How to Enable Office 365 Multi-Factor Authentication
I can’t tell you how often I receive an email from someone I haven’t talked to in forever thinking “Hey, they thought of me!” only to find out they had their Yahoo or Gmail account hacked and they want to tell me about it. Their email to me says something like “You’ve got to see this!” with some bogus link. And no matter how often you tell folks to come up with stronger passwords they still use the same old passwords that are easily guessed by the bad guys. A partial answer to that problem is to use multi-factor authentication, and Office 365 have been recently updated to enable that functionality. Most banks offer multi-factor authentication — which requires a password as the first factor of authentication, and then a phone call, text message, or other contact method to confirm your identity, hence the “multi-factor” description — and now most email providers do as well, including Office 365 (as of February 2014).
Office 365 Multi-Factor Authentication
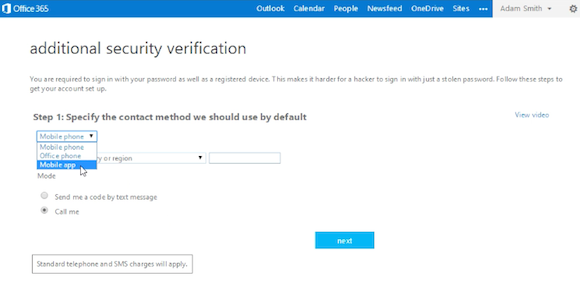
Setting up multi-factor authentication in Office 365 is relatively easy, so I’ve outlined the steps below, followed by a short video embedded farther down in this post that visually demonstrates the same procedure. From the perspective of an Office 365 administrator, it really comes down to enabling/disabling the feature. Once end-users are enabled they are prompted to choose their multi-factor method of choice (a phone call, a text message, an app notification).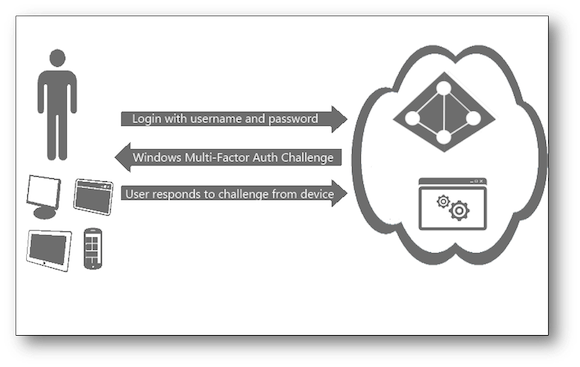
- Log into your Office 365 company portal with your administrative credentials.
- Select the ‘users and groups’ link on the left side of the screen.
- Select ‘Set up’ next to the line ‘Set Multi-factor authentication requirements:’
- Select one or more end-users and choose the ‘Enable’ link under ‘quick steps’ on the right pane. Note: You can also choose to read the deployment guide before proceeding.
- Select the ‘enable multi-factor auth’ link.
Enabling Office 365 multi-factor authentication video tutorial. (Video: J. Peter Bruzzese)
They have to specify a default contact method and then the system will verify that the method you’ve provided works. For example, in the video embedded above this paragraph you can see that we opted for the system to dial our mobile, so before it completes the configuration it first confirms that it can get through to us on our phone.Office 365 multi-factor authentication options (Source: J. Peter Bruzzese)
Office 365 Multi-Factor Authentication Types
The following types of authentication are available for Office 365 multi-factor authentication:- Call My Mobile Phone: When the users receive the confirmation call, they press # in the phone’s dial pad to log in.
- Call My Office Phone: This works like Call My Mobile Phone, but sends the confirmation call to a separate line, such as a desk phone.
- Text Code to My Mobile Phone: The user receives a code sent via SMS text message to their phone, then enter it in the Office 365 login form.
- Notify Me through App: The user can use a Microsoft smartphone app to receive and confirm the notification; the app is available for Windows Phone, iPhone, and Android.
- Show One-Time Code in App: This uses the same app as for the Notify Me through App option, but sends a one-time six-digit code that must be entered in the Office 365 login screen.