
When it comes to cloud services and security technology, IT and systems administrators should seriously consider having SSO implemented for greater convenience and security.
What is single sign-on (SSO)?
SSO is an authentication method that allows users to securely access multiple SaaS (Software-as-a-Service) applications, websites, and other digital resources with a single set of login credentials. As opposed to remembering and entering separate usernames and passwords for each service, SSO enables users to authenticate themselves once and then be granted access to all authorized systems and applications. Microsoft SSO, in particular, has become a pivotal centerpiece in its evolutionary, security- and AI-led approach across its entire ecosystem.
At its core, SSO establishes a trusted relationship between a user and one or more service providers (SPs). The user is responsible for providing the credentials, the service then creates an authentication token that validates the user as verified. This token is stored either in a browser or within the SSO vendor’s servers. The SSO vendor then passes the user’s token details to any apps on the server and the user is granted access without the need to enter their details again.
SSO plays a crucial role in securely managing access and authentication across geographically distributed teams and infrastructure. It allows organizations to manage user identities and access permissions from a centralized platform, simplifying the switching between various tools and services without the need to re-authenticate, fostering more efficient and streamlined workflows. Additionally, organizations can use SSO to validate users’ attempts to access and interact with mission-critical systems and enhance their DevOps operations, with CI/CD pipelines and cloud applications proving inherently more agile with this authentication method embedded.
How does single sign-on work?
Firstly, however, it’s important to establish how SSO works in a business context. An SSO configuration setup can be viewed as a go-between that confirms whether a user’s login information matches their identity on a separately managed database. Most SSO services don’t manage databases themselves but can access them quickly to validate a login request.

The SSO process typically follows these steps:
- A user attempts to access a secure application or resource.
- The application redirects the user to the identity provider’s login page.
- The user provides their username and password to the application.
- The application establishes a secure session through identity verification.
- The resource generates an authentication token and returns it to the user’s browser.
- The user’s browser automatically includes the authentication token when accessing the original application or other connected services.
- The service provider validates the token and grants the user secure access to the requested resource(s).
Authentication tokens have specific communication standards to adhere to when confirming a request’s validity. The main token standard is known as Security Assertion Markup Language (SAML), but there are several common SSO configurations that organizations – of all sizes – can implement.
Types of SSO configurations
SAML-based SSO
SAML is an XML standard for exchanging authentication and authorization data between users and service providers. SAML-based SSO involves communication between the user, the identity provider (IdP) that oversees a user directory or database, and the service provider.
Kerberos-based SSO
Kerberos is a network authentication protocol that authenticates secure service requests between trusted hosts across non-secure networks. In a Kerberos-based SSO setup, a user initially provides their credentials before a ticket-granting ticket (TGT) is issued, which obtains service tickets for other wanted resources without the need for re-entering information.
Smart Card-based SSO
Smart card-based SSO utilizes a physical smart card or security token as the primary or initial authentication factor. Once the data from the card is used, the user does not have to re-enter their credentials, with the SSO vendor storing certificates or passwords after first entry.
Some organizations allow users to validate their access requests if they log in using their social media account credentials. This can provide a convenient login experience but it also introduces potential security risks that users should consider carefully, given that it creates a single point of failure easily exploitable by attackers.
Enterprise SSO
Enterprise single sign-on (eSSO) services usually comprise password managers with server and client components that align users and target applications with securely stored user-generated credentials.
Benefits of SSO
The enterprise SSO market is projected to reach an $11 billion valuation by 2036, expanding at a 14% CAGR from this year onwards. Given the current cyber threat landscape, it’s clear that enterprises are taking SSO seriously, and with good reason. Implementing a robust SSO solution can provide organizations with several advantages.
- Improved user experience: By removing the need for multiple login prompts and the need to remember separate passwords, SSO improves overall productivity and efficiency for users.
- Enhanced security: SSO can help IT teams strengthen security by enforcing stronger and specific password policies, multi-factor authentication (MFA), and the centralized management of user identities and access permissions.
- Reduced IT support costs: With the help of SSO, administrators spend less time implementing repeated password resets and can take advantage of a single place from which to initiate re-entry for internal applications. As such, business productivity improves and IT teams can dedicate more resources to higher-value work.
- Aiding in compliance: Many SSO solutions provide high-quality logging and reporting capabilities, which can help organizations meet regulations with greater oversight and less ambiguity.
- Scalability and flexibility: Third-party SSO platforms can be seamlessly integrated with a wide range of on-premise and cloud-based applications, making them adaptable to the evolving needs of modern organizations.
Are there any security risks of SSO?
While SSO offers several benefits, it’s important to be aware of potential security risks. If malicious actors gain access to a user’s credentials, resources connected through SSO can be potentially compromised through a single point of failure. Organizations must maintain strict controls and processes to reduce both password fatigue and an overreliance on service provider availability. To mitigate these risks, organizations should implement stringent identity and access management (IAM) practices, regular audits and 24/7 incident response.
