Conditional Access Blocks Downloads of Office 365 Attachments and Documents
Office 365 and Conditional Access
The blog entitled “Read-Only and Attachment Download Restrictions in Exchange Online” by MVP Brian Reid prompted me to think about Azure Active Directory conditional access policies. These policies have been around for a while. For instance, in April 2017, I reviewed how to use conditional access to enforce MFA when users opened documents protected by Azure Information Protection. But it does take time for any technology to find its way into all aspects of a large suite like Office 365.
To change behavior at an application level, conditional access policies depend on an interaction between application settings and policy settings. In short, Azure Active Directory watches inbound sign-ins and notes if a user is subject to control. This information is passed to applications, which impose the restriction.
Recent changes improve the interaction between the base Office 365 workloads and conditional access policies. Briefly, you can configure OWA and SharePoint Online (including OneDrive for Business) to stop users downloading attachments (OWA) or items in document libraries (SharePoint and OneDrive.
I followed the steps laid out in Brian’s post to create a conditional access policy. To make things easier to manage, I created a new security group with the intention that the members of this group would be subject to the new policy.
Updating Exchange
OWA uses OWA mailbox policies to control settings. Every Office 365 has a default OWA mailbox policy and you could update it with a new value for the ConditionalAccessPolicy setting, which is how OWA knows what to do when a mailbox is subject to a conditional access policy. The documentation for settings in a OWA mailbox policy tells us that ConditionalAccessPolicy supports these values:
- Off: No conditional access policy is applied to OWA. This is the default
- ReadOnly: Users can’t download attachments to their local computer and can’t enable Offline Mode on non-compliant computers. They can still view attachments in the browser.
- ReadOnlyPlusAttachmentsBlocked: All restrictions from ReadOnly apply, but users can’t view attachments in the browser.
I decided to create a new OWA mailbox policy. This makes it easy to find mailboxes subject to the policy and doesn’t interfere with any other settings that might be active. Creating a new policy and setting the value to block attachment downloads is easy with PowerShell:
New-OwaMailboxPolicy -Name "Restricted Download Access" Set-OwaMailboxPolicy -Identity "Restricted Download Access" -ConditionalAccessPolicy ReadOnly
The Set-CASMailbox cmdlet assigns the policy for a mailbox. For example:
Set-CASMailbox -Identity "Sanjay" -OwaMailboxPolicy "Restricted Download Access"
Automating the Flow
Remember that you must add the user to both the security group and update their OWA mailbox policy before conditional access can work. To automate the process, we can write a little code to do both tasks. Feel free to improve and expand!
$GroupForBlocks = "ad09f554-2719-442f-8837-b747213e633e"
$Check = (Read-Host "Enter user principal name to block)")
$User = (Get-AzureADUser -ObjectId $Check -ErrorAction SilentlyContinue)
If (-not $User) {Write-Host $Check "not found"}
Else {Add-AzureADGroupMember -ObjectId $GroupForBlocks -RefObjectId $User.ObjectId
Set-CASMailbox -Identity $User.ObjectId -OWAMailboxPolicy "Restricted Download Access"
Write-Host $User.UserPrincipalName "updated for conditional access"}
The Effect of Conditional Access
CAS updates take about 30 minutes to replicate and become effective. When the policy is effective, users under its control will notice that choices they normally have for attachments (Figure 1) disappear and are replaced by a banner to inform them that they have restricted access (Figure 2).
