
Key Takeaways:
- Hackers are using the zero-point font obfuscation technique to target Microsoft Outlook users.
- These phishing emails are designed to deceive recipients by appearing trustworthy rather than evading automated detection.
- This emerging phishing tactic underscores the need for organizations to educate employees about recognizing and countering such scams, bolstering their cybersecurity defenses.
Security researchers have discovered that hackers are now employing a new zero-point font obfuscation technique to target Microsoft Outlook users. Unlike traditional phishing emails that try to evade automated detection, this novel approach aims to deceive recipients by making emails appear more trustworthy.
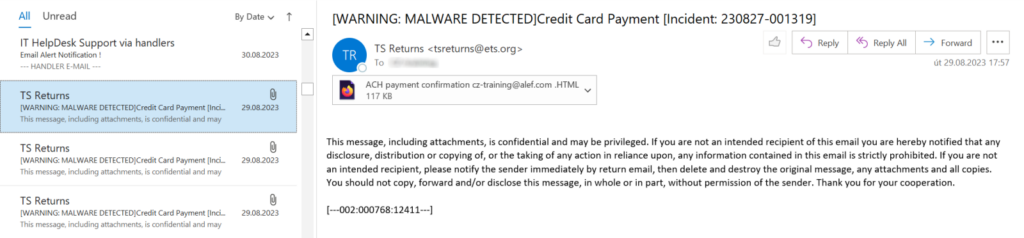
In a recent report published by the SANS Internet Storm Center, cybersecurity analyst Jan Kopriva found a new phishing email that used text written in a font with zero-pixel size. ZeroFont Phishing is an obfuscation technique that lets hackers insert hidden words written in zero font size throughout the email body.
Typically, the ZeroFont technique is used to make it harder for automated phishing detection tools to flag suspicious email messages. However, the phishing campaign identified by the security researcher was designed for a completely different purpose.
“Nevertheless, the “invisible” text in the e-mail which was delivered to our handler e-mail address last Friday did not serve the usual purpose – it wasn’t intended to hinder automated scanners from identifying the message as potentially fraudulent/malicious, but instead to make the message appear more trustworthy to the recipient,” Kopriva explained.
Hidden fake antivirus scans in Outlook raise security concerns
In Microsoft Outlook, the email listing pane contained the subject and a line that indicated that a threat protection tool had scanned the email message. As seen in the screenshot above, the following text was embedded in zero font size under the subject line: “Scanned and secured by Isc®Advanced Threat protection (APT): 9/22/2023T6:42 AM.”
The security researcher mentioned that it’s not the first time that this technique has been used by threat actors in a sophisticated phishing campaign. This highlights the importance of promptly informing employees about this evolving threat and providing them with the necessary training to detect and respond to fraudulent emails effectively. This proactive approach should help organizations to protect sensitive data and maintain a robust security posture.



