How To Get NTFS File Permissions Using PowerShell

iCacls is a built-in command line tool for reporting NTFS access permissions in Windows. And while it is a comprehensive tool with lots of options, PowerShell provides more flexibility on how results are formatted. Like all PowerShell cmdlets, objects generated by Get-Acl can be easily processed by other PowerShell cmdlets, or the output can be formatted so that it can be passed to other applications. In this article, I will look at using Get-Acl with files and folders, but it can also be used with registry keys and other objects.
Check out this article on Petri about how to modify access control lists using icacls if you don’t want to use PowerShell.
Running Get-Acl without any parameters will return the NTFS permissions set on the current working directory. Or you can provide Get-Acl with a path instead.
Get-Acl -Path C:\temp
-Path is a positional parameter, so if it appears in the first position, you can omit -Path. But I will include it in the examples here for completeness.
Get-Acl C:\temp
If the output is truncated, pipe the output to the Format-Table cmdlet as shown below:
Get-Acl -Path C:\temp | Format-Table -Wrap
To get more information, you’ll need to use Format-List instead:
Get-Acl -Path C:\temp | Format-List
You can also return more specific information like this:
(Get-Acl -Path C:\temp).Access
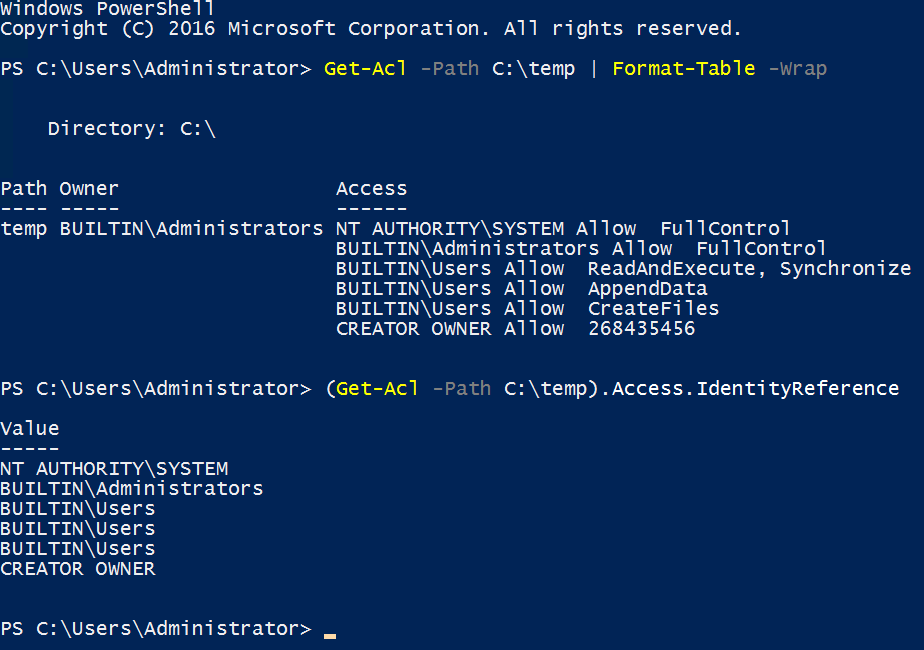
And again, you can narrow the output down further. Access.IdentityReference shows the users or groups listed in the ACL.
(Get-Acl -Path C:\temp).Access.IdentityReference
To discover what parameters can be used, press TAB in the PowerShell window after typing the period. For example, typing (Get-Acl C:\temp). and then pressing the TAB key will add Access to the command. Pressing TAB repeatedly will scroll through all the options.
(Get-Acl -Path C:\temp).[TAB]
When used on its own, Get-Acl can only report on one file or directory at a time. If you want to generate a report on a folder hierarchy, you’ll need to pass each folder to Get-Acl using a ForEach loop. First, I use the Get-ChildItem cmdlet to create an object that stores the folder hierarchy that I want to pass to Get-Acl.
$FolderPath = Get-ChildItem -Directory -Path "C:\temp" -Recurse -Force
The first loop cycles through each folder in the hierarchy. For each folder I run another ForEach loop that lists the entries (ACEs) in its ACL by creating a variable ($Properties) that formats the output to list the folder name, the group or user in the ACE, the permission(s) granted, and whether they are inherited. Finally, I create a new object using the $Properties variable, which is what is displayed in the output in the PowerShell window.
ForEach ($Folder in $FolderPath) {
$Acl = Get-Acl -Path $Folder.FullName
ForEach ($Access in $Acl.Access) {
$Properties = [ordered]@{'Folder Name'$Folder.FullName;'Group/User'=$Access.IdentityReference;'Permissions'=$Access.FileSystemRights;'Inherited'=$Access.IsInherited}
New-Object -TypeName PSObject -Property $Properties
}
}
You can see the output only lists folders. There are no files in the results. You could also create an array ($Output) and pipe the results to Out-GridView or a .csv file.
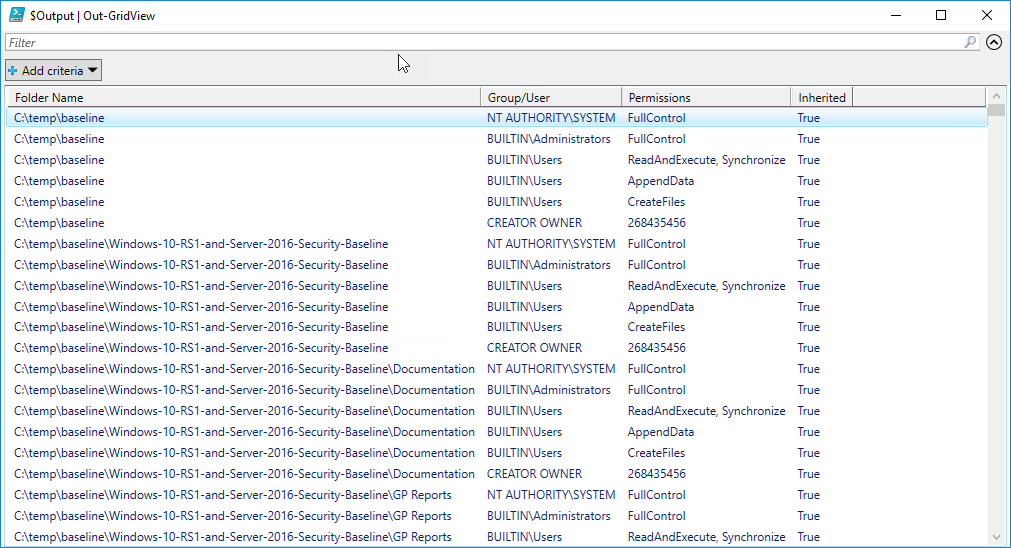
$FolderPath = Get-ChildItem -Directory -Path "C:\temp" -Recurse -Force
$Output = @()
ForEach ($Folder in $FolderPath) {
$Acl = Get-Acl -Path $Folder.FullName
ForEach ($Access in $Acl.Access) {
$Properties = [ordered]@{'Folder Name'=$Folder.FullName;'Group/User'=$Access.IdentityReference;'Permissions'=$Access.FileSystemRights;'Inherited'=$Access.IsInherited}
$Output += New-Object -TypeName PSObject -Property $Properties
}
}
$Output | Out-GridView
The script and commands that I’ve shown you in this article should help you to get started with using PowerShell to report on NTFS permissions.