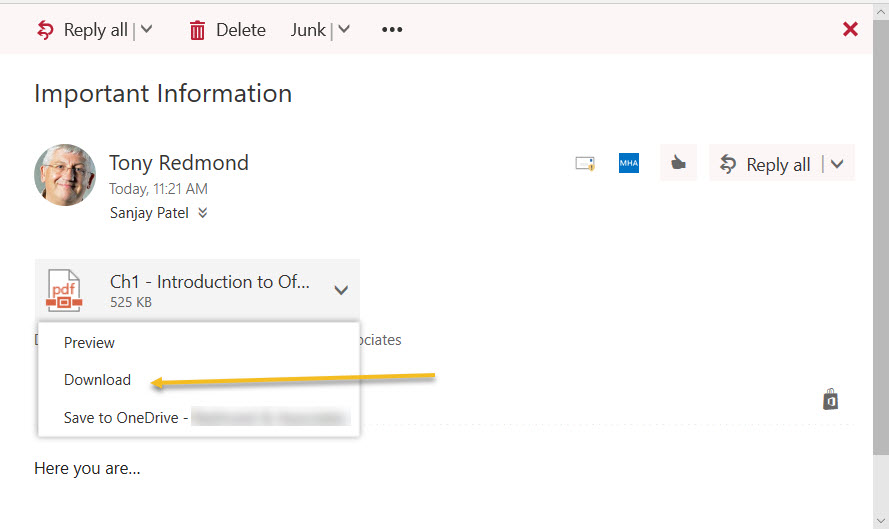
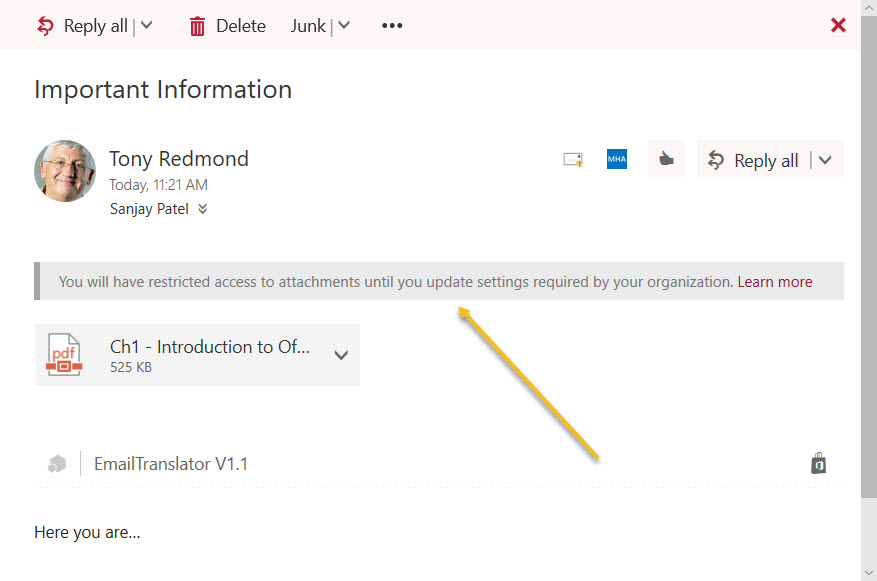
Restricted access means that the user can preview the file using Office Online or save it to their OneDrive for Business account. They can also forward the email with the attachment to other recipients. However, they can’t download the attachment and open it with a desktop application or save the file to a local drive.
Some training is needed to acquaint users with what to do when they are restricted. The Learn More link in the restricted access banner (Figure 2) takes them a page on Microsoft’s web site called “Using managed devices to get work done.”
Microsoft obviously chose the banner text in the belief that tenants who use conditional access policies will do so as part of a device management strategy based around their InTune technology. However, you can deploy conditional access policies without InTune and currently there’s no way to swap a company-authored page to replace Microsoft’s text. This situation might change in the future as a setting called ConditionalAccessFeatures already exists for OWA mailbox policies that Microsoft might use to give tenants more control over how the feature works.
Only for OWA
It’s important to emphasize that the conditional access policy only affects OWA. Other Exchange clients, like Outlook for Windows, Outlook mobile for IOS and Android, and any ActiveSync client, don’t respect OWA mailbox settings and know nothing about conditional access restricting downloads.
Controlling SharePoint
Exercising control email attachments is all very well, but controlling the download of documents from SharePoint Online document libraries is possibly even more important, especially because applications like Teams and Office 365 Groups make it easier for users to store documents in SharePoint.
