Windows 10 Ignoring the Hosts File for Specific Name Resolution
Ever since the beginning of Windows and the TCP/IP protocol, name resolution of computer names has been done through several methods (knowing there are NetBIOS names and DNS names, we’ll focus on DNS names in this article). Using DNS for name resolution is the common practice nowadays, but another method of manually translating names to IP addresses has been the HOSTS file (the HOSTS file is also used in Linux/Unix and Mac systems).
Modifying the HOSTS hosts file causes your computer to look directly at the IP address specified in it. This is useful, for example, when you want to test a website before going live with a public DNS name, or when you want to prevent your computer from resolving a DNS name, thus preventing it from reaching it.
The HOSTS file located in %WINDIR%\System32\drivers\etc is a simple text file (although it does NOT have a .TXT suffix), where for what seems like ages, you could add text lines such as this one:
<IP address><space><DNS name>
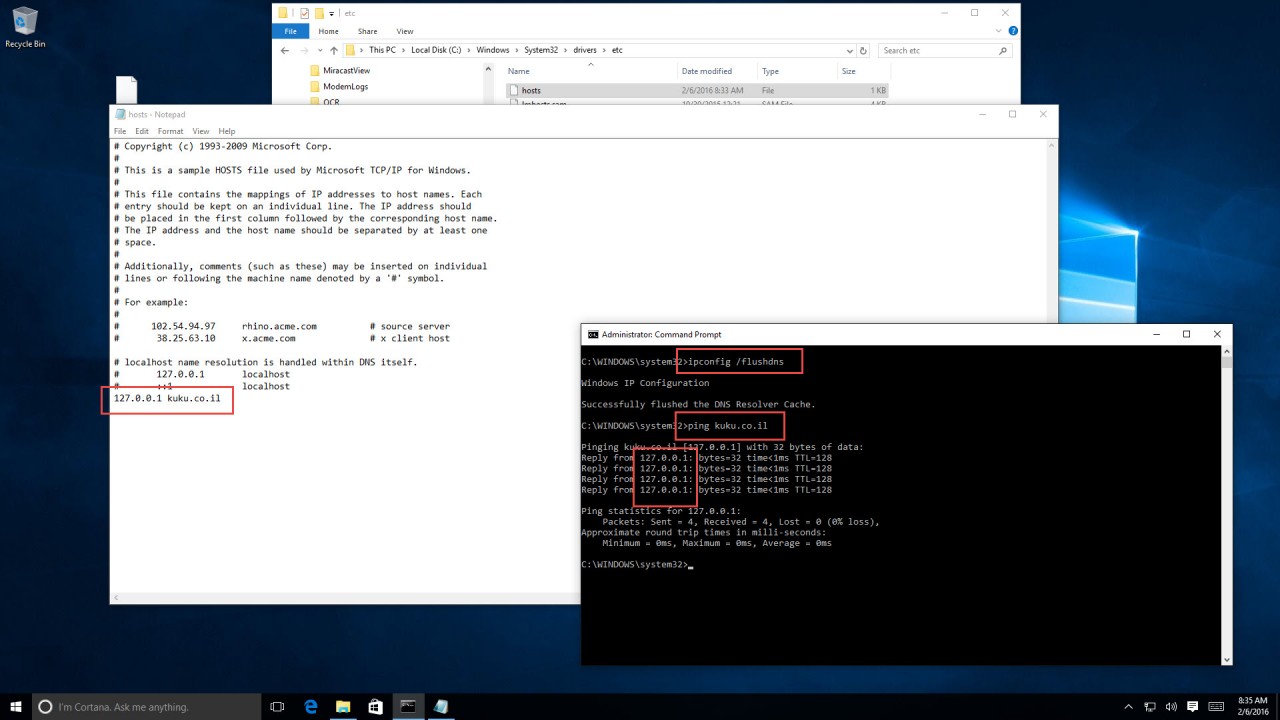
And once this was saved and name resolution cache had been cleared (run ipconfig /flushdns in a Command Prompt window), your computer would resolve the DNS name to the given IP address.
To prevent the computer from communicating to any external DNS name, add the relevant name to the HOSTS file and point it to the 127.0.0.1 IP address (which is the local host itself), or to 0.0.0.0.
