How to Control Intune Enrollment with Enrollment Restrictions
Part of what makes Intune such a compelling management tool is its universally accessible nature. Devices can be managed anywhere with an internet connection, eliminating dependencies on communicating with on-premises infrastructure over things like a VPN. Devices can also be enrolled anywhere with an internet connection and, by default, this is available to any user on any device.
There’s an advantage to this: your IT team get manageability of devices, with which comes control, with which comes the ability to secure and monitor its use. This is ideal for bring your own device (BYOD) scenarios. But be careful. If your users start fully enrolling their devices into Intune, do you have a policy advising them of such? Do your users feel comfortable with internal IT having the ability to remotely manage, including fully wipe, their machines? And do you even want such responsibility or blurring of the lines between what is corporate and what isn’t?
To have some more control over what we allow enroll into Intune, we can use enrollment restrictions.
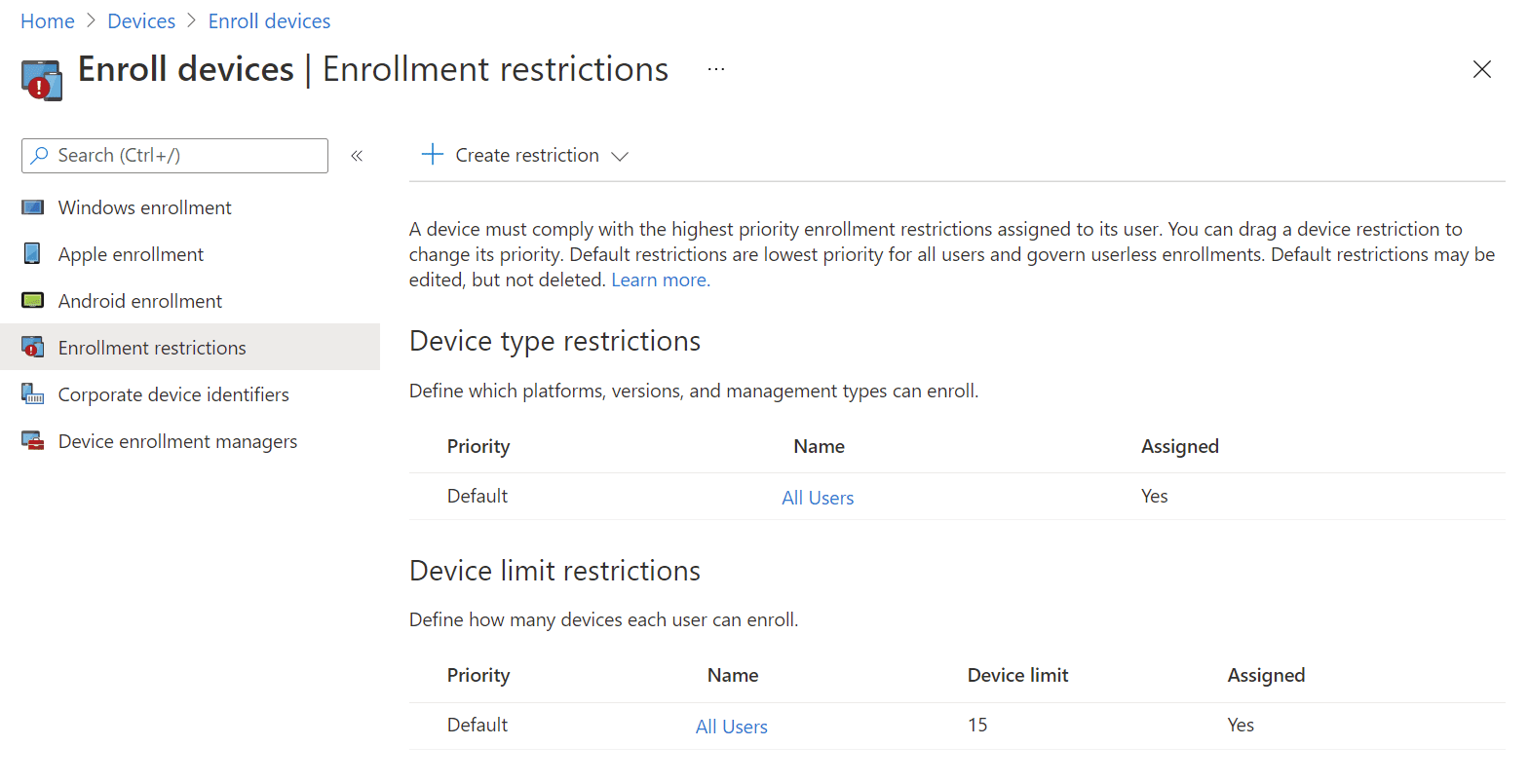
Enrollment restrictions are sets of rules assigned to Azure AD groups. There are two types of enrollment restrictions: device type and device limit. This lets you have different rules for different users. For example, you may allow your IT team or a pilot group of users the permission to enroll personal devices while everyone else cannot. The more restriction rules you have with different assignments, the higher the likelihood of a user being assigned multiple restrictions. To deal with this, restrictions are given a priority which works like a golf score, where lower wins, and only one applies: priority 1 beats priority 2, which beats priority 3, and any priority beats the default restriction.
