
In this article, we are going to take a brief look at what Azure Sphere is and how it is helping to protect Internet of Things (IoT) devices with additional security overlay.
In today’s world, we are surrounded by billions of devices – all with microcontrollers embedded in them for control and to add logic. More and more, these devices are connecting to the Internet to extend the their functionality. And to enable manufacturers to send over-the-air (OTA) updates or receive logging and metrics.
Connecting devices to a network, let alone the Internet, is not without risks. We have all heard about hackers breaking into enterprise networks via small microcontroller devices that were connected to the corporate intranet. This absolutely can and does happen.
But how can you prevent these kinds of attacks? Clearly the benefit of such devices connecting to a network is huge, especially in the climate and rise of IoT. Looking for a way to protect and secure microcontroller unit (MCU) based devices, Microsoft came up with an ingenious way to manage their security.
What is Azure Sphere and Azure Sphere OS?
Azure Sphere is not exactly a single product; it is a collection of 3 core items that are known as ‘Azure Sphere’.
- The MCU – A microcontroller unit that is secured and can connect to the Internet.
- The OS – A customized Linux-based operating system.
- The Cloud Based Security Service – A platform that provides a continuous security service for authentication, authorization, and renewal of security principles.
Azure Sphere is an end-to-end platform that enables us all to build secure IoT devices. Right the way from secured silicon that extends all the way through the operating system and right up to the cloud platform.
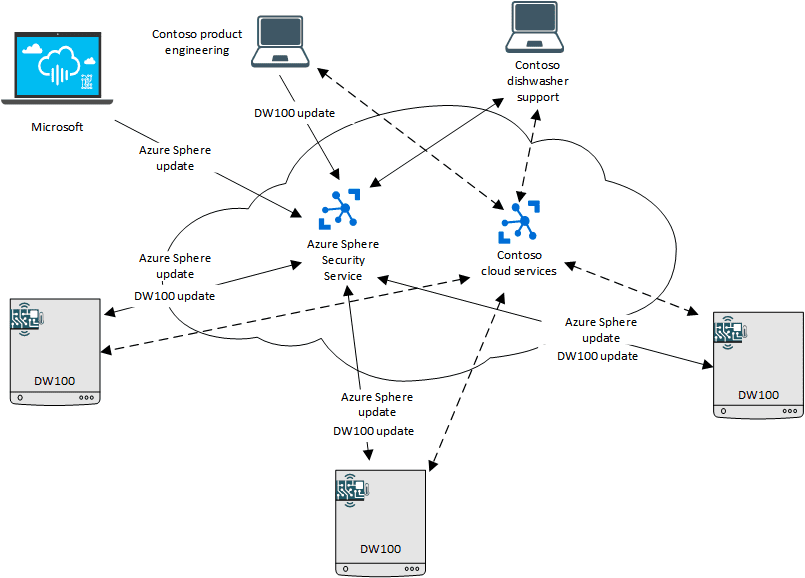
Connected devices can leverage all the great features and functionality offered by the Azure cloud platform, like the diverse catalogue of preconfigured solutions that we can choose from to build and securely connect our intelligent devices.
We are also able to leverage Azure’s OTA update functionality. And the security improvements that Microsoft has implemented over its platforms. As well as being able to manage and control these devices via the Azure IoT Hub or develop applications with Azure IoT Central.
These three components of Azure Sphere collectively go some way to addressing a myriad of security requirements. In fact, Microsoft’s own experience and development over the years has led it to develop a listing of seven properties of a highly secure device, which Azure Sphere addresses.
What are the seven properties of highly secured devices?
One of the main goals of Azure Sphere is the ability to provide a highly secure platform at as low a cost as possible. Allowing low cost MCU’s to be utilized in a myriad of devices from network connected appliances and sensors, to toys and games, into the plethora of devices that will exponentially be growing over the coming years.
Microsoft has decades of experience dealing with Internet security. And as part of Azure Sphere development, the team has identified what a highly secured device should look like with its seven properties of highly secured devices.
- Hardware-based root of trust – Having this root of trust based in hardware ensures that any device and its identity are intrinsically linked together. It prevents any device forgery or device spoofing. Every Azure Sphere crossover MCU can be identified by an unforgeable crypto key that has been generated and protected by the Microsoft designed Pluton security subsystem hardware.
- Defense in Depth – Ensure multiple layers of security to provide multiple mitigations against attack on any of these layers. By default, Azure Sphere validates that the layer above it is secured.
- Small, trusted computing base – The majority of an Azure Sphere device’s software remains outside of the computing base, which limits the attack surface. The small, trusted computing base in this case would comprise a security monitor, the Pluton runtime and subsystem, which are provided by Microsoft to run on the trusted computing base.
- Dynamic Compartments – Azure Sphere certified silicon chips all contain countermeasures and hardware firewalls to prevent any security breaches from spreading from one subsystem to another. Code corruption can be controlled with a constrained ‘sandbox’ environment.
- Password-less authentication – Certificate based authentication, which is verified and validated with an unforgeable crypto key, provides a strong authentication mechanism when compared to passwords. The Azure Sphere platform ensures that it will only accept signed communications based on these certificates from every software component and device to cloud, or cloud to device, communication.
- Error Reporting – Use of error reporting to exploit devices is very typical in today’s security attack techniques. Consistent and constant communications from devices to the cloud platform of error reporting provides early warning of any potential problems. This will enable developers to spot and rectify possible issues earlier.
- Renewable Security – With Azure Sphere, the device software can be automatically updated to ensure any known vulnerabilities or security breaches are mitigated. This does not need any intervention from a product manufacturer or end user, making security updates truly seamless and automatic. This is all achieved with the use of Azure Sphere OS and the Azure Sphere Security Service.