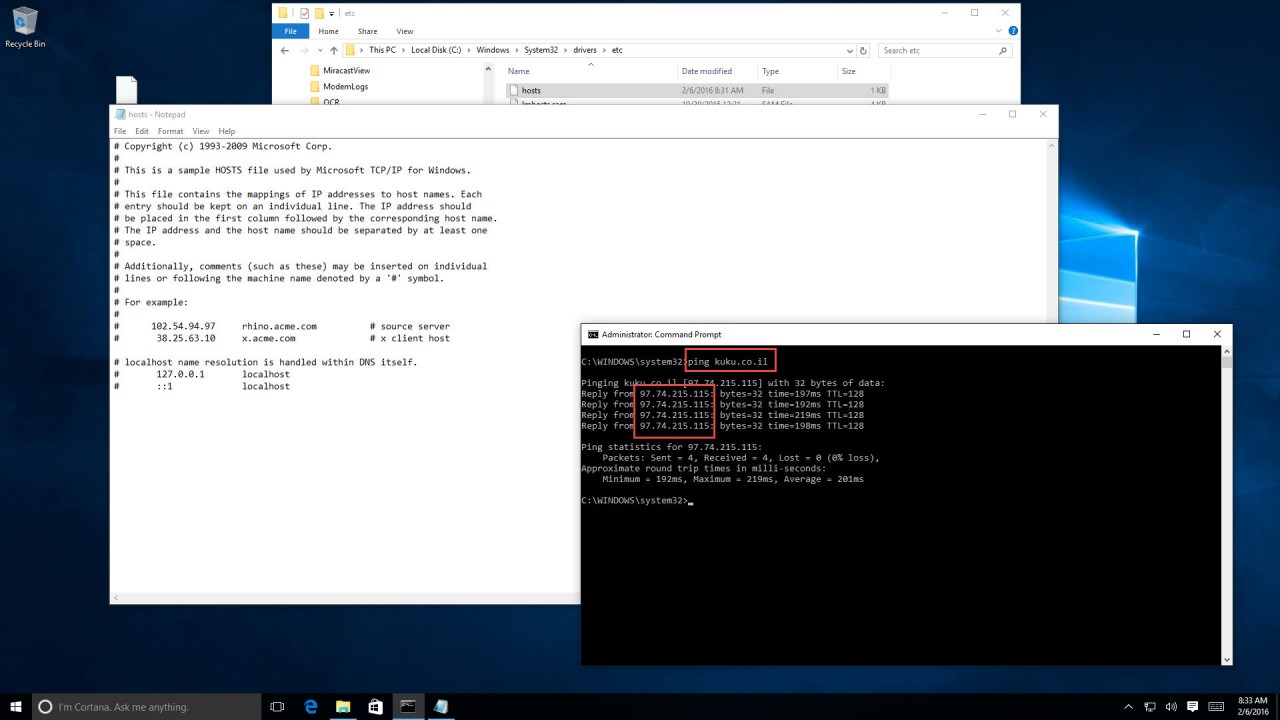
For example, adding a line to a domain name, and the subsequent PING command that follows:
While this was true for all DNS domain names, in the past several years something has changed in the way Windows translates some names. This is another one of those annoyances that can drive you crazy, trying to figure out what exactly you did wrong, where in fact it’s not a malfunction or wrong configuration: It’s not something you did wrong – it’s a built-in “feature” that was added by Microsoft a while ago (actually – in Windows XP SP2), and it’s still here in Windows 10.
These are the hardcoded DNS domain names that will resolve to their proper IP addresses regardless of what you put into the HOSTS file:
www.msdn.com
msdn.com
www.msn.com
msn.com
go.microsoft.com
msdn.microsoft.com
office.microsoft.com
microsoftupdate.microsoft.com
wustats.microsoft.com
support.microsoft.com
www.microsoft.com
microsoft.com
update.microsoft.com
download.microsoft.com
microsoftupdate.com
windowsupdate.com
windowsupdate.microsoft.com
These FDQNs are hardcoded in the following DLL:
%WINDIR%\system32\dnsapi.dll
The reason Microsoft added it is to prevent malicious software and/or people that wanted to use their computer’s HOSTS file to override some name resolution from doing so. This means that even if you edited the HOSTS file and added records to it that changed the name resolution to Microsoft’s update servers, proper name resolution would still work and the operating system would be able to go to the Microsoft update servers, allowing the OS to update itself, regardless of the changes to the HOSTS file.