SharePoint’s application setting we need for our conditional access policy is found in the Access Control section of the new SharePoint Online Admin Center. Click Unmanaged devices and then select Allow limited web-only access (Figure 3).
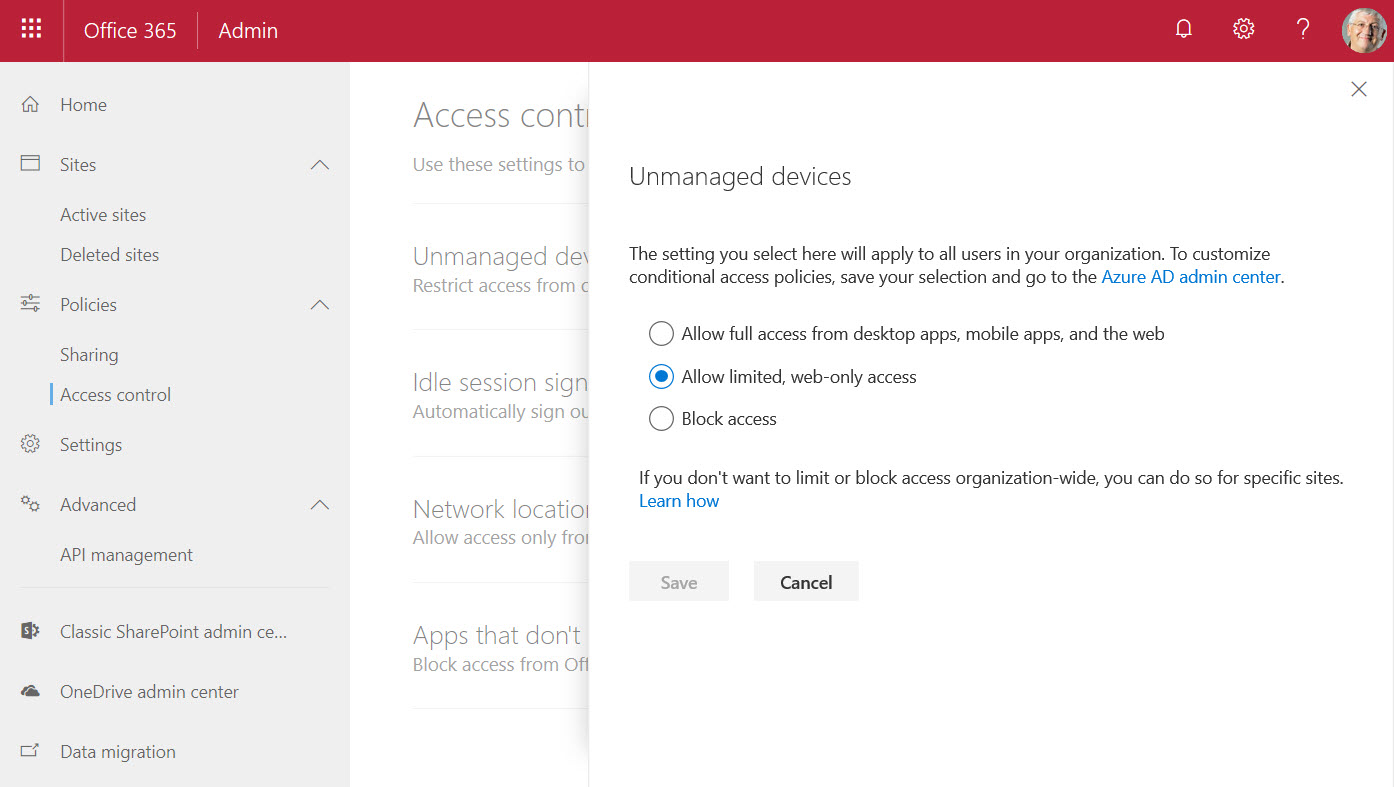
The same effect is gained by running the Set-SPOTenant PowerShell cmdlet. Bizarrely, the ConditionAccessPolicy setting is not covered in the documentation, but here’s what you need to do:
Set-SPOTenant -ConditionalAccessPolicy AllowLimitedAccess
Fortunately, blogs like this piece by Vasil Michev explain the mysteries of conditional access for SharePoint Online.