Microsoft Entra ID SSO implementation
Microsoft Entra ID, formerly known as Azure Active Directory (Azure AD) is Microsoft’s cloud-based identity and access management service. The Microsoft Entra SSO is an incumbent feature within the Entra platform and is the primary SSO solution that permits users to use one set of credentials to access multiple Microsoft applications.
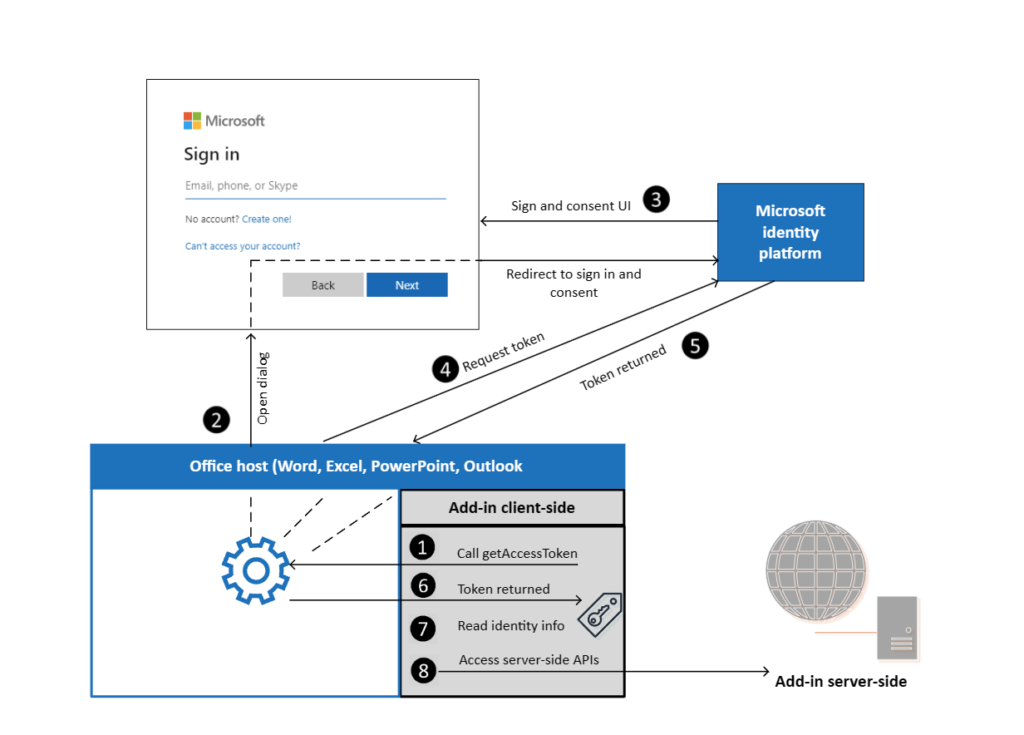
The service offers extensive support for app integrations, passwordless and multi-factor authentication and a notable conditional access functionality which allows administrators to set specific conditions that grant users access to certain applications based on location, device, and other data. This is an agile and proactive workaround for users who have lost access to or forgotten logins, while giving administrators flexibility to ensure infrastructure stability and minimize risk.
Microsoft Entra also supports all OAuth 2.0 flows, which are connected to OpenID Connect (OIDC), a proven and reliable authorization layer.
Microsoft Entra ID additionally allows users to create an application identity that can connect to other resources using Entra authentication, with it recently permitting enterprise customers to convert external accounts to internal accounts with ease. Administrators can connect many Azure resources, for example, by supporting managed user identities with the help of Entra ID, including but not limited to Azure Virtual Machines, Azure SQL, Azure IoT Hub, and Azure Communication Services, to name just a few.
As such, administrators can create a robust, comprehensive security and regulatory compliance framework for their infrastructure and processes.
It’s clear that SSO is a powerful authentication solution that simplifies user access and identity management across an organization’s Microsoft infrastructure. Using SSO is a definitive way to enhance security and productivity across your estate, and by understanding the various configurations and benefits it can provide, as well as the potential security risks, IT administrators can implement the right enterprise-grade SSO solution that aligns with their unique business needs.
Enterprises have access to a user-friendly and established SSO tool within incumbent Microsoft setups, known as Entra ID, which can be leveraged to further streamline user authentication and access management across a range of cloud-based and on-premises applications. As organizations continue to scale with the help of DevOps, the role of SSO in securely managing user identities and access becomes increasingly vital.
As security becomes more of a hot topic among IT professionals, staying informed about SSO developments will help you make more informed choices about how best to implement a well-designed and reliable SSO solution.