Is this good or bad?
Depends on your point of view. Some may argue that if Microsoft did this, so can other companies that have their software installed on your computer: Adobe, Google, and others can be candidates (and some actually do bypass name resolution: for example, some browser makers). So today it’s Microsoft; tomorrow it can be anyone else, and soon thereafter our computer will “call home” without us being able to do anything about it. (In a way, this is exactly what’s happening now with Windows 10’s telemetry data being sent to Microsoft without us being able to really control it.)
Others may hold a different view. They claim that all Microsoft is doing is taking steps towards ensuring that users can get updates and patches to the operating system when needed, without worrying about any malicious software modifying the computers’ HOSTS file (and some do).
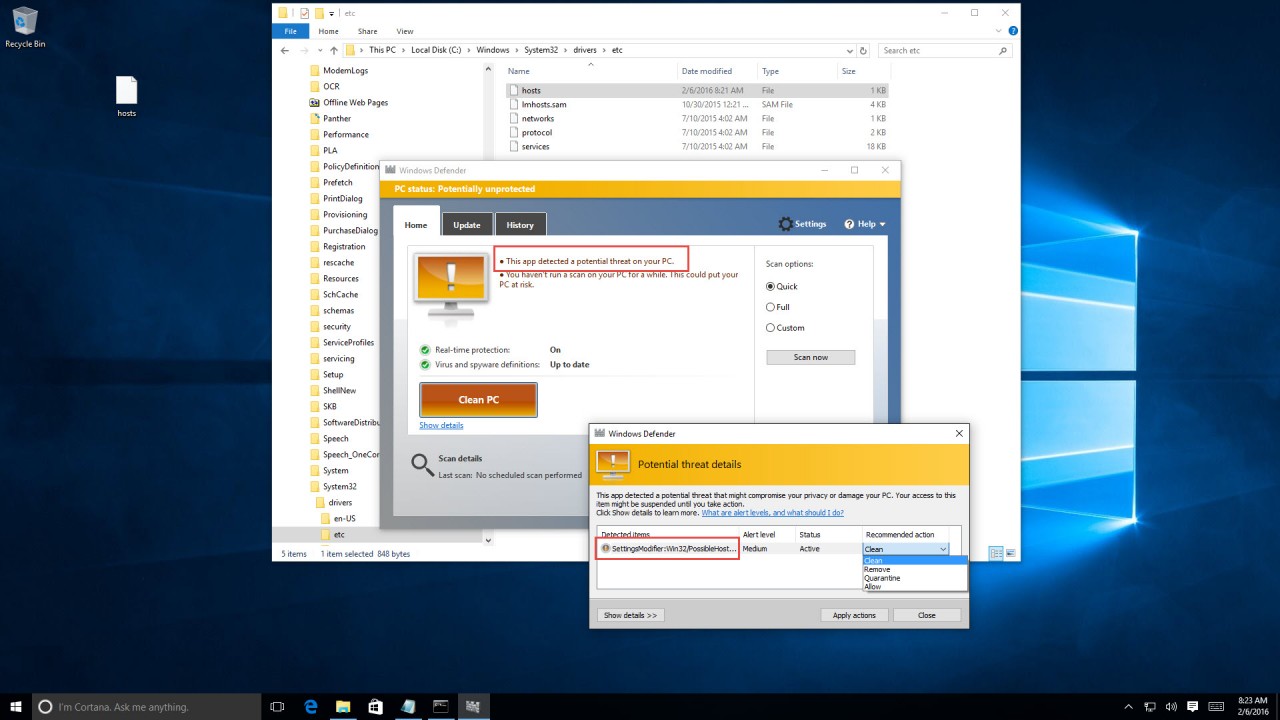
BTW, Windows 10 actually warns you when you (or a software) tries to modify the contents of the HOSTS file:
So how do you prevent Windows from “talking” to these FQDNs? One approach would be by creating Windows firewall rules for these specific (or other) domain names (another approach would be using third-party firewall products).
You can also use a third-party DNS proxy software that will replace Microsoft’s internal DNS client mechanism.
If you’re using a router/firewall to connect to the Internet, you can create blocking rules on that device, preventing your computer and any other operating system that’s connected to that network from connecting to these domain names.