Blocking SharePoint Downloads
The block becomes effective for SharePoint Online and OneDrive for Business soon after updating the tenant configuration. Users in the control group see a new banner and the ability to open an Office document in a desktop application is removed (Figure 4), but they can be opened in Office Online (if they’re not protected with a sensitivity label). Non-Office documents like PDFs can only be opened in preview. Users can still upload or share documents, but they can’t copy or move them.
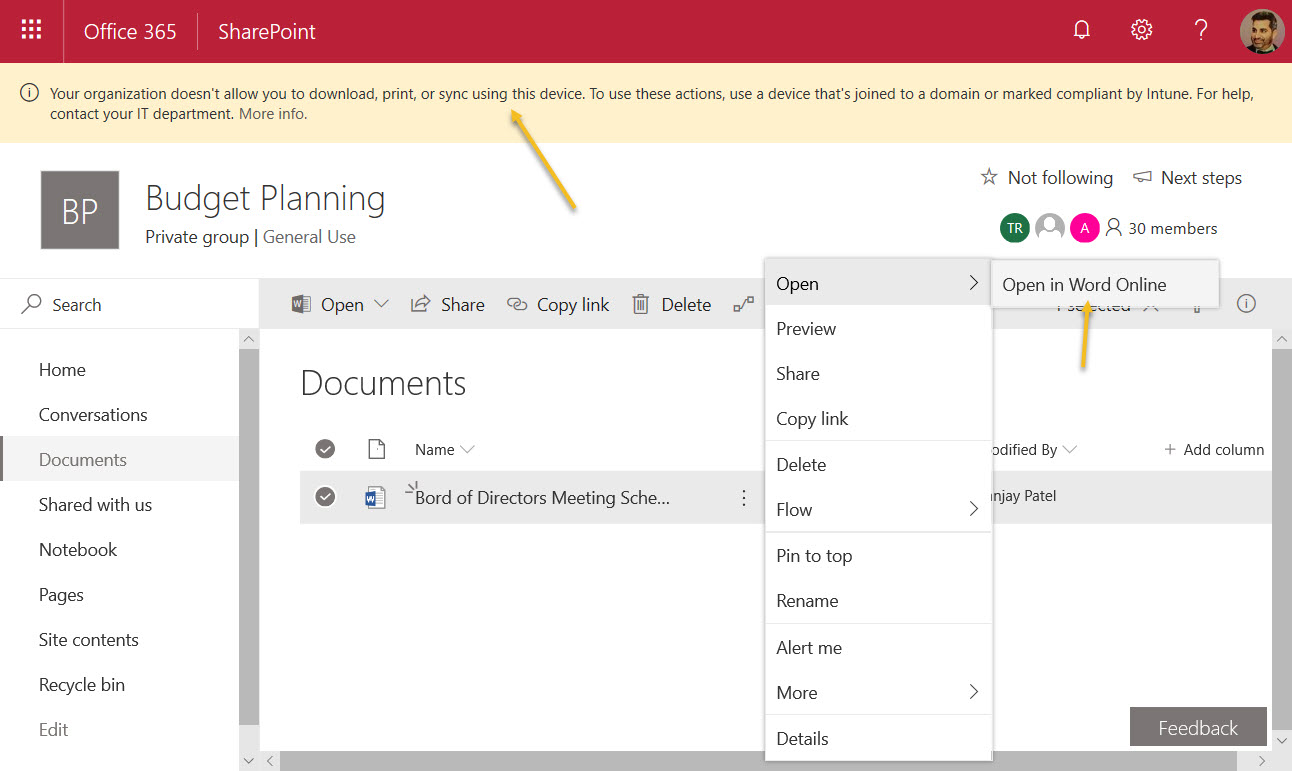
A Block in Teams and Planner Too
The block extends into Teams, where any attempt to download a file from a team’s document library fails through the Files view (Figure 5) or after opening Files in SharePoint.
