In today’s Ask the Admin, I’ll explain how a new set of APIs in Windows 10 and Windows Server 2016 can be used to block malicious activity.
It’s long been recognized that signature-based antivirus protection alone cannot adequately protect devices due to the sheer number of viruses in the wild and the speed at which they mutate. One of the issues of scanning files on disk and comparing them against a known database of threats is that hackers use various techniques to obfuscate the actual code that will run in memory. Let’s through some simple examples of the ways hackers can avoid detection.
Using dynamic languages, such as VBScript and Ruby, much of the work is done at runtime rather than at the compilation stage. Objects can be created, by adding methods and properties, when the code is run; we don’t need to define objects in advance. Applying that knowledge, code can be written to cover up what will execute at runtime, helping to avoid detection.
Scripting engines and shells, such as VBScript and PowerShell, are an ideal target because they are built into the operating system and used by system administrators, who hackers often target due to their likely overprivileged access to systems.
Avoiding Detection
Instead of simply using Write-Host ‘You have been hacked’ to output a message to the console, we can use string concatenation to change the script to avoid detection, but retrieve the same output at the console:
Function Hack-Me
{
Invoke-Expression (“Write-Host ‘You have ” + “been hacked’”)
}
Hack-Me
Once the AV signatures have been updated to detect the technique used above, something more sophisticated is required, such as Base64 encoding or algorithmic obfuscation. The following script encodes Write-Host ‘You have been hacked’ to Base64, and stores the results in a variable ($EncodedText):
$Text = “Write-Host ‘You have ” + “been hacked’” $Bytes = [System.Text.Encoding]::Unicode.GetBytes($Text) $EncodedText =[Convert]::ToBase64String($Bytes)
We can then use the encoded text to obfuscate our intentions in a piece of malicious code:
Function Hack-Me
{
$code = ‘VwByAGkAdABlAC0ASABvAHMAdAAgABggWQBvAHUAIABoAGEAdgBlACAAYgBlAGUAbgAgAGgAYQBjAGsAZQBkABkg’
$newcode = [System.Text.Encoding]::Unicode.GetString([System.Convert]::FromBase64String($code))
Invoke-Expression $newcode
}
Hack-Me
As you can see, this is a game of cat and mouse, and while what I’ve shown above are simple examples of how hackers use obfuscation, it gives you an idea of their methods for evading detection.
Antivirus solutions use emulators to execute code in a sandboxed environment to try and detect any suspicious behavior using heuristic analysis. But like other defenses, hackers have plenty of tricks up their sleeves to avoid detection, including ‘prodding’ (i.e., check whether the code is running in a real or emulated environment), or adding lengthy time delays to code, forcing the emulator to time out. And while emulators are part of most antivirus solutions, they’re also resource intensive and not difficult to bypass.
Antimalware Scan Interface
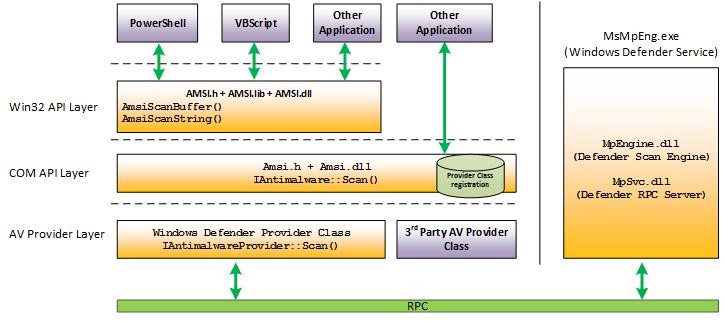
Whatever method a hacker uses to obfuscate their wares, the scripting engine must finally be supplied with plain code, and at this point, Microsoft’s Antimalware Scan Interface APIs can be used to scan the code in memory. AMSI can also scan files, streams, and provide content source URL/IP reputation checks. Any application can make use of the APIs, whether it’s an antivirus solution or messaging app, to get a better insight into the code in memory, and the opportunity to stop it from running before it does any harm. Windows Defender already uses AMSI to provide better protection.
Like any other defense, AMSI is not a panacea, and ways to bypass were found at Black Hat 2016. It remains to be seen whether Microsoft has been able to plug the holes found by researchers, but nevertheless, defense-in-depth is always the best strategy. For instance, removing administrative privileges from users, implementing application control, and antivirus protection, are all essential components of any defense-in-depth plan.