All restrictions are created and can be later edited from Microsoft Endpoint Manager admin center > Devices > Enroll devices > Enrollment restrictions. Use the + Create restriction button to start a new restriction rule assignment.
Device type restrictions
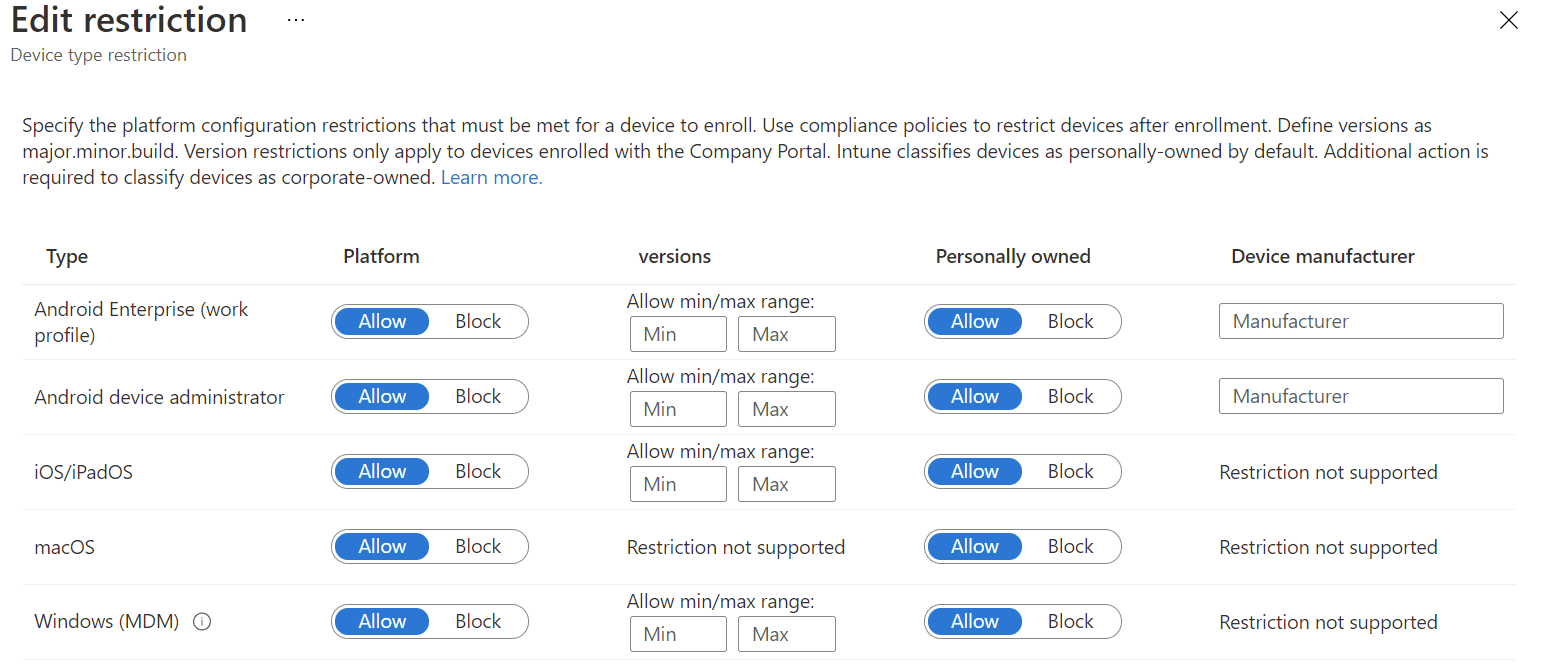
Device type restrictions allow you to control enrollment rights based on whether values related to the device itself: type (Android, iOS, macOS, Windows), ownership, operating system and version, and manufacturer. Some of these values are only supported on certain types of device. For example, macOS does not support restricting based on OS version, and only Android enrollment can be controlled by the manufacturer.