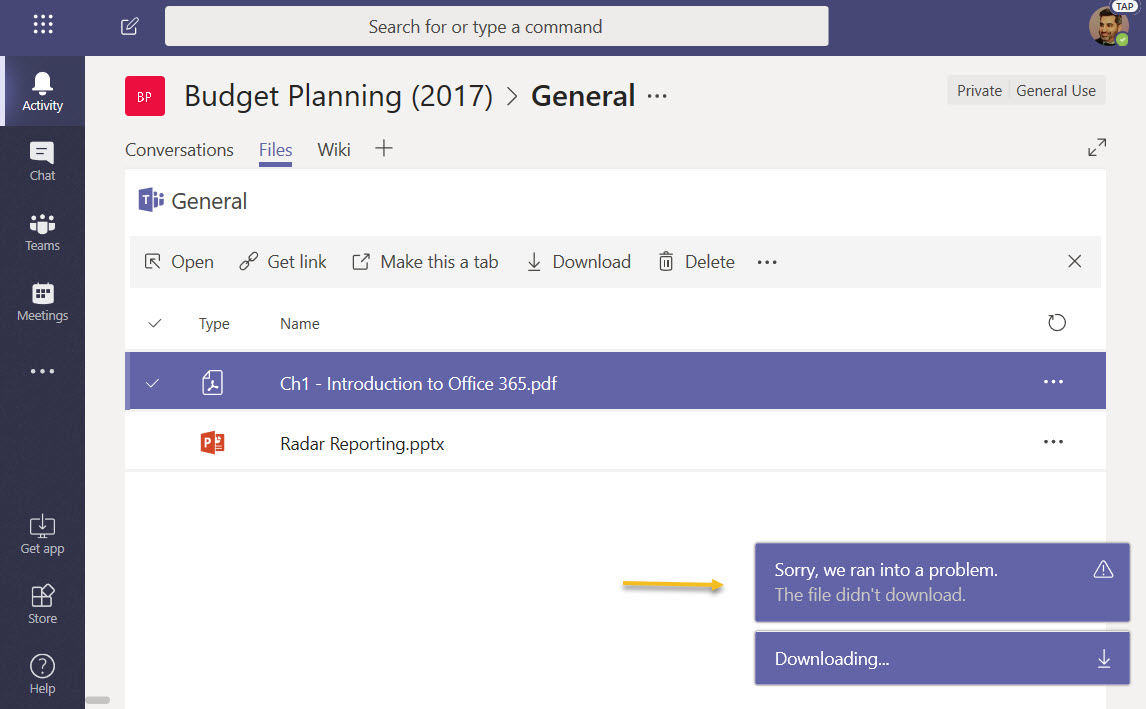
Planner behaves much the same way as Teams, with the exception that you see an error if you try to view a non-Office attachment for a task. This is because Planner normally downloads these files to involve their native application to view the contents and this can’t happen with the block in place.
More Licenses Needed
Conditional access policies are an Azure Active Directory premium feature, so the accounts who come within the scope of these policies must be assigned an Azure AD Premium P1 license. In most cases, this is not an issue because the organizations who are interested in this kind of feature usually invest in Enterprise Security and Mobility to manage devices, or buy Microsoft 365 licenses, which include EM&S.
If you’re not in that category, you might not see the benefit of investing in extra licenses just to use conditional access policies. That’s certainly an understandable position as costs can mount quickly. However, over the last two years, Microsoft has invested heavily in new premium features for Azure Active Directory, so perhaps it’s worth reviewing the up-to-date situation, especially in the context of ongoing security challenges.




