
Key Takeaways:
- Microsoft disclosed a critical vulnerability in XZ Utils, a widely used open-source data compression utility on Linux systems.
- The backdoor could enable hackers to bypass secure shell authentication, potentially leading to unauthorized access and exploitation of infected systems.
- The vulnerability affects various Linux distributions, including Fedora 41, Kali Linux, and openSUSE variants.
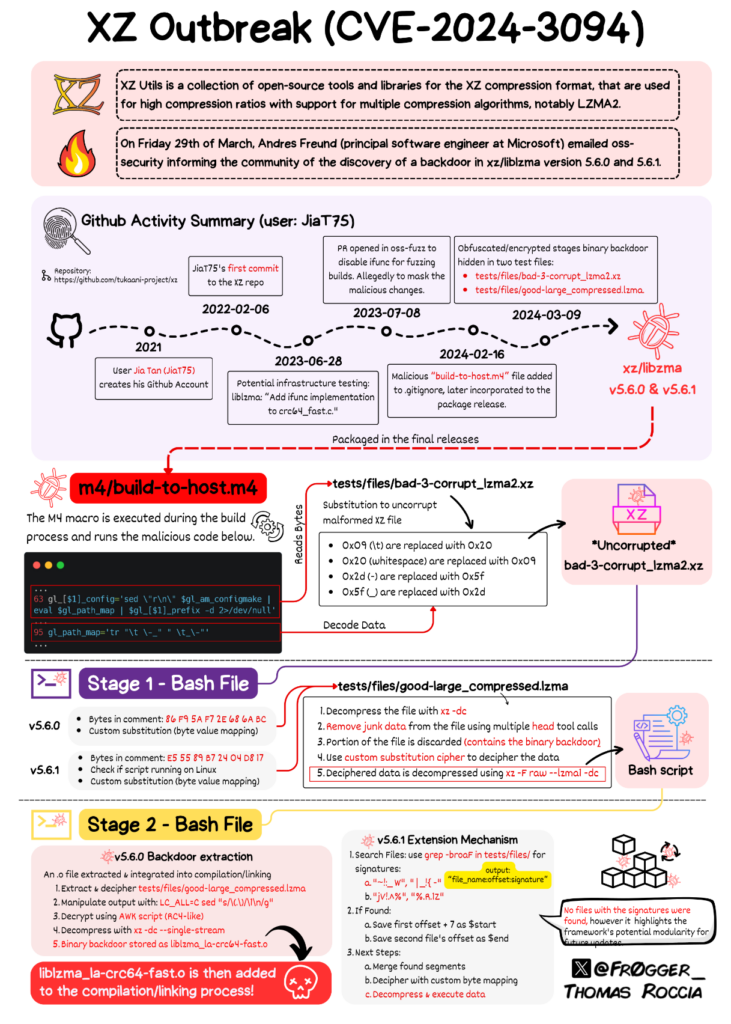
Microsoft has recently disclosed a new vulnerability in an open-source data compression utility present in almost all Linux distributions. The backdoor in XZ Utils could enable hackers to bypass secure shell (sshd) authentication and gain unauthorized access to an infected system.
What is XZ Utils?
XZ is a command-line utility that provides lossless data compression on virtually all Unix-like operating systems, including Linux. It offers critical functionalities required for compressing and decompressing data across various operations. The XZ utility is commonly used to compress large files and directories to save bandwidth or disk space when transferring files over the Internet.
What does the XZ Backdoor Util do?
Microsoft developer Andres Freund recently discovered the backdoor in XZ Utils while performance issues on some Debian installations. He found that the problem was triggered by updates that had been made to XZ Utils. On March 29, Freund disclosed that someone had been intentionally injecting malicious code into the compression software.
According to Freund, the backdoor (tracked as CVE-2024-3094) is present in XZ Utils versions 5.6.0 and 5.6.1. It affected the upstream XZ repository and associated archived download packages (called “tarballs”). The vulnerability could allow remote hackers to deploy malware, steal encryption keys, and deliver new payloads.
The backdoor vulnerability affects various Linux distributions, including Fedora 41, Kali Linux, Fedora Rawhide, openSUSE MicroOS, openSUSE Tumbleweed, and some experimental versions of Debian. However, the malware doesn’t impact other popular Linux distributions such as Red Hat Enterprise, Amazon Linux and Ubuntu, as well as SUSE Linux Enterprise and Leap.
What should organizations do to protect their devices?
The US Cybersecurity and Infrastructure Security Agency (CISA) has urged organizations to downgrade to an earlier version (such as version 5.4.6 Stable) of XZ Utils. Additionally, it’s recommended to thoroughly inspect enterprise environments for any signs of potential malicious activities.
Meanwhile, Microsoft recommends that customers evaluate their exposure to the vulnerability using security tools like Defender for Cloud, Microsoft Security Exposure Management, and Defender Vulnerability Management. These solutions can help in identifying devices that have the vulnerable software version installed.