All device types support the ability to block personally owned devices. Intune assigns ownership as either corporate or personal to a device based on values that differ from platform to platform. Windows devices are categorized as corporate if they registered as Autopilot devices (but they don’t have to be enrolled during Autopilot), if their IMEI number is registered in Intune, are enrolled automatically using something like Group Policy (you can read how to do that here), or they exhibit enrollment by a few other methods indicative of corporate ownership. macOS and iOS are ideally controlled by serial number or use of Apple’s Automated Device Enrolment system. Android devices different depending on Android Enterprise of Device Administrator. In all cases, you can manually edit a device’s ownership later on in the device object’s properties in Endpoint Manager.
Device limit restrictions
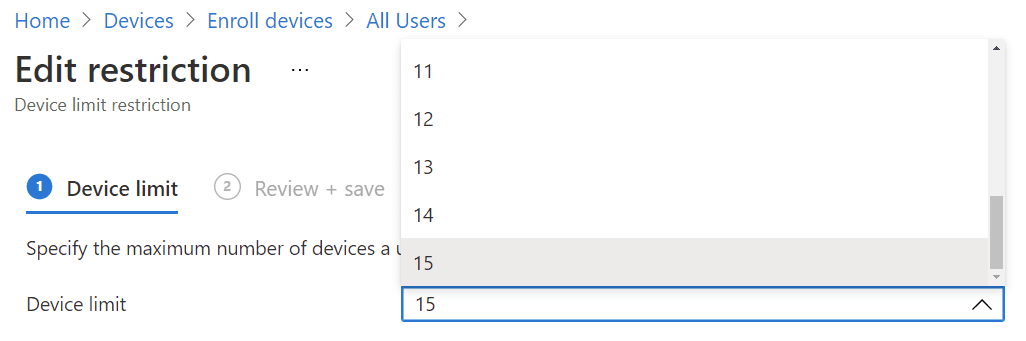
Falling squarely into the “does what it says on the tin” category, device limit restrictions control the number of devices a given Azure AD user is allowed to enroll. This is not a string value you can control freely: there is a lower limit of 1 and an upper limit of 15 which you cannot specify more than. When a user hits their assigned limit, and attempt to enroll, they will be notified they are the limit and should remove existing devices.
There are some important notes about the limit restrictions.
If devices are enrolling through just about any automatic or corporately controlled method, the restriction does not apply. For example, if a user is provisioning a Windows 10 device with Autopilot, the enrollment that is included in this does not count towards their limit. This means you don’t need to worry that actions such as remote Intune wipes and reprovisions will contribute to your device enrollment count. Similarly, enrolling into co-management with Configuration Manager or by Group Policy for Hybrid Azure AD Joined devices does not count.
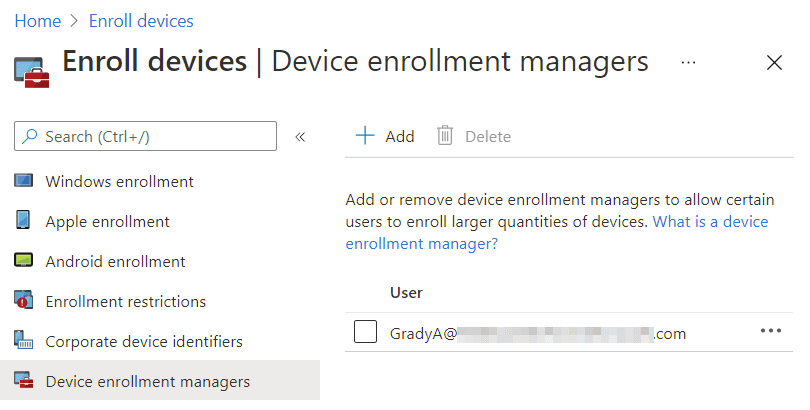
Lastly, there is a special privilege you can assign your Azure AD users: device enrollment manager (DEM), which is controlled from Microsoft Endpoint Manager admin center > Devices > Enroll devices > Device enrollment managers and clicking the + Add button. Specify an Intune licensee’s full username and they’ll become a DEM, empowering them to enroll up to a thousand devices. They do not need to be an Azure AD administrator for this. DEM is primarily used for scenarios such as device bulk enrollment, as using it introduces constraints around things such as the user initiating a wipe, and actually cannot be used on Android Enterprise fully managed devices.