
Key Takeaways:
- Russian hackers are exploiting a Windows print spooler flaw to gain elevated privileges and steal credentials in compromised enterprise networks.
- The hacker uses a custom tool named GooseEgg to target organizations, indicating a sophisticated and deliberate approach to cyber infiltration.
- Microsoft advises applying patches and implementing to mitigate the risk of cyberattacks.
Microsoft has warned customers about the exploitation of a Windows print spooler vulnerability by Russian hackers, enabling them to elevate privileges and pilfer credentials within compromised enterprise networks. The Russian hacking group is using a custom tool known as GooseEgg to target a range of organizations.
What is Windows Print Spooler vulnerability?
Microsoft patched the print spooler elevation of privilege vulnerability (CVE-2022-38028) in October 2022. The security flaw, which carries a CVSS rating of 7.8, allows attackers to attackers to remotely execute code with system-level privilege on vulnerable machines. The Windows print spooler service manages the printing process in Windows environments.
On Monday, Microsoft disclosed that Forest Blizzard (aka Fancy Bear) has been exploiting the CVE-2022-38028 vulnerability in the Windows Print Spooler service since at least June 2020. The hacking group has been linked by the US and UK governments to the Russian General Staff Main Intelligence Directorate (GRU).
Microsoft found that the Russian-backed threat actor exploited the security flaw to gain unauthorized access to a target Windows device. The attackers use a simple batch script to deploy the GooseEgg executable and establish persistence on the compromised system.
“While a simple launcher application, GooseEgg is capable of spawning other applications specified at the command line with elevated permissions, allowing threat actors to support any follow-on objectives such as remote code execution, installing a backdoor, and moving laterally through compromised networks,” the Microsoft Threat Intelligence team explained.
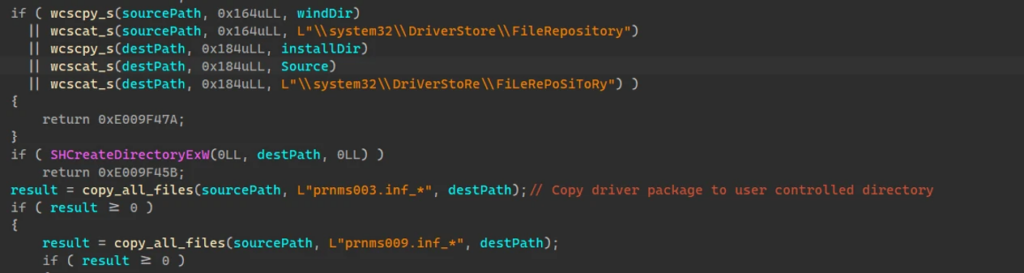
According to Microsoft, Forest Blizzard is using GooseEgg to launch attacks on organizations based in Ukraine, Western Europe, and North America. These targets span across various sectors including government, non-government, education, and transportation.
How to protect Windows devices against Forest Blizzard cyberattacks?
Microsoft’s advisory suggests that administrators should ensure that the fix for CVE-2022-38028 and CVE-2021-34527 has been deployed on Windows devices. Additionally, the company recommends disabling the print spooler service on domain controllers. A domain controller is a server computer that authenticates and validates user access on a network, and it doesn’t require printing capabilities.
Microsoft Defender for Identity offers a built-in security assessment that helps system admins detect the availability of Print Spooler services on domain controllers. You can find the full list of threat-hunting queries and indicators of compromise on Microsoft’s official blog post.


