
Key Takeaways:
- Security researchers have identified critical security flaws in Windows Hello fingerprint authentication on laptops from major manufacturers, including Dell, Lenovo, and Microsoft.
- The fingerprint sensors on these laptops use “Match on Chip” technology for biometric verification on internal microprocessors, yet this approach doesn’t inherently protect against potential spoofing attacks.
- The researchers recommend manufacturers to enable Microsoft’s Secure Device Connection Protocol (SDCP) to ensure encrypted communication with fingerprint sensors.
Cybersecurity researchers from Blackwing HQ have managed to bypass Windows Hello fingerprint authentication on three different laptops from Dell, Lenovo, and Microsoft. The penetration tests were carried out at the request of Microsoft to assess the security of the fingerprint sensors used in these devices.
Windows Hello is a biometric authentication feature that allows users to login to their devices with a PIN (Personal Identification Number), fingerprint recognition, and facial recognition. Once configured, the fingerprint authentication feature allows users to verify their identity and access Windows devices using their fingerprints.
The fingerprint scanners use the “Match on Chip” (MoC) technology, which comes with internal storage and a microprocessor for data storage. This eliminates the need to store sensitive biometric information on the host machine. The communication between the operating system and the chip is encrypted, providing an extra layer of security to prevent unauthorized access by hackers.
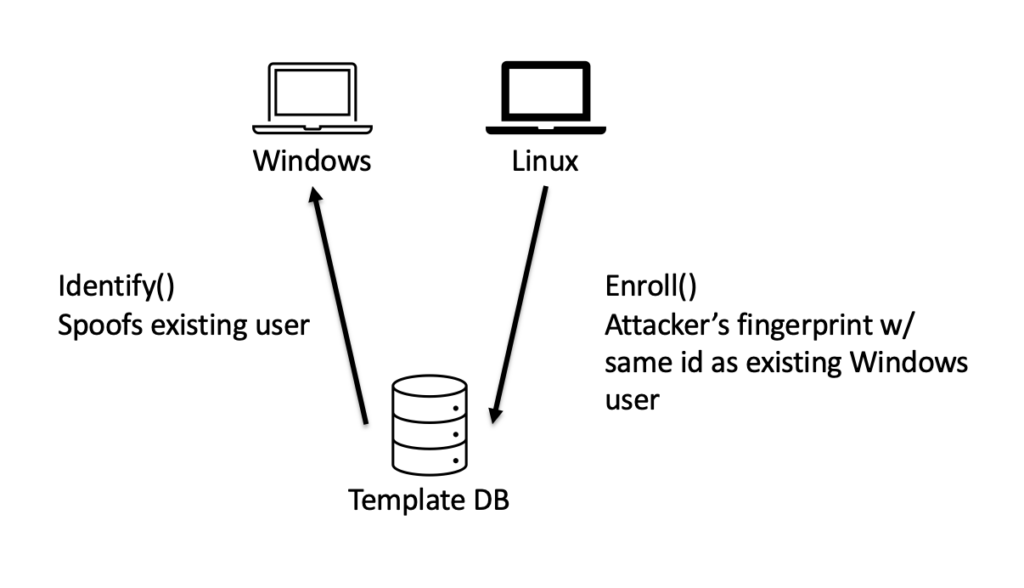
How the cybersecurity researchers hacked Windows Hello Fingerprint authentication
Security researchers from Blackwing HQ conducted penetration tests on various devices, including a Lenovo ThinkPad T14, a Dell Inspiron 15, and the Microsoft Surface Pro8/X. These devices have fingerprint sensors from Synaptics, Goodix, and ELAN, respectively.
Here’s the list of different approaches used by cybersecurity researchers to exploit flaws in the fingerprint sensors on the devices:
Dell Inspiron 15
The Dell Inspiron 15 contains a security vulnerability where its sensor stores two distinct fingerprint databases for Windows and Linux. The security flaw could let hackers manipulate a configuration packet to redirect the sensor in order to reference the Linux database instead of Windows. This technique enabled the researchers to use any fingerprint to sign into Windows machines without compromising Microsoft’s Secure Device Connection Protocol (SDCP).
Lenovo ThinkPad T14s
In the case of the Lenovo ThinkPad T14s, the researchers found that Synaptics fingerprint sensor uses an insecure custom Transport Security Layer (TLS). The sensor supports the Secure Device Connection Protocol (SDCP), though it’s disabled by default. Moreover, the client certificate and the encryption key are readable, which can be used for authentication on Windows PCs.
Microsoft Surface Pro Type Cover
Surprisingly, the Microsoft Surface Cover’s fingerprint sensor proved to be the most vulnerable to compromise. The lack of security measures between the operating system (OS) and the sensor, combined with clear text communication over USB, exposes the system to significant security risks. The researchers successfully replaced the original sensor with their own device that can masquerade as the chip. This technique can be used to log into Windows without even providing a fingerprint.
Recommendations
The Blackwing Intelligence team has urged the device manufacturers to enable Microsoft’s Secure Device Connection Protocol (SDCP) in order to ensure encrypted communication between the fingerprint sensors and Windows. The results showed that the Microsoft Surface Type Cover and the Lenovo ThinkPad T14s didn’t use SDCP at all.
“Microsoft did a good job designing SDCP to provide a secure channel between the host and biometric devices, but unfortunately device manufacturers seem to misunderstand some of the objectives. Additionally, SDCP only covers a very narrow scope of a typical device’s operation, while most devices have a sizable attack surface exposed that is not covered by SDCP at all,” the researchers wrote.
It’s important to note that Windows Hello is still considered to be a more secure option compared to password-based authentication. The security researchers confirmed that these highly specialized attacks require the attacker to have physical access to the device. This means that the likelihood of a similar attack is low unless the device is stolen.



