Exiting Office 365 with Your Encrypted Messages and Documents
Creating a Cloud Exit Plan for Encryption
Microsoft engineering teams publish all sorts of useful tips. The only problem is that it can be hard to find the gems in the flood of information in announcements, marketing bumpf, and blogs that any self-respecting product organization generates.
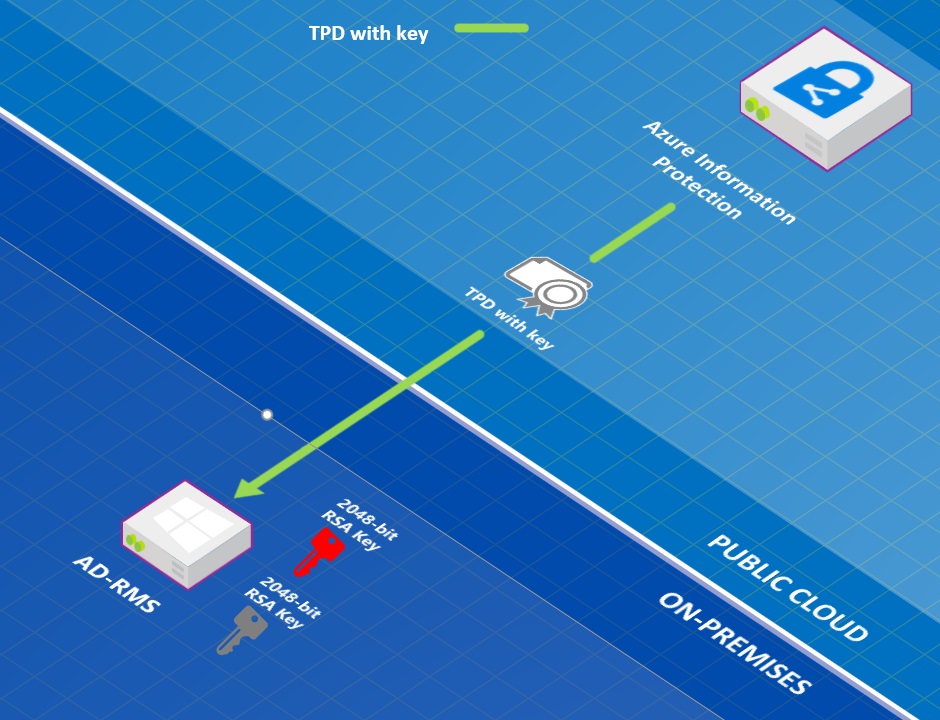
Which brings me to the post titled “How to prepare an Azure Information Protection “Cloud Exit” plan” where the Azure Information Protection team lay out the steps needed to move encrypted information out of the cloud to an on-premises location.
Could You Exit Office 365?
You might think that you will never exit the cloud. And indeed, it is Microsoft’s sincere wish that you should never even have such a thought because they’d like their tenants to continue paying the billions of dollars of monthly subscriptions that make Microsoft’s cloud properties so valuable.
It’s hard to consider making a cloud exit. Where would you go? The two obvious destinations are another cloud service or back on-premises, but both choices pose difficulties, as I discuss in a post about what people could do if an Office 365 disaster happened.
But if it’s difficult to contemplate moving unencrypted data from an Office 365 tenant to somewhere else, it’s even harder if you factor in encrypted data. Today, the amount of encrypted content (message, documents, and other data) inside Office 365 tenants is minuscule, so the difficulty only arises for tenants who embrace rights management and encryption for a good reason. In most cases, these organizations have used on-premises Active Directory Rights Management services and are accustomed to the intricacies of encryption.
The Complexity Created by Easier Encryption
Tomorrow, the situation might well be different. Microsoft has made it much easier for Office 365 tenants to encrypt content with features like the Encrypt-Only template that’s available to all Office 365 enterprise and business customers as well as Outlook.com premium users.
More importantly, sensitivity labels are now available. Office 365 E3 and E5 tenants have licenses to protect (encrypt) messages and documents with sensitivity labels. This requires a preview version of the Azure Information Protection client today, but the Office desktop apps (for Windows) are scheduled to have native support for sensitivity labels in 2H 2019. When all the Office apps (desktop, mobile, and online) support sensitivity labels, there’ll be no good reason why Office 365 users shouldn’t protect their most important information with encryption.
By 2022, I think between 2% and 4% of all Office 365 content will be protected. This figure sounds low, but the protected content will be the most important content. Over time, the percentage of protected content will increase steadily. You can also bet that Microsoft will enable support for sensitivity labels elsewhere in the Office 365 spectrum, like Teams channels or even individual messages.
The Upside and Downside for Tenants
Tenants seem to get a big upside from the change. Microsoft is doing the heavy lifting to make encryption easy and there’s lots of goodness in that. But it also means that tenant data will be even harder to move off Office 365.
Impact on ISVs
The impact will be larger on ISVs. Companies who create autosignature products already see the signs because their code can’t apply signatures to messages encrypted by Outlook. But any ISV that relies on the ability to process Office 365 data will be affected if they can’t deal with encrypted content. Take a backup service that offers tenants the ability to recreate a user mailbox should a major outage occur. If the restore operation doesn’t decrypt any encrypted messages when it reconstructs the mailbox, the user won’t be able to access those messages unless they can authenticate against Azure Active Directory.
Preparing for a Cloud Exit
This is a central point made in Microsoft’s post. They advise that anyone who thinks that they might need to exit the cloud should create a new Active Directory Rights Management on-premises cluster (perhaps on a virtual machine) and populate it with the Microsoft managed key generated automatically for Office 365 tenants for rights management. Super users can then decrypt the content copied over from the cloud.
Setting up a new rights management cluster and transferring keys is not something you can do on the fly when an Office 365 outage happens, or after you have exited the cloud. Instead, it’s a carefully planned exercise to be done upfront so that the outcome can be tested and verified to ensure that everything works if the need arises. Depending on how many messages and files need to be processed, decrypting content and returning that content to users could take considerable effort and time. In short, you can extract and decrypt your Office 365 content, but only with good preparation and much toil.
Encryption Creates Opportunities and Problems
Encryption has always brought complexity in terms of key management. Microsoft has done a lot to take complexity out of the equation, but that doesn’t mean that organizations can simply deploy without thought. As we enter a world where encrypted content is more common, we all need to figure out what it means for operations, products, and long-term strategy.