Names like “Cisco” and “Checkpoint” dominate edge network security in large enterprises and clouds. Dell SonicWALL has become a dominant player in unified threat management (UTM) in the small/medium enterprise. I recently started working with the XTM appliances by WatchGuard. I knew of other names such as SonicWALL and Fortinet, but I knew nothing of this American company until last year. In this article I will share what I have learned so far about this edge security device that fits perfectly into the branch office and small/medium enterprise scenarios.
What Is Unified Threat Management?
Once upon a time, network security was all about putting a simple device on the edge network to filter unwanted incoming traffic. Threats evolved and services were created. Malware started to spread via broadcasts on the Internet, drive-by, and waterhole attacks. Companies need to control access to Internet content, secure company intellectual property, and protect customer personal data. Internet threat management needs to do more:
- Firewall: A hardware or software appliance provided network filtering on the Internet connection to keep the bad stuff out and the good stuff in.
- Application control: Restrict unwanted applications to selected users or time windows. For example, you might limit access to streaming media to lunch breaks and the hour after the workday ends.
- URL filtering: One of the most popular features in Internet security is the ability to restrict access to undesirable web content, such as pornography, gambling, or even any nonwork-related materials.
- Anti-spam: If you are one of the businesses that still operates on-premise email servers then you will want a solution for dealing with spam.
- Gateway antivirus: Malware can still spread via removable storage (see Conficker), but the easiest way for an attacker to spread or target their threats is to do so online. This can be via bad websites, hacked sites, or even legitimate sites that are accidentally sharing adverts that contain malware. A gateway antivirus solution provides your first line of defense against malware, supplemented by the security that you continue to run on your PCs and any servers that you might run.
- Intrusion Protection Services (IPS): This is a form of traffic inspection that scans permitted protocols and blocks suspicious behavior, such as a denial of service attack.
- Data Loss Prevention (DLP): The most overlooked threat to a business are the employees. Can you trust telesales employees with customers’ credit card or social security information? Could sales staff move to a competitor after sending sensitive product or contact information to their new email account?
Five years ago, it wasn’t uncommon to see multiple servers or virtual machines, each running a point solution to provide the above security services. This allows large businesses to avail of best-of-breed services. But there are downsides:
- Increased management costs: Using services from lots of different vendors means you have more points of administration, no native integration, difficult (if not impossible) automation, and a higher total cost of ownership.
- Restricted market opportunity: Small and medium enterprises (SMEs) cannot afford to run such a wide array of point solutions. When you take the community view, any threats that attack SMEs will also attack larger enterprises.
A number of appliance manufacturers, including Fortinet and Dell SonicWALL created a solution known as unified threat management (UTM) to provide a combined solution. UTM appliances target markets varying from the small office/home office (SOHO) to the large enterprise, with the promise of a bundled solution that simplifies security, and reduces costs and complexity. I was recently introduced to WatchGuard, a longtime player in the UTM market, and was educated on the capabilities of their XTM series of devices.
WatchGuard XTM
WatchGuard’s strategy for building a UTM gave them a unique selling point. Instead of trying to develop their own expertise in anti-malware, URL filtering, DLP, and so on, they focused on the firewall, integration, and management of the UTM appliance.
WatchGuard includes best-of-breed products from the likes of WebSense, Cyren (formerly CommTouch), AVG, Kaspersky, Trend Micro, and Sophos. Olympians are experts. A decathlete might be a good 100-meter sprinter, but he or she will never be as good as the athlete who focuses every day of his or her life at perfecting the sprint. The same holds true for Internet security: Networking companies can acquire and develop skills, and with time, they might offer fine services, but they will never be best of breed.
WatchGuard’s approach is unique in the UTM market. I will admit that I looked at their product range, branded as XTM, over a year ago. I read some documentation and it both confused and scared me. It was only recently when I revisited the products with current documentation that I realized everything I had read previously was out of date and no longer applicable. The XTM range of products varies from appliances for the SOHO up to solutions for large enterprise headquarters and data centers. The beauty of the solution is that you get a UTM appliance for the scale that suits your business or location, and that solution doesn’t change much as you move through the series. The security features offered from the XTM 2 Series that is intended for small offices are the same those offered by the enterprise-level XTM 1500 series; the only differences are related to the need to scale out networking capacity and services.
Ease of Use
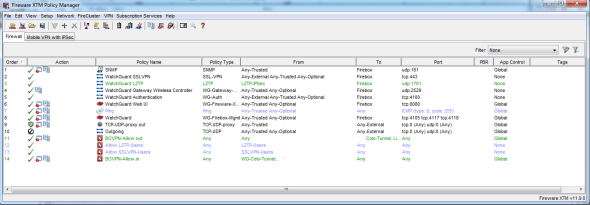
My biggest concern with the XTM was complexity. The outdated information I had previously read implied that there were lots of subsystems that required multiple seoiAZOP3 rvers and administration tools to manage the appliance’s security services. An XTM 25 was set up in our office at work and my fears were put to rest. One GUI tool, the Fireware XTM Policy Manager, was installed on a laptop and that gave us complete administration control over every one of the security services, no command prompts required.