With the above list of principles, you can see how on their own, they are robust. All with the ideology of ensuring heightened security for your devices. When used all together, the end-to-end security of hardware MCU based devices can be reliably secured from device to cloud. And devices can leverage the security updating mechanisms supplied by Azure Sphere and the Azure Cloud in general.
Azure Sphere architecture
Microsoft has provided some documentation on the architecture of the three components of Azure Sphere. Azure Sphere MCU Hardware devices take on the following architecture. A single Azure Sphere crossover MCU consists of multiple cores sat on a single silicon die as follows:
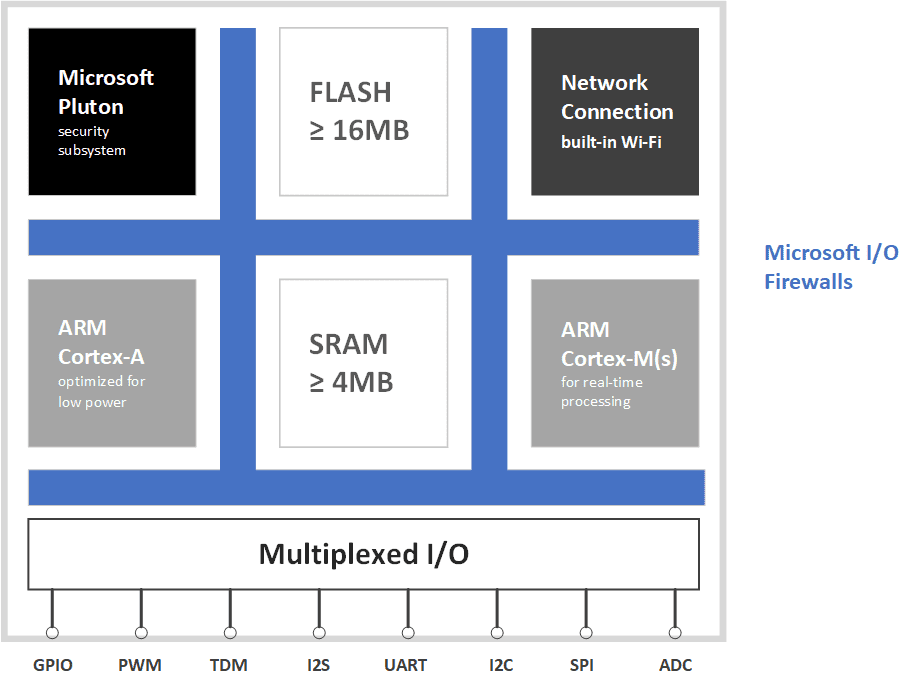
Each core and associated subsystem is placed into a different trust domain. The Pluton security subsystem is then employed to manage security and make sure that the layer above hasn’t been compromised.
Without delving into too much detail, the hardware architecture can be listed as follows:
- Microsoft Pluton security subsystem
- High-Level Application Core
- Real-time core(s)
- Connectivity and communications
- Multiplexed Input/Output (I/O)
- Microsoft Firewalls
- Integrated RAM and flash memory
Looking at the Operating System software architecture, Azure Sphere handles security as follows:
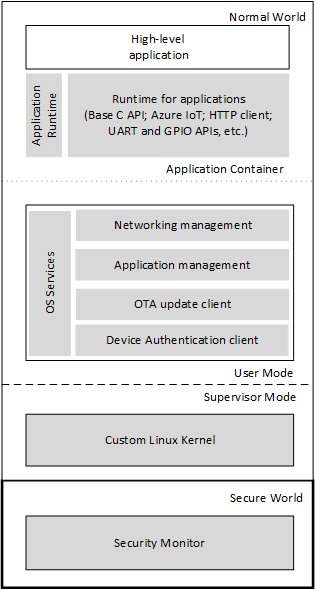
The high-level application depicted above runs the Azure Sphere OS. As well as any device specific high-level application that communicates with the Internet and real-time cores on the MCU.
The parts of the software architecture that Microsoft supports are highlighted in grey above. So, you can see, developers simply deploy application code on to the MCU. And then they can then use the entire Azure Sphere ecosystem to secure and manage devices.
Components of the Software Architecture:
- Application Runtime
- OS Services
- Custom Linux Kernel
- Security Monitor
Customers using Azure Sphere
Microsoft has some great use case stories from large global businesses that can be used for inspiration.
Starbucks is using Azure Sphere guardian devices to enable them to securely connect their coffee machines to provide real-time performance metrics. And to enable predictive maintenance. As well as enabling remote updates for these machines.
Purell Smartlink/GOJO Industries have built securely connected sanitizer dispensers. With end-to-end security provided by Azure Sphere, and the integration with the Azure IoT Platform, GOJO was able to deliver comprehensive data on care giver behavior in hospitals.
OSO Hotwater has improved energy efficiency and reduced service disruptions with an Azure Sphere enabled water heater that securely connects to grid companies and cities.
Sysinno monitors air quality with Azure Sphere enabled sensor devices. The devices securely connect and monitor large environments. Integration with Azure IoT Hub, and the renewable security of Azure Sphere, helps to improve performance and reduce operating costs.
Getting started with Azure Sphere?
Microsoft has made things relatively simple to get started exploring, building devices and applications using Azure Sphere enabled hardware.
You can purchase an Azure Sphere Development Kit. These kits provide you with everything that you need to begin your learning journey. And to start prototyping and developing Azure Sphere applications.
Once you have a developer kit, you can download the Azure Sphere SDK and begin building applications using the tutorial documentation.



