uses AI-driven detection capabilities to detect malicious activities. Secondly, it analyzes the malicious activities and flags the assets controlled by the hackers. Finally, the service triggers automatic response actions against compromised entities to block ongoing attacks.
Lastly, Microsoft has added new visual cues to highlight the automatic actions and the current asset status. Furthermore, administrators can easily tailor the automatic attack disruption settings to their preferences and revert any changes via the Microsoft 365 Defender Portal. You can learn more about automatic attack disruption on this support page.