Every one of the UTM services is easy to enable and configure, and I like WatchGuard’s approach to using services from established players in their respective fields. Installation and maintenance should be a breeze; this is of huge importance in one market that I see as being very important.
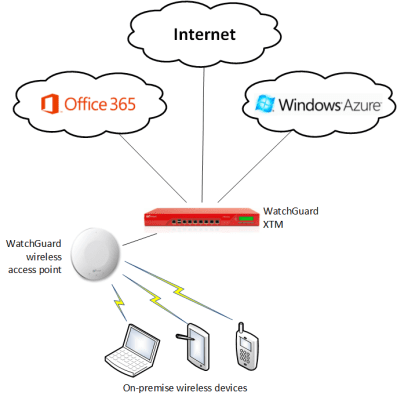
Small businesses that used to run one or a handful of servers are rapidly moving to cloud services such as Office 365. Those Windows Server 2003 or Small Business Server machines are being deprecated. Those customers now need reliable and secure Internet connectivity. One downside to the XTM is that it is not an Internet router, but that’s not a big deal – simply place the XTM behind the router that is already there, enable the router to forward all traffic to the XTM, and let the appliance do the heavy lifting. The customer can enable anti-virus, URL filtering, and whatever other services that they need in addition to the firewall and VPN (yes it offers remote client connectivity over SSL and IPsec VPN too). Don’t worry if you’re in a medium or large business and would like cloud services. The WatchGuard XTM is also one of the site-site VPN solutions that you can use to connect securely to Windows Azure networking. You can secure your edge network, manage software threats, and build a hybrid cloud with one of these small red boxes.
No Shortage of Information
Whether you want a quick look-see, do some troubleshooting, or get a historical view of activity, the WatchGuard XTM can do it for you. Using the admin tool, you can browse through graphical representations of the appliance’s ports, see live logging of network activity, see bandwidth utilization, and more. A web portal that runs in the XTM’s system allows you to drill down into the current data so you can see a bit more. If you need to generate reports or audit usage then you have a few important options. An optional virtual appliance called Dimension can be used to archive reporting data. This virtual appliance gives auditors and security officers visibility into how bandwidth is being used. This sort of data is considered sensitive in some countries because of employee rights. The Dimension restricts access to the data and can even anonymize it.
Connectivity and Fault Tolerance
Internet connectivity is mission critical for many businesses. The XTM can be clustered and can be connected to multiple Internet connections. In my early conversations with customers about the WatchGuard XTM, one of the add-ons has proven to be very interesting. WatchGuard also make a range of wireless access points (WAPs) to be used with the UTM appliance. At work, we’ve had serious problems with wireless networking due to the construction of our building. That’s a bit of an issue in an electronics distribution company where everyone has a PC, at least one smartphone, and access to a wide variety of laptops and tablets (company and personal). We tested out an XTM 25 with one of the single antenna (hang from the wall or a ceiling) WAPs and we had a signal throughout the building. I’d love to see how the dual-antenna model (hang above the ceiling tiles) would work! This solution will be superb in steel-heavy buildings like ours and in older stone buildings that are to be found in northeast United States and all around Europe where building regulations restrict wired networking and the walls are blocking wireless signals.
Rating the WatchGuard XTM
To be very clear, my firm recently started to distribute the product range from WatchGuard in the Irish market. I wasn’t an early believer, but tech firms that I respect were. I’ve learned more about the appliance, and now I am on board. We don’t necessarily use a product ourselves if we distribute it; we can believe in the product, but we’re not going to rip out something that we’ve already paid for and is working. We recently renewed the support for our edge firewall (one of the big names), but the demonstration of wireless connectivity gave our decision makers an easy choice: We finally could connect the entire building and wouldn’t have to apologize to visitors for the lack of connectivity in meeting rooms. We’re putting in an XTM with a couple of WAPs (just to be safe) and the old firewall will be recycled.
Another benefit is that our part-time IT will be able to manage the XTM via the easy-to-use UI, whereas we have to bring in someone to manage the legacy firewall via its 1970s interface. We will also avail of some of the security features to protect the business. I really do like the strategy of partnering with established experts, instead of trying to reinvent the wheel… badly. I’ve used bad malware and URL filtering solutions, and I’ve used good ones. There is a world of difference, and that varies from protection from threats to always finding yourself trying to recover from failure; I’d rather work with the best. So you can take it with a grain of salt, considering that my employers do sell these appliances, but I’ve hopped on the WatchGuard bandwagon.