Stop MFA Fatigue with Additional Context and Number Matching for Microsoft Authenticator

Last week, Uber confirmed a major cybersecurity attack that compromised its internal communications and engineering systems. The company believes that someone affiliated with the hacking group Lapsus$ leveraged the MFA fatigue attack technique to compromise an Uber employee account.
According to the New York Times, the hackers social engineered the company’s worker after discovering his WhatsApp number. The intruders sent a direct message to the employee pretending to be an Uber IT staffer. They used the phishing technique to steal passwords and repeatedly sent multifactor authentication (MFA) login notifications. The Uber employee eventually accepted one of those login requests.
After gaining initial access, the attackers sent messages to a company-wide Slack channel announcing the massive security breach and reconfigured Uber’s OpenDNS. The screenshots revealed that the hackers had access to various internal systems, including G Suite accounts, Amazon Web Services, and code repositories.
What is MFA fatigue?
An MFA fatigue attack is “the process of sending a high volume of push requests to the target’s mobile device until the user accepts, either accidentally or simply to attempt to silence the repeated push notifications they are receiving.” Threat actors are increasingly using this technique to target large organizations, such as Microsoft and Cisco.
How to enable additional context in the Azure AD portal to block MFA fatigue attacks
Security researchers have advised organizations to add additional context (such as the application name and geographic location) in MFA push notifications to prevent MFA fatigue attacks. It is also recommended to combine additional context with number matching to boost sign-in security.
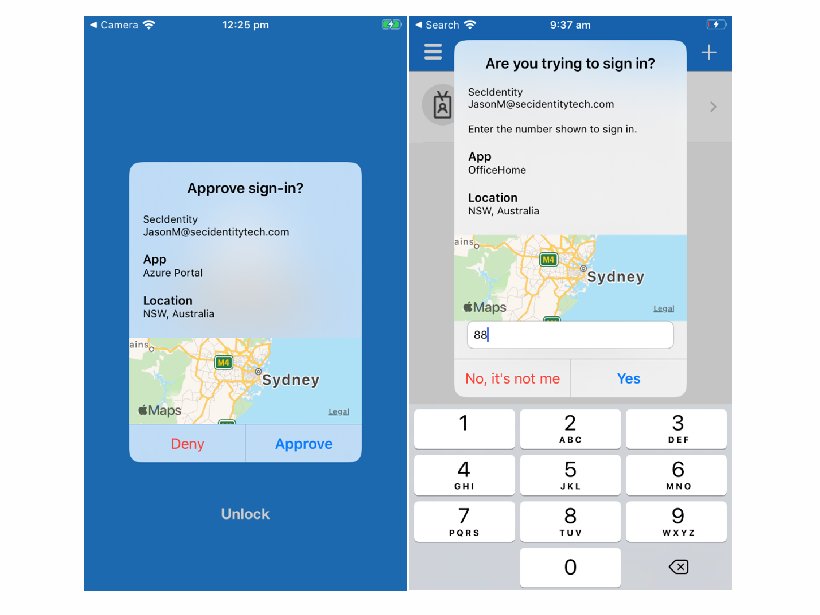
IT admins can enable additional context in the Azure AD portal by following the steps listed below:
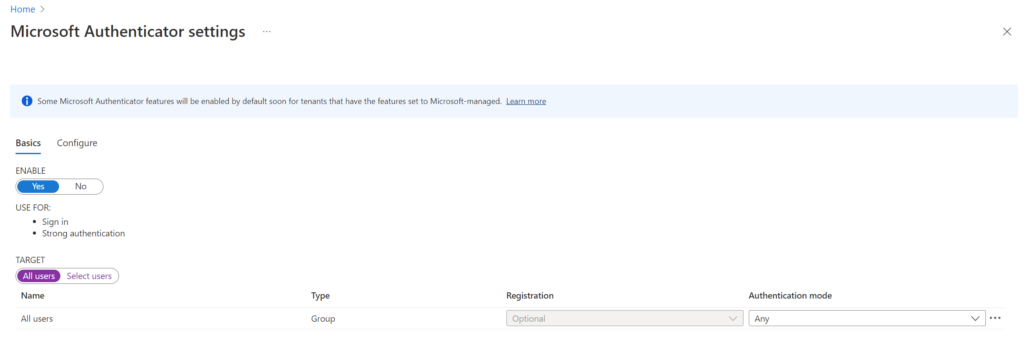
- Log in to the Azure AD portal and navigate to Security >> Authentication methods >> Microsoft Authenticator.
- Select the Basics tab, click the Yes and All users options, and then set the Authentication mode to Any.
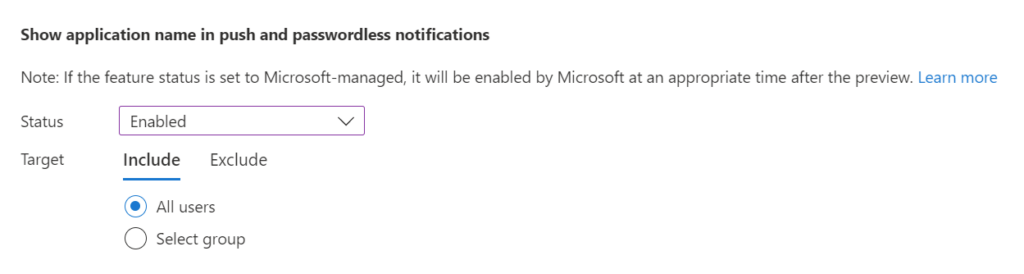
- In the Configure tab, navigate to the “Show application name in push and passwordless notifications” section and change its Status to Enabled. Choose users to include or exclude from the policy and click the Save button.
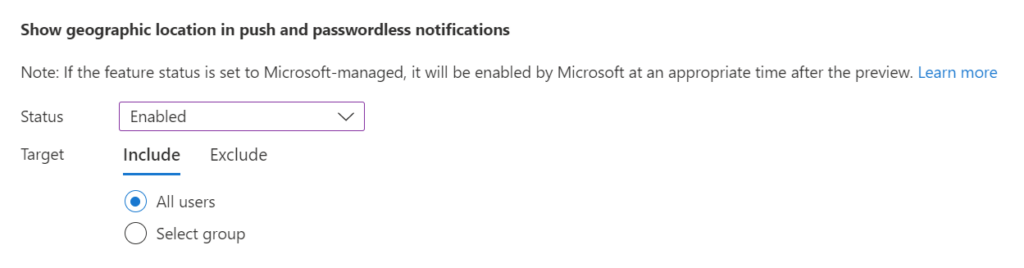
- Repeat the same process for “Show geographic location in push and passwordless notifications.”
It is important to note that IT admins can only enforce this policy on Microsoft Authenticator users. This means that those who have not been enrolled won’t be able to see the application name or geographic location. Moreover, additional context supported is not available for Active Directory Federation Services (AD FS) and Network Policy Server (NPS).



