In this Ask the Admin, I’ll explain how to resolve an RDP error that might appear after the May 2018 cumulative updates.
If you’ve had trouble logging in to remote Windows servers using Remote Desktop Protocol (RDP) recently, you are not alone. I started noticing an error last month when logging into Azure VMs running Windows Server. Because I use Windows Server VMs for testing, it isn’t updated with the latest Windows patches on a regular basis. The Windows PC from which I connect, on the other hand, is patched as soon updates are available on Windows Update. This disparity in patch level between client and server doesn’t usually cause a problem but can sometimes lead to issues.
Microsoft fixed a remote code execution vulnerability in CredSSP in the March updates for Windows. The Credential Security Support Provider protocol (CredSSP) is a Security Support Provider that lets applications delegate user’s NTLM or Kerberos credentials from clients to servers for remote authentication over an encrypted Transport Layer Security (TLS) channel.
The vulnerability could allow a man-in-the-middle attack where user credentials are relayed and used to run code on the remote system. Microsoft outlined an example where an attacker could perform a man-in-the-middle attack against an RDP session, enabling them to install programs, view, change, or delete data, and create new user accounts.
Patch One, Two, Three
The first patch that Microsoft released in March updates CredSSP authentication and RDP clients for all supported platforms. It also required IT to update the Encryption Oracle Remediation Group Policy setting to ‘Force updated clients’ or ‘Mitigated’ on both client and server computers to receive full protection against the vulnerability. You can find the Encryption Oracle Remediation setting in Group Policy under Computer Configuration > Administrative Templates > System > Credentials Delegation.
In April, another patch was released to improve the error message that users see when RDP clients can’t connect to a server. Then in May, in another update, Microsoft changed the default Encryption Oracle Remediation Group Policy setting from ‘Vulnerable’ to ‘Mitigated’, meaning that patched clients could no longer connect to unpatched servers.
Getting a Connection
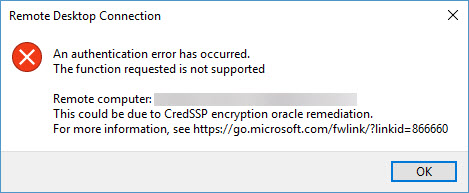
The simplest way to remediate this issue is to make sure that both clients and servers have the latest patches from Microsoft. If there’s a mismatch, you’ll likely see the error in the screenshot above when trying to establish an RDP session.
If for whatever reason you are not able to patch your servers, or vice versa cannot patch your clients, Microsoft has published two workarounds to address both scenarios here.
In this Ask the Admin, I explained why Microsoft has patched CredSSP in Windows and where to find information about establishing RDP connections to unpatched servers or from unpatched clients.
Follow Russell on Twitter @smithrussell.
Related Article: