How do I configure SMB Security in Windows Server 2012?
Windows Server 2012 (and Windows 8) introduce a new version of the Server Message Block (SMB) protocol for transferring files across a network. One of the most interesting new features is the ability to encrypt files over the wire between two supported clients. SMB 2.1 in Windows Server 2008 R2 (and Windows 7) was able to sign SMB packets to prevent spoofing, but not encrypt the actual data. Prior to Windows Server 2012, the only way to encrypt file data in transit was to configure IPsec. SMB 3.0 encryption can be enabled, either per share or file server, without any special planning.
Disable SMB 1.o
Microsoft recommends that unless you have clients running Windows XP or earlier, you should disable SMB 1.0. Do this in a preproduction lab environment before rolling out the change to your production systems. However, there are still certain scenarios where SMB 1.0 is still required, such as when the computer browser service is enabled in Vista (or later).
Windows Server 2012 has a new PowerShell command that makes it easy to get the configuration status of SMB protocols on the server, and optionally enable or disable SMB protocol support.
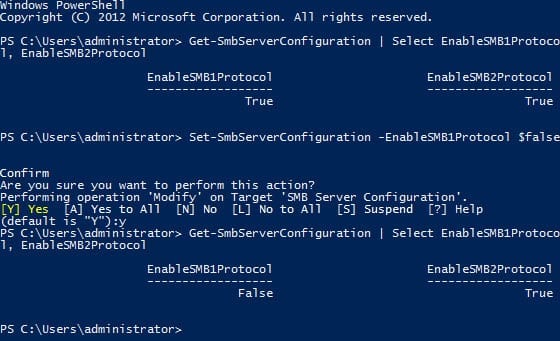
To get the current SMB protocol status on Windows Server 2012: Logon to the server as a local administrator, open a PowerShell prompt from the Start screen or icon on the desktop Taskbar, and run the following command:
Get-SmbServerConfiguration | Select EnableSMB1Protocol, EnableSMB2Protocol
Note that there’s no separate command to enable or disable SMB 3.0, as it cannot operate independently of SMB 2.1.
Now, run the following command to disable SMB 1.0 and confirm the action when prompted:
Set-SmbServerConfiguration -EnableSMB1Protocol $false
After that, run the first command again. You should see that SMB 1 has been successfully disabled.
Enable SMB 3.0 Encryption
You can enable encryption per file share or for the entire server. SMB 3.0 uses the AES-CCM algorithm for both encryption and signing. Using the same PowerShell cmdlet as above, run the following command to enable SMB 3.0 Encryption for all file shares:
Set-SmbServerConfiguration –EncryptData $true
To enable encryption for a specific file share, run the following PowerShell command, replacing <sharename> with name of the file share for which you want to enable encryption:
Set-SmbShare –Name <sharename> -EncryptData $true
When enabled, SMB 3.0 encryption will encrypt file data between devices that support SMB 3.0. Clients that don’t support SMB 3.0 will not be able to connect to the file server or share where encryption is turned on. While not recommended, this behavior can be changed by running the Set-SmbServerConfiguration –RejectUnencryptedAccess $false PowerShell command.
Related Article: