Microsoft Sentinel Launches New Log4j Vulnerability Solution In Public Preview
Microsoft has announced some important updates for Microsoft Sentinel, its scalable cloud-native SIEM tool that provides AI-powered security analytics in enterprise environments. The Redmond giant has launched a new solution in public preview that should help IT Admins to detect Apache Log4j vulnerabilities.
Last week, Microsoft acknowledged the emergence of an Apache Log4j vulnerability (CVE-2021-44228) that is currently being exploited by threat actors to install malwares by gaining remote access to compromised devices. “The vulnerability allows unauthenticated remote code execution and is triggered when a specially crafted string provided by the attacker through a variety of different input vectors is parsed and processed by the Log4j 2 vulnerable component,” the company explained.
Complete solution in Microsoft Sentinel to easily track, monitor, and investigate the Log4Shell exploit
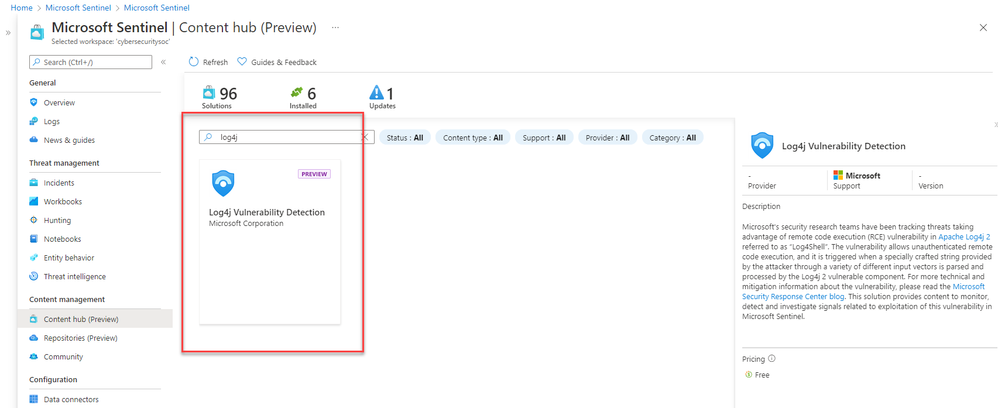
With the new Log4j exploit detection tool, Microsoft is offering enterprise customers a complete solution to easily track, monitor, as well as investigate the Log4Shell exploit targeting the Log4j flaw. Specifically, IT admins will be able to access the new Log4j exploit detection solution via Microsoft Sentinel Content Hub.
However, a Microsoft representative has confirmed that enterprise customers with active Microsoft Sentinel subscriptions will have to download and install the tool from GitHub manually. “Solutions can’t be deployed into subscriptions from Microsoft Azure Cloud Solution Providers. However, you can manually add these detections into your workspace from our Github repo,” said Sarah Young, Senior Program Manager for Azure Security at Microsoft.
To deploy the new Log4j exploit detection tool, IT Admins will need to follow these steps:
- First of all, log in to the Microsoft Sentinel portal and head to the navigation menu.
- Click the Content hub (Preview) option available under the Content Management section and then type Log4j in the search bar.
- Select the “Log4j vulnerability detection” solution, and finally click the “Install” button.
Microsoft is still investigating the Log4j vulnerability, and it’s recommending enterprise customers check for the latest updates regularly. The company is also keeping track of all the indicators of compromise (IOCs) related to the Log4j security flaw on the Microsoft Threat Intelligence Center (MSTIC), and you can find the full list on this GitHub page.