Install PowerShell Web Access in Windows Server 2012
- Blog
- PowerShell
- Post
Windows PowerShell Web Access allows users to access PowerShell on a remote server via a web browser, without any prerequisite requirements on the client device, apart from a supported web browser. In this Ask the Admin, I’ll show you how to quickly install and configure this feature in Windows Server 2012. For more detailed configuration options on how to install PowerShell Web Access, see the four-part series PowerShell Web Access by Jeff Hicks.
Install a Windows PowerShell Web Access Gateway
A Windows PowerShell Web Access Gateway allows users to remotely access servers on a remote network using PowerShell commands executed from a web browser. To install the gateway, log in to Windows Server 2012 R2 as an administrator:
- Open a PowerShell console with administrative privileges. Switch to the Start menu, type powershell and press CTRL+SHIFT+ENTER.
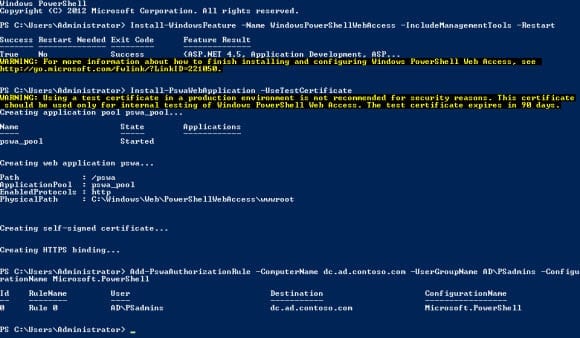
- In the PowerShell console, type Install-WindowsFeature –Name WindowsPowerShellWebAccess -IncludeManagementTools –Restart and press Enter.
Configure the Web Access Gateway Application
Once operation has completed, we can use PowerShell to configure the web application in IIS. The resulting URL for the web access console will be https://<server_name>/pswa, where <server_name> is the DNS name of the server where you are installing the Web Access Gateway.
- Switch to the Start menu, type powershell and press CTRL+SHIFT+ENTER.
- In the PowerShell console, type Install-PswaWebApplication –UseTestCertificate and press Enter.
The –UseTestCertificate parameter should only be used when creating a Web Access Gateway in a test lab. In a production environment, you can use the same command, but you should replace the certificate with one signed by a certification authority. The test certificate generated expires after 90 days.
Configure User Access via the Gateway
Before users can authorize, you need to setup authorization rules. This can only be done using PowerShell. In this example, I’m going to manage access in the authorization rule by using an Active Directory group. It is also possible to specify individual or multiple user accounts instead. For more information of the command syntax, see Add-PswaAuthorizationRule on TechNet.
- In a PowerShell console, type Add-PswaAuthorizationRule -ComputerName <server_name> -UserGroupName AD\PSadmins -ConfigurationName Microsoft.PowerShell and press Enter. Replace <server_name> with the fully qualified domain name (FQDN) of the device to which users are allowed to access. The remote computer can be the gateway itself, or any other computer on the network where PowerShell remoting is enabled. Microsoft.PowerShell is the default PowerShell session configured on all devices where PowerShell is installed.
To see a list of existing authorization rules, type Get-PswaAuthorizationRule in the PowerShell console window.
Access a Remote Computer Using the Web Access Gateway
Now we are ready to access a remote computer via the gateway, as defined in the authorization rule created in the previous step.
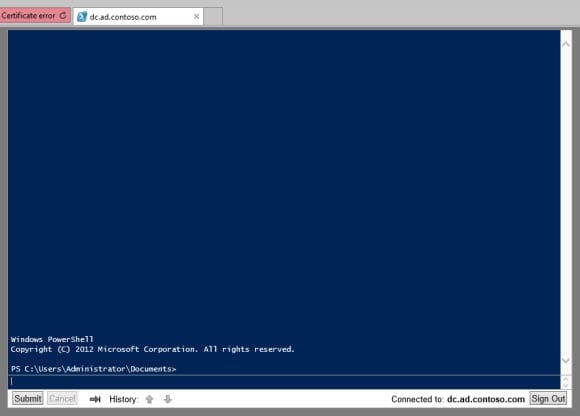
- Open a web browser on a remote computer and type the gateway application address, https://<server_name>/pswa, replacing <server_name> with the name of the Web Access Gateway server, and press Enter.
- Ignore the certificate warning and continue to the sign-in page.
- Enter the name of a user account that has permission to access a PowerShell session on the remote server, as defined by your authorization rule, in the following format: <domain>\<username>. For example, AD\administrator.
- Enter the user’s password and then type the FQDN of the computer you want to access in the Computer name box.
- Click Sign In and you will be taken to a new webpage with a PowerShell console.
Note that in a workgroup environment, the username should be entered in this format: <workgroup>\<username>.