
Apache Superset has released fixes to patch a security flaw in the default configuration that could lead to remote code execution. Tracked as CVE-2023-27524, the vulnerability allows threat actors to potentially steal sensitive data, harvest credentials, and then execute malicious code.
Apache Superset is an open-source data exploration and virtualization solution. It enables users to create interactive dashboards, graphs, and charts based on NoSQL databases, SQL databases, flat files, and other data sources. Apache Superset provides various advanced analytics capabilities such as ad-hoc data analysis, custom SQL queries, and integration with machine learning models.
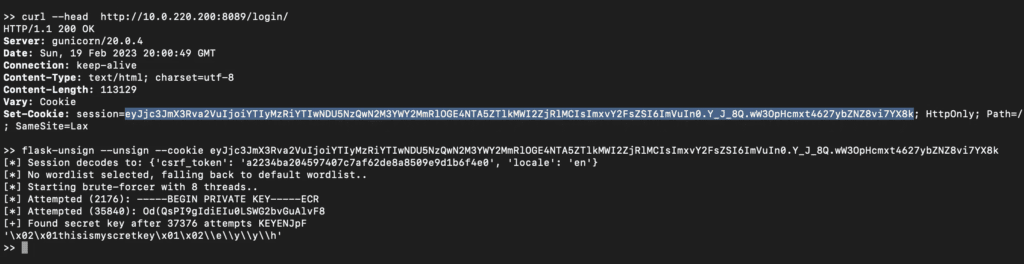
In a recent advisory, Security firm Horizon3.ai explained that Apache Superset signs authentication session cookies with a default Flask Secret Key. The attacker could use the value of the default key to generate and sign cookies for authentication purposes.
“The security of the web application depends critically on ensuring the SECRET_KEY is actually secret. If the SECRET_KEY is exposed, an attacker with no prior privileges could generate and sign their own cookies and access the application, masquerading as a legitimate user,” explained Naveen Sunkavally, Chief Architect at Horizon3.ai.
Horizon3.ai releases script to discover the Apache Superset flaw
The security firm found that around 2,000 vulnerable Superset instances relied on the default configuration, including government agencies, corporations, and universities. As a result, any attacker with administrative privileges can log in to the vulnerable servers. The researchers notified some organizations to address the vulnerability and protect their enterprise networks.
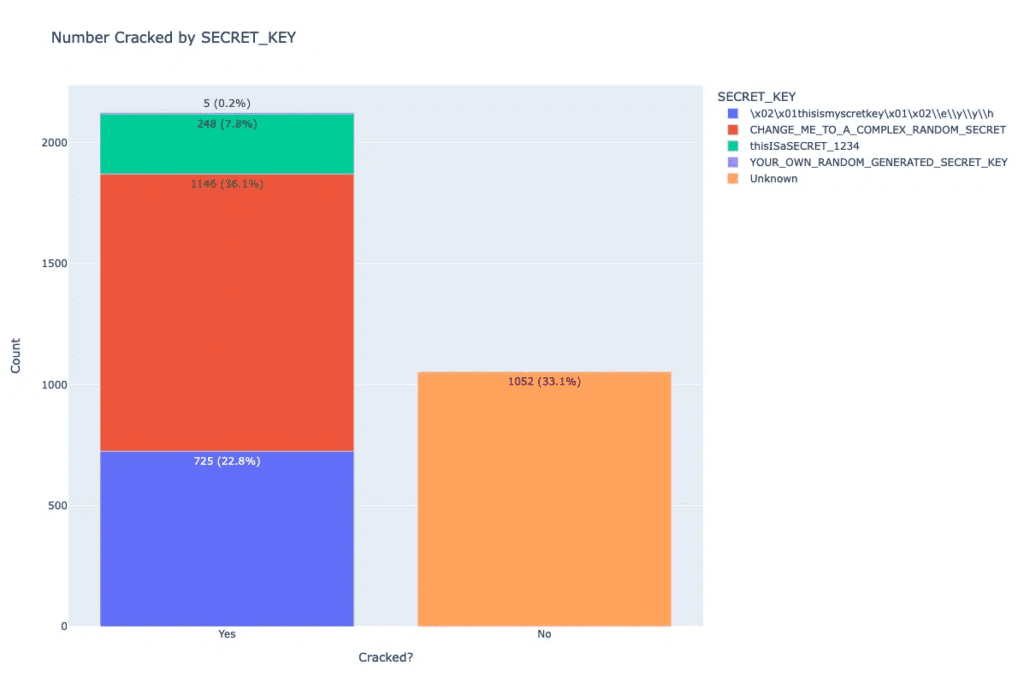
Horizon3.ai has released a script to help IT admins find vulnerable Apache Superset instances in their organization. “It’s commonly accepted that users don’t read documentation and applications should be designed to force users along a path where they have no choice but to be secure by default,” Sunkavally added. “The best approach is to take the choice away from users and require them to take deliberate actions to be purposefully insecure.”


